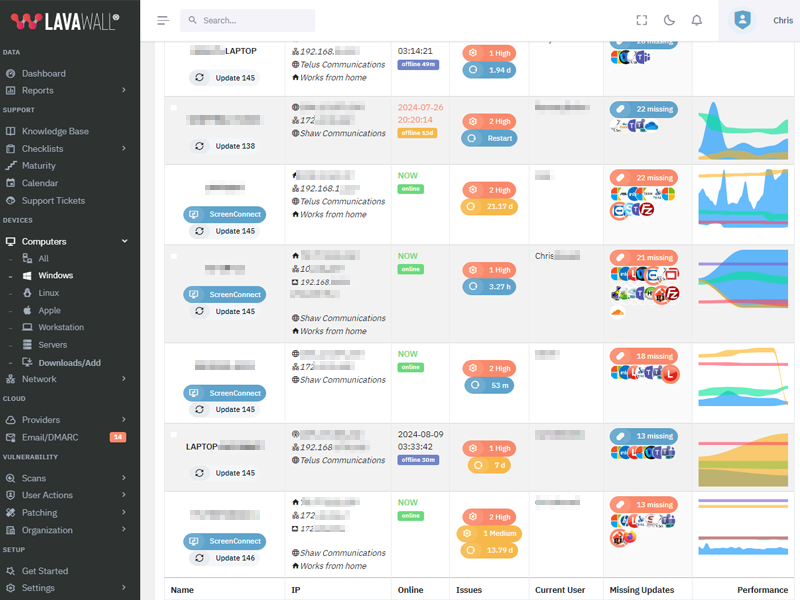
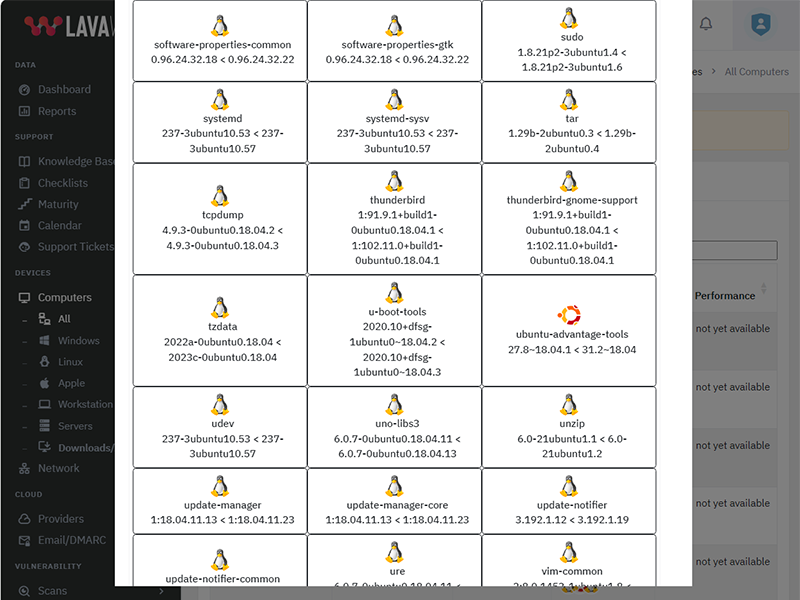
Update Wireshark to version 4.6.3
What patches are you missing?
CVE Vulnerabilities for Wireshark
| CVE | Published | Severity | Details | Exploitability | Impact | Vector |
| CVE‑2025‑9817 | 2025‑09‑03 08:15:32 | HIGH (8) | SSH dissector crash in Wireshark 4.4.0 to 4.4.8 allows denial of service | 2 | 6 | LOCAL |
| CVE‑2025‑5601 | 2025‑06‑04 11:15:22 | HIGH (8) | Column handling crashes in Wireshark 4.4.0 to 4.4.6 and 4.2.0 to 4.2.12 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2025‑1492 | 2025‑02‑20 02:15:39 | HIGH (8) | Bundle Protocol and CBOR dissector crashes in Wireshark 4.4.0 to 4.4.3 and 4.2.0 to 4.2.10 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑9781 | 2024‑10‑10 07:15:04 | HIGH (8) | AppleTalk and RELOAD Framing dissector crash in Wireshark 4.4.0 and 4.2.0 to 4.2.7 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑9780 | 2024‑10‑10 07:15:04 | MEDIUM (6) | ITS dissector crash in Wireshark 4.4.0 allows denial of service via packet injection or crafted capture file | 2 | 4 | LOCAL |
| CVE‑2024‑8645 | 2024‑09‑10 10:15:14 | MEDIUM (6) | SPRT dissector crash in Wireshark 4.2.0 to 4.0.5 and 4.0.0 to 4.0.15 allows denial of service via packet injection or crafted capture file | 2 | 4 | LOCAL |
| CVE‑2024‑8250 | 2024‑08‑29 00:15:09 | HIGH (8) | NTLMSSP dissector crash in Wireshark 4.2.0 to 4.0.6 and 4.0.0 to 4.0.16 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑4854 | 2024‑05‑14 15:45:19 | MEDIUM (6) | MONGO and ZigBee TLV dissector infinite loops in Wireshark 4.2.0 to 4.2.4, 4.0.0 to 4.0.14, and 3.6.0 to 3.6.22 allow denial of service via packet injection or crafted capture file | 2 | 5 | NETWORK |
| CVE‑2024‑2955 | 2024‑03‑26 20:15:12 | HIGH (8) | T.38 dissector crash in Wireshark 4.2.0 to 4.0.3 and 4.0.0 to 4.0.13 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑24479 | 2024‑02‑21 19:15:09 | HIGH (8) | A Buffer Overflow in Wireshark before 4.2.0 allows a remote attacker to cause a denial of service via the wsutil/to_str.c, and format_fractional_part_nsecs components. NOTE: this is disputed by the vendor because neither release 4.2.0 nor any other release was affected. | 4 | 4 | NETWORK |
| CVE‑2024‑24478 | 2024‑02‑21 17:15:10 | HIGH (8) | An issue in Wireshark before 4.2.0 allows a remote attacker to cause a denial of service via the packet-bgp.c, dissect_bgp_open(tvbuff_t*tvb, proto_tree*tree, packet_info*pinfo), optlen components. NOTE: this is disputed by the vendor because neither release 4.2.0 nor any other release was affected. | 4 | 4 | NETWORK |
| CVE‑2024‑24476 | 2024‑02‑21 19:15:09 | HIGH (8) | A buffer overflow in Wireshark before 4.2.0 allows a remote attacker to cause a denial of service via the pan/addr_resolv.c, and ws_manuf_lookup_str(), size components. NOTE: this is disputed by the vendor because neither release 4.2.0 nor any other release was affected. | 4 | 4 | NETWORK |
| CVE‑2024‑11596 | 2024‑11‑21 11:15:33 | HIGH (8) | ECMP dissector crash in Wireshark 4.4.0 to 4.4.1 and 4.2.0 to 4.2.8 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑11595 | 2024‑11‑21 11:15:33 | HIGH (8) | FiveCo RAP dissector infinite loop in Wireshark 4.4.0 to 4.4.1 and 4.2.0 to 4.2.8 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑0211 | 2024‑01‑03 08:15:11 | HIGH (8) | DOCSIS dissector crash in Wireshark 4.2.0 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑0210 | 2024‑01‑03 08:15:11 | HIGH (8) | Zigbee TLV dissector crash in Wireshark 4.2.0 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2024‑0209 | 2024‑01‑03 08:15:11 | HIGH (8) | IEEE 1609.2 dissector crash in Wireshark 4.2.0, 4.0.0 to 4.0.11, and 3.6.0 to 3.6.19 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2024‑0208 | 2024‑01‑03 08:15:10 | HIGH (8) | GVCP dissector crash in Wireshark 4.2.0, 4.0.0 to 4.0.11, and 3.6.0 to 3.6.19 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2024‑0207 | 2024‑01‑03 08:15:10 | HIGH (8) | HTTP3 dissector crash in Wireshark 4.2.0 allows denial of service via packet injection or crafted capture file | 2 | 6 | LOCAL |
| CVE‑2023‑6175 | 2024‑03‑26 08:15:36 | HIGH (8) | NetScreen file parser crash in Wireshark 4.0.0 to 4.0.10 and 3.6.0 to 3.6.18 allows denial of service via crafted capture file | 2 | 6 | LOCAL |
| CVE‑2023‑6174 | 2023‑11‑16 12:15:07 | MEDIUM (6) | SSH dissector crash in Wireshark 4.0.0 to 4.0.10 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑5371 | 2023‑10‑04 17:15:10 | MEDIUM (5) | RTPS dissector memory leak in Wireshark 4.0.0 to 4.0.8 and 3.6.0 to 3.6.16 allows denial of service via packet injection or crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑4513 | 2023‑08‑24 07:15:12 | HIGH (8) | BT SDP dissector memory leak in Wireshark 4.0.0 to 4.0.7 and 3.6.0 to 3.6.15 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2023‑4512 | 2023‑08‑24 07:15:12 | MEDIUM (5) | CBOR dissector crash in Wireshark 4.0.0 to 4.0.6 allows denial of service via packet injection or crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑4511 | 2023‑08‑24 07:15:12 | MEDIUM (5) | BT SDP dissector infinite loop in Wireshark 4.0.0 to 4.0.7 and 3.6.0 to 3.6.15 allows denial of service via packet injection or crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑3649 | 2023‑07‑14 07:15:09 | MEDIUM (5) | iSCSI dissector crash in Wireshark 4.0.0 to 4.0.6 allows denial of service via packet injection or crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑3648 | 2023‑07‑14 07:15:08 | MEDIUM (5) | Kafka dissector crash in Wireshark 4.0.0 to 4.0.6 and 3.6.0 to 3.6.14 allows denial of service via packet injection or crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑2952 | 2023‑05‑30 23:15:10 | MEDIUM (5) | XRA dissector infinite loop in Wireshark 4.0.0 to 4.0.5 and 3.6.0 to 3.6.13 allows denial of service via packet injection or crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑2906 | 2023‑08‑25 21:15:08 | MEDIUM (7) | Due to a failure in validating the length provided by an attacker-crafted CP2179 packet, Wireshark versions 2.0.0 through 4.0.7 is susceptible to a divide by zero allowing for a denial of service attack. | 3 | 4 | NETWORK |
| CVE‑2023‑2879 | 2023‑05‑26 21:15:19 | MEDIUM (6) | GDSDB infinite loop in Wireshark 4.0.0 to 4.0.5 and 3.6.0 to 3.6.13 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑2858 | 2023‑05‑26 21:15:19 | MEDIUM (7) | NetScaler file parser crash in Wireshark 4.0.0 to 4.0.5 and 3.6.0 to 3.6.13 allows denial of service via crafted capture file | 3 | 4 | NETWORK |
| CVE‑2023‑2857 | 2023‑05‑26 21:15:18 | MEDIUM (7) | BLF file parser crash in Wireshark 4.0.0 to 4.0.5 and 3.6.0 to 3.6.13 allows denial of service via crafted capture file | 3 | 4 | NETWORK |
| CVE‑2023‑2856 | 2023‑05‑26 21:15:18 | MEDIUM (7) | VMS TCPIPtrace file parser crash in Wireshark 4.0.0 to 4.0.5 and 3.6.0 to 3.6.13 allows denial of service via crafted capture file | 3 | 4 | NETWORK |
| CVE‑2023‑2855 | 2023‑05‑26 21:15:18 | MEDIUM (5) | Candump log parser crash in Wireshark 4.0.0 to 4.0.5 and 3.6.0 to 3.6.13 allows denial of service via crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑2854 | 2023‑05‑26 21:15:18 | MEDIUM (5) | BLF file parser crash in Wireshark 4.0.0 to 4.0.5 and 3.6.0 to 3.6.13 allows denial of service via crafted capture file | 2 | 3 | LOCAL |
| CVE‑2023‑1994 | 2023‑04‑12 22:15:14 | MEDIUM (6) | GQUIC dissector crash in Wireshark 4.0.0 to 4.0.4 and 3.6.0 to 3.6.12 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑1993 | 2023‑04‑12 21:15:16 | MEDIUM (6) | LISP dissector large loop in Wireshark 4.0.0 to 4.0.4 and 3.6.0 to 3.6.12 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑1992 | 2023‑04‑12 21:15:15 | MEDIUM (6) | RPCoRDMA dissector crash in Wireshark 4.0.0 to 4.0.4 and 3.6.0 to 3.6.12 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑1161 | 2023‑03‑06 21:15:11 | HIGH (7) | ISO 15765 and ISO 10681 dissector crash in Wireshark 4.0.0 to 4.0.3 and 3.6.0 to 3.6.11 allows denial of service via packet injection or crafted capture file | 3 | 4 | NETWORK |
| CVE‑2023‑0668 | 2023‑06‑07 03:15:09 | MEDIUM (7) | Due to failure in validating the length provided by an attacker-crafted IEEE-C37.118 packet, Wireshark version 4.0.5 and prior, by default, is susceptible to a heap-based buffer overflow, and possibly code execution in the context of the process running Wireshark. | 3 | 4 | NETWORK |
| CVE‑2023‑0667 | 2023‑06‑07 03:15:09 | MEDIUM (7) | Due to failure in validating the length provided by an attacker-crafted MSMMS packet, Wireshark version 4.0.5 and prior, in an unusual configuration, is susceptible to a heap-based buffer overflow, and possibly code execution in the context of the process running Wireshark | 3 | 4 | NETWORK |
| CVE‑2023‑0666 | 2023‑06‑07 03:15:09 | MEDIUM (7) | Due to failure in validating the length provided by an attacker-crafted RTPS packet, Wireshark version 4.0.5 and prior, by default, is susceptible to a heap-based buffer overflow, and possibly code execution in the context of the process running Wireshark. | 3 | 4 | NETWORK |
| CVE‑2023‑0417 | 2023‑01‑26 21:18:08 | MEDIUM (7) | Memory leak in the NFS dissector in Wireshark 4.0.0 to 4.0.2 and 3.6.0 to 3.6.10 and allows denial of service via packet injection or crafted capture file | 3 | 4 | NETWORK |
| CVE‑2023‑0416 | 2023‑01‑26 21:18:08 | MEDIUM (6) | GNW dissector crash in Wireshark 4.0.0 to 4.0.2 and 3.6.0 to 3.6.10 and allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑0415 | 2023‑01‑26 21:18:08 | MEDIUM (7) | iSCSI dissector crash in Wireshark 4.0.0 to 4.0.2 and 3.6.0 to 3.6.10 and allows denial of service via packet injection or crafted capture file | 3 | 4 | NETWORK |
| CVE‑2023‑0414 | 2023‑01‑26 21:18:08 | MEDIUM (6) | Crash in the EAP dissector in Wireshark 4.0.0 to 4.0.2 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑0413 | 2023‑01‑26 21:18:08 | MEDIUM (6) | Dissection engine bug in Wireshark 4.0.0 to 4.0.2 and 3.6.0 to 3.6.10 and allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑0412 | 2023‑01‑26 21:18:08 | MEDIUM (6) | TIPC dissector crash in Wireshark 4.0.0 to 4.0.2 and 3.6.0 to 3.6.10 and allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2023‑0411 | 2023‑01‑26 21:18:08 | MEDIUM (6) | Excessive loops in multiple dissectors in Wireshark 4.0.0 to 4.0.2 and 3.6.0 to 3.6.10 and allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2022‑4345 | 2023‑01‑12 04:15:11 | MEDIUM (6) | Infinite loops in the BPv6, OpenFlow, and Kafka protocol dissectors in Wireshark 4.0.0 to 4.0.1 and 3.6.0 to 3.6.9 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2022‑4344 | 2023‑01‑12 00:15:09 | MEDIUM (4) | Memory exhaustion in the Kafka protocol dissector in Wireshark 4.0.0 to 4.0.1 and 3.6.0 to 3.6.9 allows denial of service via packet injection or crafted capture file | 3 | 1 | NETWORK |
| CVE‑2022‑3725 | 2022‑10‑27 17:15:10 | MEDIUM (6) | Crash in the OPUS protocol dissector in Wireshark 3.6.0 to 3.6.8 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2022‑3724 | 2022‑12‑09 18:15:20 | HIGH (8) | Crash in the USB HID protocol dissector in Wireshark 3.6.0 to 3.6.8 allows denial of service via packet injection or crafted capture file on Windows | 4 | 4 | NETWORK |
| CVE‑2022‑3190 | 2022‑09‑13 15:15:09 | MEDIUM (6) | Infinite loop in the F5 Ethernet Trailer protocol dissector in Wireshark 3.6.0 to 3.6.7 and 3.4.0 to 3.4.15 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2022‑0586 | 2022‑02‑14 22:15:08 | HIGH (8) | Infinite loop in RTMPT protocol dissector in Wireshark 3.6.0 to 3.6.1 and 3.4.0 to 3.4.11 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2022‑0585 | 2022‑02‑18 18:15:12 | MEDIUM (4) | Large loops in multiple protocol dissectors in Wireshark 3.6.0 to 3.6.1 and 3.4.0 to 3.4.11 allow denial of service via packet injection or crafted capture file | 3 | 1 | NETWORK |
| CVE‑2022‑0583 | 2022‑02‑14 22:15:08 | MEDIUM (6) | Crash in the PVFS protocol dissector in Wireshark 3.6.0 to 3.6.1 and 3.4.0 to 3.4.11 allows denial of service via packet injection or crafted capture file | 3 | 3 | NETWORK |
| CVE‑2022‑0582 | 2022‑02‑14 22:15:08 | CRITICAL (10) | Unaligned access in the CSN.1 protocol dissector in Wireshark 3.6.0 to 3.6.1 and 3.4.0 to 3.4.11 allows denial of service via packet injection or crafted capture file | 4 | 6 | NETWORK |
| CVE‑2022‑0581 | 2022‑02‑14 22:15:08 | HIGH (8) | Crash in the CMS protocol dissector in Wireshark 3.6.0 to 3.6.1 and 3.4.0 to 3.4.11 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑4190 | 2021‑12‑30 22:15:10 | HIGH (8) | Large loop in the Kafka dissector in Wireshark 3.6.0 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑4186 | 2021‑12‑30 22:15:10 | HIGH (8) | Crash in the Gryphon dissector in Wireshark 3.4.0 to 3.4.10 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑4185 | 2021‑12‑30 22:15:10 | HIGH (8) | Infinite loop in the RTMPT dissector in Wireshark 3.6.0 and 3.4.0 to 3.4.10 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑4184 | 2021‑12‑30 22:15:10 | HIGH (8) | Infinite loop in the BitTorrent DHT dissector in Wireshark 3.6.0 and 3.4.0 to 3.4.10 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑4183 | 2021‑12‑30 22:15:10 | MEDIUM (6) | Crash in the pcapng file parser in Wireshark 3.6.0 allows denial of service via crafted capture file | 2 | 4 | LOCAL |
| CVE‑2021‑4182 | 2021‑12‑30 22:15:10 | HIGH (8) | Crash in the RFC 7468 dissector in Wireshark 3.6.0 and 3.4.0 to 3.4.10 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑4181 | 2021‑12‑30 22:15:10 | HIGH (8) | Crash in the Sysdig Event dissector in Wireshark 3.6.0 and 3.4.0 to 3.4.10 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39929 | 2021‑11‑19 17:15:09 | HIGH (8) | Uncontrolled Recursion in the Bluetooth DHT dissector in Wireshark 3.4.0 to 3.4.9 and 3.2.0 to 3.2.17 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39928 | 2021‑11‑18 19:15:08 | HIGH (8) | NULL pointer exception in the IEEE 802.11 dissector in Wireshark 3.4.0 to 3.4.9 and 3.2.0 to 3.2.17 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39926 | 2021‑11‑19 17:15:09 | HIGH (8) | Buffer overflow in the Bluetooth HCI_ISO dissector in Wireshark 3.4.0 to 3.4.9 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39925 | 2021‑11‑19 17:15:09 | HIGH (8) | Buffer overflow in the Bluetooth SDP dissector in Wireshark 3.4.0 to 3.4.9 and 3.2.0 to 3.2.17 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39924 | 2021‑11‑19 17:15:09 | HIGH (8) | Large loop in the Bluetooth DHT dissector in Wireshark 3.4.0 to 3.4.9 and 3.2.0 to 3.2.17 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39923 | 2021‑11‑19 17:15:08 | HIGH (8) | Large loop in the PNRP dissector in Wireshark 3.4.0 to 3.4.9 and 3.2.0 to 3.2.17 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39922 | 2021‑11‑19 17:15:08 | HIGH (8) | Buffer overflow in the C12.22 dissector in Wireshark 3.4.0 to 3.4.9 and 3.2.0 to 3.2.17 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39921 | 2021‑11‑19 17:15:08 | HIGH (8) | NULL pointer exception in the Modbus dissector in Wireshark 3.4.0 to 3.4.9 and 3.2.0 to 3.2.17 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑39920 | 2021‑11‑18 19:15:08 | HIGH (8) | NULL pointer exception in the IPPUSB dissector in Wireshark 3.4.0 to 3.4.9 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑22235 | 2021‑07‑20 12:15:08 | HIGH (8) | Crash in DNP dissector in Wireshark 3.4.0 to 3.4.6 and 3.2.0 to 3.2.14 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑22222 | 2021‑06‑07 13:15:08 | HIGH (8) | Infinite loop in DVB-S2-BB dissector in Wireshark 3.4.0 to 3.4.5 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2021‑22207 | 2021‑04‑23 18:15:08 | MEDIUM (7) | Excessive memory consumption in MS-WSP dissector in Wireshark 3.4.0 to 3.4.4 and 3.2.0 to 3.2.12 allows denial of service via packet injection or crafted capture file | 3 | 4 | NETWORK |
| CVE‑2021‑22191 | 2021‑03‑15 18:15:18 | HIGH (9) | Improper URL handling in Wireshark 3.4.0 to 3.4.3 and 3.2.0 to 3.2.11 could allow remote code execution via via packet injection or crafted capture file. | 3 | 6 | NETWORK |
| CVE‑2021‑22174 | 2021‑02‑17 15:15:13 | LOW (4) | Crash in USB HID dissector in Wireshark 3.4.0 to 3.4.2 allows denial of service via packet injection or crafted capture file | 2 | 1 | NETWORK |
| CVE‑2021‑22173 | 2021‑02‑17 15:15:13 | HIGH (8) | Memory leak in USB HID dissector in Wireshark 3.4.0 to 3.4.2 allows denial of service via packet injection or crafted capture file | 4 | 4 | NETWORK |
| CVE‑2020‑9431 | 2020‑02‑27 23:15:13 | HIGH (8) | In Wireshark 3.2.0 to 3.2.1, 3.0.0 to 3.0.8, and 2.6.0 to 2.6.14, the LTE RRC dissector could leak memory. This was addressed in epan/dissectors/packet-lte-rrc.c by adjusting certain append operations. | 4 | 4 | NETWORK |
| CVE‑2020‑9430 | 2020‑02‑27 23:15:13 | HIGH (8) | In Wireshark 3.2.0 to 3.2.1, 3.0.0 to 3.0.8, and 2.6.0 to 2.6.14, the WiMax DLMAP dissector could crash. This was addressed in plugins/epan/wimax/msg_dlmap.c by validating a length field. | 4 | 4 | NETWORK |
| CVE‑2020‑9429 | 2020‑02‑27 23:15:13 | HIGH (8) | In Wireshark 3.2.0 to 3.2.1, the WireGuard dissector could crash. This was addressed in epan/dissectors/packet-wireguard.c by handling the situation where a certain data structure intentionally has a NULL value. | 4 | 4 | NETWORK |
| CVE‑2020‑9428 | 2020‑02‑27 23:15:13 | HIGH (8) | In Wireshark 3.2.0 to 3.2.1, 3.0.0 to 3.0.8, and 2.6.0 to 2.6.14, the EAP dissector could crash. This was addressed in epan/dissectors/packet-eap.c by using more careful sscanf parsing. | 4 | 4 | NETWORK |
| CVE‑2020‑7045 | 2020‑01‑16 04:15:11 | MEDIUM (7) | In Wireshark 3.0.x before 3.0.8, the BT ATT dissector could crash. This was addressed in epan/dissectors/packet-btatt.c by validating opcodes. | 3 | 4 | ADJACENT_NETWORK |
| CVE‑2020‑7044 | 2020‑01‑16 04:15:11 | HIGH (8) | In Wireshark 3.2.x before 3.2.1, the WASSP dissector could crash. This was addressed in epan/dissectors/packet-wassp.c by using >= and <= to resolve off-by-one errors. | 4 | 4 | NETWORK |
| CVE‑2020‑28030 | 2020‑11‑02 21:15:30 | HIGH (8) | In Wireshark 3.2.0 to 3.2.7, the GQUIC dissector could crash. This was addressed in epan/dissectors/packet-gquic.c by correcting the implementation of offset advancement. | 4 | 4 | NETWORK |
| CVE‑2020‑26575 | 2020‑10‑06 15:15:16 | HIGH (8) | In Wireshark through 3.2.7, the Facebook Zero Protocol (aka FBZERO) dissector could enter an infinite loop. This was addressed in epan/dissectors/packet-fbzero.c by correcting the implementation of offset advancement. | 4 | 4 | NETWORK |
| CVE‑2020‑26422 | 2020‑12‑21 18:15:15 | MEDIUM (5) | Buffer overflow in QUIC dissector in Wireshark 3.4.0 to 3.4.1 allows denial of service via packet injection or crafted capture file | 4 | 1 | NETWORK |
| CVE‑2020‑26421 | 2020‑12‑11 19:15:12 | MEDIUM (4) | Crash in USB HID protocol dissector and possibly other dissectors in Wireshark 3.4.0 and 3.2.0 to 3.2.8 allows denial of service via packet injection or crafted capture file. | 2 | 3 | NETWORK |
| CVE‑2020‑26420 | 2020‑12‑11 19:15:12 | LOW (3) | Memory leak in RTPS protocol dissector in Wireshark 3.4.0 and 3.2.0 to 3.2.8 allows denial of service via packet injection or crafted capture file. | 2 | 1 | NETWORK |
| CVE‑2020‑26419 | 2020‑12‑11 19:15:12 | LOW (3) | Memory leak in the dissection engine in Wireshark 3.4.0 allows denial of service via packet injection or crafted capture file. | 2 | 1 | NETWORK |
| CVE‑2020‑26418 | 2020‑12‑11 19:15:12 | MEDIUM (5) | Memory leak in Kafka protocol dissector in Wireshark 3.4.0 and 3.2.0 to 3.2.8 allows denial of service via packet injection or crafted capture file. | 4 | 1 | NETWORK |
| CVE‑2020‑25866 | 2020‑10‑06 15:15:15 | HIGH (8) | In Wireshark 3.2.0 to 3.2.6 and 3.0.0 to 3.0.13, the BLIP protocol dissector has a NULL pointer dereference because a buffer was sized for compressed (not uncompressed) messages. This was addressed in epan/dissectors/packet-blip.c by allowing reasonable compression ratios and rejecting ZIP bombs. | 4 | 4 | NETWORK |
| CVE‑2020‑25863 | 2020‑10‑06 15:15:15 | HIGH (8) | In Wireshark 3.2.0 to 3.2.6, 3.0.0 to 3.0.13, and 2.6.0 to 2.6.20, the MIME Multipart dissector could crash. This was addressed in epan/dissectors/packet-multipart.c by correcting the deallocation of invalid MIME parts. | 4 | 4 | NETWORK |
| CVE‑2020‑25862 | 2020‑10‑06 15:15:15 | HIGH (8) | In Wireshark 3.2.0 to 3.2.6, 3.0.0 to 3.0.13, and 2.6.0 to 2.6.20, the TCP dissector could crash. This was addressed in epan/dissectors/packet-tcp.c by changing the handling of the invalid 0xFFFF checksum. | 4 | 4 | NETWORK |
| CVE‑2020‑17498 | 2020‑08‑13 16:15:13 | MEDIUM (7) | In Wireshark 3.2.0 to 3.2.5, the Kafka protocol dissector could crash. This was addressed in epan/dissectors/packet-kafka.c by avoiding a double free during LZ4 decompression. | 3 | 4 | NETWORK |
| CVE‑2020‑15466 | 2020‑07‑05 11:15:10 | HIGH (8) | In Wireshark 3.2.0 to 3.2.4, the GVCP dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-gvcp.c by ensuring that an offset increases in all situations. | 4 | 4 | NETWORK |
| CVE‑2020‑13164 | 2020‑05‑19 22:15:12 | HIGH (8) | In Wireshark 3.2.0 to 3.2.3, 3.0.0 to 3.0.10, and 2.6.0 to 2.6.16, the NFS dissector could crash. This was addressed in epan/dissectors/packet-nfs.c by preventing excessive recursion, such as for a cycle in the directory graph on a filesystem. | 4 | 4 | NETWORK |
| CVE‑2020‑11647 | 2020‑04‑10 21:15:12 | HIGH (8) | In Wireshark 3.2.0 to 3.2.2, 3.0.0 to 3.0.9, and 2.6.0 to 2.6.15, the BACapp dissector could crash. This was addressed in epan/dissectors/packet-bacapp.c by limiting the amount of recursion. | 4 | 4 | NETWORK |
| CVE‑2019‑9214 | 2019‑02‑28 04:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.12 and 2.6.0 to 2.6.6, the RPCAP dissector could crash. This was addressed in epan/dissectors/packet-rpcap.c by avoiding an attempted dereference of a NULL conversation. | 0 | 0 | NETWORK |
| CVE‑2019‑9209 | 2019‑02‑28 04:29:00 | MEDIUM (6) | In Wireshark 2.4.0 to 2.4.12 and 2.6.0 to 2.6.6, the ASN.1 BER and related dissectors could crash. This was addressed in epan/dissectors/packet-ber.c by preventing a buffer overflow associated with excessive digits in time values. | 2 | 4 | LOCAL |
| CVE‑2019‑9208 | 2019‑02‑28 04:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.12 and 2.6.0 to 2.6.6, the TCAP dissector could crash. This was addressed in epan/dissectors/asn1/tcap/tcap.cnf by avoiding NULL pointer dereferences. | 0 | 0 | NETWORK |
| CVE‑2019‑5721 | 2019‑01‑08 23:29:01 | MEDIUM (4) | In Wireshark 2.4.0 to 2.4.11, the ENIP dissector could crash. This was addressed in epan/dissectors/packet-enip.c by changing the memory-management approach so that a use-after-free is avoided. | 0 | 0 | NETWORK |
| CVE‑2019‑5719 | 2019‑01‑08 23:29:01 | MEDIUM (4) | In Wireshark 2.6.0 to 2.6.5 and 2.4.0 to 2.4.11, the ISAKMP dissector could crash. This was addressed in epan/dissectors/packet-isakmp.c by properly handling the case of a missing decryption data block. | 0 | 0 | NETWORK |
| CVE‑2019‑5718 | 2019‑01‑08 23:29:00 | MEDIUM (4) | In Wireshark 2.6.0 to 2.6.5 and 2.4.0 to 2.4.11, the RTSE dissector and other ASN.1 dissectors could crash. This was addressed in epan/charsets.c by adding a get_t61_string length check. | 0 | 0 | NETWORK |
| CVE‑2019‑5717 | 2019‑01‑08 23:29:00 | MEDIUM (4) | In Wireshark 2.6.0 to 2.6.5 and 2.4.0 to 2.4.11, the P_MUL dissector could crash. This was addressed in epan/dissectors/packet-p_mul.c by rejecting the invalid sequence number of zero. | 0 | 0 | NETWORK |
| CVE‑2019‑5716 | 2019‑01‑08 23:29:00 | MEDIUM (4) | In Wireshark 2.6.0 to 2.6.5, the 6LoWPAN dissector could crash. This was addressed in epan/dissectors/packet-6lowpan.c by avoiding use of a TVB before its creation. | 0 | 0 | NETWORK |
| CVE‑2019‑19553 | 2019‑12‑05 01:15:14 | HIGH (8) | In Wireshark 3.0.0 to 3.0.6 and 2.6.0 to 2.6.12, the CMS dissector could crash. This was addressed in epan/dissectors/asn1/cms/packet-cms-template.c by ensuring that an object identifier is set to NULL after a ContentInfo dissection. | 4 | 4 | NETWORK |
| CVE‑2019‑16319 | 2019‑09‑15 16:15:13 | HIGH (8) | In Wireshark 3.0.0 to 3.0.3 and 2.6.0 to 2.6.10, the Gryphon dissector could go into an infinite loop. This was addressed in plugins/epan/gryphon/packet-gryphon.c by checking for a message length of zero. | 4 | 4 | NETWORK |
| CVE‑2019‑13619 | 2019‑07‑17 20:15:12 | HIGH (8) | In Wireshark 3.0.0 to 3.0.2, 2.6.0 to 2.6.9, and 2.4.0 to 2.4.15, the ASN.1 BER dissector and related dissectors could crash. This was addressed in epan/asn1.c by properly restricting buffer increments. | 4 | 4 | NETWORK |
| CVE‑2019‑12295 | 2019‑05‑23 12:29:00 | HIGH (8) | In Wireshark 3.0.0 to 3.0.1, 2.6.0 to 2.6.8, and 2.4.0 to 2.4.14, the dissection engine could crash. This was addressed in epan/packet.c by restricting the number of layers and consequently limiting recursion. | 4 | 4 | NETWORK |
| CVE‑2019‑10903 | 2019‑04‑09 04:29:02 | HIGH (8) | In Wireshark 2.4.0 to 2.4.13, 2.6.0 to 2.6.7, and 3.0.0, the DCERPC SPOOLSS dissector could crash. This was addressed in epan/dissectors/packet-dcerpc-spoolss.c by adding a boundary check. | 4 | 4 | NETWORK |
| CVE‑2019‑10902 | 2019‑04‑09 04:29:02 | MEDIUM (5) | In Wireshark 3.0.0, the TSDNS dissector could crash. This was addressed in epan/dissectors/packet-tsdns.c by splitting strings safely. | 0 | 0 | NETWORK |
| CVE‑2019‑10901 | 2019‑04‑09 04:29:01 | HIGH (8) | In Wireshark 2.4.0 to 2.4.13, 2.6.0 to 2.6.7, and 3.0.0, the LDSS dissector could crash. This was addressed in epan/dissectors/packet-ldss.c by handling file digests properly. | 4 | 4 | NETWORK |
| CVE‑2019‑10900 | 2019‑04‑09 04:29:01 | MEDIUM (5) | In Wireshark 3.0.0, the Rbm dissector could go into an infinite loop. This was addressed in epan/dissectors/file-rbm.c by handling unknown object types safely. | 0 | 0 | NETWORK |
| CVE‑2019‑10899 | 2019‑04‑09 04:29:01 | HIGH (8) | In Wireshark 2.4.0 to 2.4.13, 2.6.0 to 2.6.7, and 3.0.0, the SRVLOC dissector could crash. This was addressed in epan/dissectors/packet-srvloc.c by preventing a heap-based buffer under-read. | 4 | 4 | NETWORK |
| CVE‑2019‑10898 | 2019‑04‑09 04:29:01 | MEDIUM (5) | In Wireshark 3.0.0, the GSUP dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-gsm_gsup.c by rejecting an invalid Information Element length. | 0 | 0 | NETWORK |
| CVE‑2019‑10897 | 2019‑04‑09 04:29:01 | MEDIUM (5) | In Wireshark 3.0.0, the IEEE 802.11 dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-ieee80211.c by detecting cases in which the bit offset does not advance. | 0 | 0 | NETWORK |
| CVE‑2019‑10896 | 2019‑04‑09 04:29:01 | HIGH (8) | In Wireshark 2.4.0 to 2.4.13, 2.6.0 to 2.6.7, and 3.0.0, the DOF dissector could crash. This was addressed in epan/dissectors/packet-dof.c by properly handling generated IID and OID bytes. | 4 | 4 | NETWORK |
| CVE‑2019‑10895 | 2019‑04‑09 04:29:01 | HIGH (8) | In Wireshark 2.4.0 to 2.4.13, 2.6.0 to 2.6.7, and 3.0.0, the NetScaler file parser could crash. This was addressed in wiretap/netscaler.c by improving data validation. | 4 | 4 | NETWORK |
| CVE‑2019‑10894 | 2019‑04‑09 04:29:01 | HIGH (8) | In Wireshark 2.4.0 to 2.4.13, 2.6.0 to 2.6.7, and 3.0.0, the GSS-API dissector could crash. This was addressed in epan/dissectors/packet-gssapi.c by ensuring that a valid dissector is called. | 4 | 4 | NETWORK |
| CVE‑2018‑9274 | 2018‑04‑04 07:29:02 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, ui/failure_message.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9273 | 2018‑04‑04 07:29:02 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-pcp.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9272 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-h223.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9271 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-multipart.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9270 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/oids.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9269 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-giop.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9268 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-smb2.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9267 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-lapd.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9266 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-isup.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9265 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, epan/dissectors/packet-tn3270.c has a memory leak. | 0 | 0 | NETWORK |
| CVE‑2018‑9264 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, the ADB dissector could crash with a heap-based buffer overflow. This was addressed in epan/dissectors/packet-adb.c by checking for a length inconsistency. | 0 | 0 | NETWORK |
| CVE‑2018‑9263 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, the Kerberos dissector could crash. This was addressed in epan/dissectors/packet-kerberos.c by ensuring a nonzero key length. | 0 | 0 | NETWORK |
| CVE‑2018‑9262 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, the VLAN dissector could crash. This was addressed in epan/dissectors/packet-vlan.c by limiting VLAN tag nesting to restrict the recursion depth. | 0 | 0 | NETWORK |
| CVE‑2018‑9261 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, the NBAP dissector could crash with a large loop that ends with a heap-based buffer overflow. This was addressed in epan/dissectors/packet-nbap.c by prohibiting the self-linking of DCH-IDs. | 0 | 0 | NETWORK |
| CVE‑2018‑9260 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, the IEEE 802.15.4 dissector could crash. This was addressed in epan/dissectors/packet-ieee802154.c by ensuring that an allocation step occurs. | 0 | 0 | NETWORK |
| CVE‑2018‑9259 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, the MP4 dissector could crash. This was addressed in epan/dissectors/file-mp4.c by restricting the box recursion depth. | 0 | 0 | NETWORK |
| CVE‑2018‑9258 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5, the TCP dissector could crash. This was addressed in epan/dissectors/packet-tcp.c by preserving valid data sources. | 0 | 0 | NETWORK |
| CVE‑2018‑9257 | 2018‑04‑04 07:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5, the CQL dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-cql.c by checking for a nonzero number of columns. | 0 | 0 | NETWORK |
| CVE‑2018‑9256 | 2018‑04‑04 07:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.5 and 2.2.0 to 2.2.13, the LWAPP dissector could crash. This was addressed in epan/dissectors/packet-lwapp.c by limiting the encapsulation levels to restrict the recursion depth. | 0 | 0 | NETWORK |
| CVE‑2018‑7421 | 2018‑02‑23 22:29:02 | HIGH (8) | In Wireshark 2.2.0 to 2.2.12 and 2.4.0 to 2.4.4, the DMP dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-dmp.c by correctly supporting a bounded number of Security Categories for a DMP Security Classification. | 4 | 4 | NETWORK |
| CVE‑2018‑7420 | 2018‑02‑23 22:29:02 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.12 and 2.4.0 to 2.4.4, the pcapng file parser could crash. This was addressed in wiretap/pcapng.c by adding a block-size check for sysdig event blocks. | 0 | 0 | NETWORK |
| CVE‑2018‑7419 | 2018‑02‑23 22:29:02 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.12 and 2.4.0 to 2.4.4, the NBAP dissector could crash. This was addressed in epan/dissectors/asn1/nbap/nbap.cnf by ensuring DCH ID initialization. | 0 | 0 | NETWORK |
| CVE‑2018‑7418 | 2018‑02‑23 22:29:02 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.12 and 2.4.0 to 2.4.4, the SIGCOMP dissector could crash. This was addressed in epan/dissectors/packet-sigcomp.c by correcting the extraction of the length value. | 0 | 0 | NETWORK |
| CVE‑2018‑7417 | 2018‑02‑23 22:29:02 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.12 and 2.4.0 to 2.4.4, the IPMI dissector could crash. This was addressed in epan/dissectors/packet-ipmi-picmg.c by adding support for crafted packets that lack an IPMI header. | 0 | 0 | NETWORK |
| CVE‑2018‑7337 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4, the DOCSIS protocol dissector could crash. This was addressed in plugins/docsis/packet-docsis.c by removing the recursive algorithm that had been used for concatenated PDUs. | 0 | 0 | NETWORK |
| CVE‑2018‑7336 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, the FCP protocol dissector could crash. This was addressed in epan/dissectors/packet-fcp.c by checking for a NULL pointer. | 0 | 0 | NETWORK |
| CVE‑2018‑7335 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, the IEEE 802.11 dissector could crash. This was addressed in epan/crypt/airpdcap.c by rejecting lengths that are too small. | 0 | 0 | NETWORK |
| CVE‑2018‑7334 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, the UMTS MAC dissector could crash. This was addressed in epan/dissectors/packet-umts_mac.c by rejecting a certain reserved value. | 0 | 0 | NETWORK |
| CVE‑2018‑7333 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-rpcrdma.c had an infinite loop that was addressed by validating a chunk size. | 0 | 0 | NETWORK |
| CVE‑2018‑7332 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-reload.c had an infinite loop that was addressed by validating a length. | 0 | 0 | NETWORK |
| CVE‑2018‑7331 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-ber.c had an infinite loop that was addressed by validating a length. | 0 | 0 | NETWORK |
| CVE‑2018‑7330 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-thread.c had an infinite loop that was addressed by using a correct integer data type. | 0 | 0 | NETWORK |
| CVE‑2018‑7329 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-s7comm.c had an infinite loop that was addressed by correcting off-by-one errors. | 0 | 0 | NETWORK |
| CVE‑2018‑7328 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-usb.c had an infinite loop that was addressed by rejecting short frame header lengths. | 0 | 0 | NETWORK |
| CVE‑2018‑7327 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-openflow_v6.c had an infinite loop that was addressed by validating property lengths. | 0 | 0 | NETWORK |
| CVE‑2018‑7326 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-lltd.c had an infinite loop that was addressed by using a correct integer data type. | 0 | 0 | NETWORK |
| CVE‑2018‑7325 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-rpki-rtr.c had an infinite loop that was addressed by validating a length field. | 0 | 0 | NETWORK |
| CVE‑2018‑7324 | 2018‑02‑23 22:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-sccp.c had an infinite loop that was addressed by using a correct integer data type. | 0 | 0 | NETWORK |
| CVE‑2018‑7323 | 2018‑02‑23 22:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-wccp.c had a large loop that was addressed by ensuring that a calculated length was monotonically increasing. | 0 | 0 | NETWORK |
| CVE‑2018‑7322 | 2018‑02‑23 22:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-dcm.c had an infinite loop that was addressed by checking for integer wraparound. | 0 | 0 | NETWORK |
| CVE‑2018‑7321 | 2018‑02‑23 22:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, epan/dissectors/packet-thrift.c had a large loop that was addressed by not proceeding with dissection after encountering an unexpected type. | 0 | 0 | NETWORK |
| CVE‑2018‑7320 | 2018‑02‑23 22:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.4 and 2.2.0 to 2.2.12, the SIGCOMP protocol dissector could crash. This was addressed in epan/dissectors/packet-sigcomp.c by validating operand offsets. | 0 | 0 | NETWORK |
| CVE‑2018‑6836 | 2018‑02‑08 07:29:01 | HIGH (8) | The netmonrec_comment_destroy function in wiretap/netmon.c in Wireshark through 2.4.4 performs a free operation on an uninitialized memory address, which allows remote attackers to cause a denial of service (application crash) or possibly have unspecified other impact. | 0 | 0 | NETWORK |
| CVE‑2018‑5336 | 2018‑01‑11 21:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.3 and 2.2.0 to 2.2.11, the JSON, XML, NTP, XMPP, and GDB dissectors could crash. This was addressed in epan/tvbparse.c by limiting the recursion depth. | 0 | 0 | NETWORK |
| CVE‑2018‑5335 | 2018‑01‑11 21:29:00 | MEDIUM (4) | In Wireshark 2.4.0 to 2.4.3 and 2.2.0 to 2.2.11, the WCP dissector could crash. This was addressed in epan/dissectors/packet-wcp.c by validating the available buffer length. | 0 | 0 | NETWORK |
| CVE‑2018‑5334 | 2018‑01‑11 21:29:00 | MEDIUM (4) | In Wireshark 2.4.0 to 2.4.3 and 2.2.0 to 2.2.11, the IxVeriWave file parser could crash. This was addressed in wiretap/vwr.c by correcting the signature timestamp bounds checks. | 0 | 0 | NETWORK |
| CVE‑2018‑19628 | 2018‑11‑29 04:29:01 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.4, the ZigBee ZCL dissector could crash. This was addressed in epan/dissectors/packet-zbee-zcl-lighting.c by preventing a divide-by-zero error. | 0 | 0 | NETWORK |
| CVE‑2018‑19627 | 2018‑11‑29 04:29:01 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.4 and 2.4.0 to 2.4.10, the IxVeriWave file parser could crash. This was addressed in wiretap/vwr.c by adjusting a buffer boundary. | 0 | 0 | NETWORK |
| CVE‑2018‑19626 | 2018‑11‑29 04:29:01 | MEDIUM (4) | In Wireshark 2.6.0 to 2.6.4 and 2.4.0 to 2.4.10, the DCOM dissector could crash. This was addressed in epan/dissectors/packet-dcom.c by adding '\0' termination. | 0 | 0 | NETWORK |
| CVE‑2018‑19625 | 2018‑11‑29 04:29:01 | MEDIUM (4) | In Wireshark 2.6.0 to 2.6.4 and 2.4.0 to 2.4.10, the dissection engine could crash. This was addressed in epan/tvbuff_composite.c by preventing a heap-based buffer over-read. | 0 | 0 | NETWORK |
| CVE‑2018‑19624 | 2018‑11‑29 04:29:00 | MEDIUM (4) | In Wireshark 2.6.0 to 2.6.4 and 2.4.0 to 2.4.10, the PVFS dissector could crash. This was addressed in epan/dissectors/packet-pvfs2.c by preventing a NULL pointer dereference. | 0 | 0 | NETWORK |
| CVE‑2018‑19623 | 2018‑11‑29 04:29:00 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.4 and 2.4.0 to 2.4.10, the LBMPDM dissector could crash. In addition, a remote attacker could write arbitrary data to any memory locations before the packet-scoped memory. This was addressed in epan/dissectors/packet-lbmpdm.c by disallowing certain negative values. | 0 | 0 | NETWORK |
| CVE‑2018‑19622 | 2018‑11‑29 04:29:00 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.4 and 2.4.0 to 2.4.10, the MMSE dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-mmse.c by preventing length overflows. | 0 | 0 | NETWORK |
| CVE‑2018‑18227 | 2018‑10‑12 06:29:01 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.3 and 2.4.0 to 2.4.9, the MS-WSP protocol dissector could crash. This was addressed in epan/dissectors/packet-mswsp.c by properly handling NULL return values. | 0 | 0 | NETWORK |
| CVE‑2018‑18226 | 2018‑10‑12 06:29:01 | HIGH (8) | In Wireshark 2.6.0 to 2.6.3, the Steam IHS Discovery dissector could consume system memory. This was addressed in epan/dissectors/packet-steam-ihs-discovery.c by changing the memory-management approach. | 0 | 0 | NETWORK |
| CVE‑2018‑18225 | 2018‑10‑12 06:29:01 | HIGH (8) | In Wireshark 2.6.0 to 2.6.3, the CoAP dissector could crash. This was addressed in epan/dissectors/packet-coap.c by ensuring that the piv length is correctly computed. | 4 | 4 | NETWORK |
| CVE‑2018‑16058 | 2018‑08‑30 01:29:01 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.2, 2.4.0 to 2.4.8, and 2.2.0 to 2.2.16, the Bluetooth AVDTP dissector could crash. This was addressed in epan/dissectors/packet-btavdtp.c by properly initializing a data structure. | 0 | 0 | NETWORK |
| CVE‑2018‑16057 | 2018‑08‑30 01:29:00 | HIGH (8) | In Wireshark 2.6.0 to 2.6.2, 2.4.0 to 2.4.8, and 2.2.0 to 2.2.16, the Radiotap dissector could crash. This was addressed in epan/dissectors/packet-ieee80211-radiotap-iter.c by validating iterator operations. | 4 | 4 | NETWORK |
| CVE‑2018‑16056 | 2018‑08‑30 01:29:00 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.2, 2.4.0 to 2.4.8, and 2.2.0 to 2.2.16, the Bluetooth Attribute Protocol dissector could crash. This was addressed in epan/dissectors/packet-btatt.c by verifying that a dissector for a specific UUID exists. | 0 | 0 | NETWORK |
| CVE‑2018‑14438 | 2018‑07‑20 00:29:00 | MEDIUM (5) | In Wireshark through 2.6.2, the create_app_running_mutex function in wsutil/file_util.c calls SetSecurityDescriptorDacl to set a NULL DACL, which allows attackers to modify the access control arbitrarily. | 0 | 0 | NETWORK |
| CVE‑2018‑14370 | 2018‑07‑19 02:29:01 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.1 and 2.4.0 to 2.4.7, the IEEE 802.11 protocol dissector could crash. This was addressed in epan/crypt/airpdcap.c via bounds checking that prevents a buffer over-read. | 0 | 0 | NETWORK |
| CVE‑2018‑14369 | 2018‑07‑19 02:29:01 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, the HTTP2 dissector could crash. This was addressed in epan/dissectors/packet-http2.c by verifying that header data was found before proceeding to header decompression. | 0 | 0 | NETWORK |
| CVE‑2018‑14368 | 2018‑07‑19 02:29:01 | HIGH (8) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, the Bazaar protocol dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-bzr.c by properly handling items that are too long. | 0 | 0 | NETWORK |
| CVE‑2018‑14367 | 2018‑07‑19 02:29:01 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.1 and 2.4.0 to 2.4.7, the CoAP protocol dissector could crash. This was addressed in epan/dissectors/packet-coap.c by properly checking for a NULL condition. | 0 | 0 | NETWORK |
| CVE‑2018‑14344 | 2018‑07‑19 02:29:00 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, the ISMP dissector could crash. This was addressed in epan/dissectors/packet-ismp.c by validating the IPX address length to avoid a buffer over-read. | 0 | 0 | NETWORK |
| CVE‑2018‑14343 | 2018‑07‑19 02:29:00 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, the ASN.1 BER dissector could crash. This was addressed in epan/dissectors/packet-ber.c by ensuring that length values do not exceed the maximum signed integer. | 0 | 0 | NETWORK |
| CVE‑2018‑14342 | 2018‑07‑19 02:29:00 | HIGH (8) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, the BGP protocol dissector could go into a large loop. This was addressed in epan/dissectors/packet-bgp.c by validating Path Attribute lengths. | 0 | 0 | NETWORK |
| CVE‑2018‑14341 | 2018‑07‑19 02:29:00 | HIGH (8) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, the DICOM dissector could go into a large or infinite loop. This was addressed in epan/dissectors/packet-dcm.c by preventing an offset overflow. | 0 | 0 | NETWORK |
| CVE‑2018‑14340 | 2018‑07‑19 02:29:00 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, dissectors that support zlib decompression could crash. This was addressed in epan/tvbuff_zlib.c by rejecting negative lengths to avoid a buffer over-read. | 0 | 0 | NETWORK |
| CVE‑2018‑14339 | 2018‑07‑19 02:29:00 | MEDIUM (5) | In Wireshark 2.6.0 to 2.6.1, 2.4.0 to 2.4.7, and 2.2.0 to 2.2.15, the MMSE dissector could go into an infinite loop. This was addressed in epan/proto.c by adding offset and length validation. | 0 | 0 | NETWORK |
| CVE‑2018‑11362 | 2018‑05‑22 21:29:01 | MEDIUM (5) | In Wireshark 2.6.0, 2.4.0 to 2.4.6, and 2.2.0 to 2.2.14, the LDSS dissector could crash. This was addressed in epan/dissectors/packet-ldss.c by avoiding a buffer over-read upon encountering a missing '\0' character. | 0 | 0 | NETWORK |
| CVE‑2018‑11361 | 2018‑05‑22 21:29:01 | MEDIUM (5) | In Wireshark 2.6.0, the IEEE 802.11 protocol dissector could crash. This was addressed in epan/crypt/dot11decrypt.c by avoiding a buffer overflow during FTE processing in Dot11DecryptTDLSDeriveKey. | 0 | 0 | NETWORK |
| CVE‑2018‑11360 | 2018‑05‑22 21:29:00 | MEDIUM (5) | In Wireshark 2.6.0, 2.4.0 to 2.4.6, and 2.2.0 to 2.2.14, the GSM A DTAP dissector could crash. This was addressed in epan/dissectors/packet-gsm_a_dtap.c by fixing an off-by-one error that caused a buffer overflow. | 0 | 0 | NETWORK |
| CVE‑2018‑11359 | 2018‑05‑22 21:29:00 | MEDIUM (5) | In Wireshark 2.6.0, 2.4.0 to 2.4.6, and 2.2.0 to 2.2.14, the RRC dissector and other dissectors could crash. This was addressed in epan/proto.c by avoiding a NULL pointer dereference. | 0 | 0 | NETWORK |
| CVE‑2018‑11358 | 2018‑05‑22 21:29:00 | MEDIUM (5) | In Wireshark 2.6.0, 2.4.0 to 2.4.6, and 2.2.0 to 2.2.14, the Q.931 dissector could crash. This was addressed in epan/dissectors/packet-q931.c by avoiding a use-after-free after a malformed packet prevented certain cleanup. | 0 | 0 | NETWORK |
| CVE‑2018‑11357 | 2018‑05‑22 21:29:00 | MEDIUM (5) | In Wireshark 2.6.0, 2.4.0 to 2.4.6, and 2.2.0 to 2.2.14, the LTP dissector and other dissectors could consume excessive memory. This was addressed in epan/tvbuff.c by rejecting negative lengths. | 0 | 0 | NETWORK |
| CVE‑2018‑11356 | 2018‑05‑22 21:29:00 | MEDIUM (5) | In Wireshark 2.6.0, 2.4.0 to 2.4.6, and 2.2.0 to 2.2.14, the DNS dissector could crash. This was addressed in epan/dissectors/packet-dns.c by avoiding a NULL pointer dereference for an empty name in an SRV record. | 0 | 0 | NETWORK |
| CVE‑2018‑11355 | 2018‑05‑22 21:29:00 | MEDIUM (5) | In Wireshark 2.6.0, the RTCP dissector could crash. This was addressed in epan/dissectors/packet-rtcp.c by avoiding a buffer overflow for packet status chunks. | 0 | 0 | NETWORK |
| CVE‑2018‑11354 | 2018‑05‑22 21:29:00 | MEDIUM (5) | In Wireshark 2.6.0, the IEEE 1905.1a dissector could crash. This was addressed in epan/dissectors/packet-ieee1905.c by making a certain correction to string handling. | 0 | 0 | NETWORK |
| CVE‑2017‑9766 | 2017‑06‑21 07:29:00 | MEDIUM (5) | In Wireshark 2.2.7, PROFINET IO data with a high recursion depth allows remote attackers to cause a denial of service (stack exhaustion) in the dissect_IODWriteReq function in plugins/profinet/packet-dcerpc-pn-io.c. | 0 | 0 | NETWORK |
| CVE‑2017‑9617 | 2017‑06‑14 20:29:00 | MEDIUM (4) | In Wireshark 2.2.7, deeply nested DAAP data may cause stack exhaustion (uncontrolled recursion) in the dissect_daap_one_tag function in epan/dissectors/packet-daap.c in the DAAP dissector. | 0 | 0 | NETWORK |
| CVE‑2017‑9616 | 2017‑06‑14 20:29:00 | MEDIUM (4) | In Wireshark 2.2.7, overly deep mp4 chunks may cause stack exhaustion (uncontrolled recursion) in the dissect_mp4_box function in epan/dissectors/file-mp4.c. | 0 | 0 | NETWORK |
| CVE‑2017‑9354 | 2017‑06‑02 05:29:01 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the RGMP dissector could crash. This was addressed in epan/dissectors/packet-rgmp.c by validating an IPv4 address. | 0 | 0 | NETWORK |
| CVE‑2017‑9353 | 2017‑06‑02 05:29:01 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.6, the IPv6 dissector could crash. This was addressed in epan/dissectors/packet-ipv6.c by validating an IPv6 address. | 0 | 0 | NETWORK |
| CVE‑2017‑9352 | 2017‑06‑02 05:29:01 | HIGH (8) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the Bazaar dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-bzr.c by ensuring that backwards parsing cannot occur. | 0 | 0 | NETWORK |
| CVE‑2017‑9351 | 2017‑06‑02 05:29:01 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the DHCP dissector could read past the end of a buffer. This was addressed in epan/dissectors/packet-bootp.c by extracting the Vendor Class Identifier more carefully. | 0 | 0 | NETWORK |
| CVE‑2017‑9350 | 2017‑06‑02 05:29:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the openSAFETY dissector could crash or exhaust system memory. This was addressed in epan/dissectors/packet-opensafety.c by checking for a negative length. | 0 | 0 | NETWORK |
| CVE‑2017‑9349 | 2017‑06‑02 05:29:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the DICOM dissector has an infinite loop. This was addressed in epan/dissectors/packet-dcm.c by validating a length value. | 0 | 0 | NETWORK |
| CVE‑2017‑9348 | 2017‑06‑02 05:29:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.6, the DOF dissector could read past the end of a buffer. This was addressed in epan/dissectors/packet-dof.c by validating a size value. | 0 | 0 | NETWORK |
| CVE‑2017‑9347 | 2017‑06‑02 05:29:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.6, the ROS dissector could crash with a NULL pointer dereference. This was addressed in epan/dissectors/asn1/ros/packet-ros-template.c by validating an OID. | 0 | 0 | NETWORK |
| CVE‑2017‑9346 | 2017‑06‑02 05:29:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the SoulSeek dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-slsk.c by making loop bounds more explicit. | 0 | 0 | NETWORK |
| CVE‑2017‑9345 | 2017‑06‑02 05:29:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the DNS dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-dns.c by trying to detect self-referencing pointers. | 0 | 0 | NETWORK |
| CVE‑2017‑9344 | 2017‑06‑02 05:29:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the Bluetooth L2CAP dissector could divide by zero. This was addressed in epan/dissectors/packet-btl2cap.c by validating an interval value. | 0 | 0 | NETWORK |
| CVE‑2017‑9343 | 2017‑06‑02 05:29:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.6 and 2.0.0 to 2.0.12, the MSNIP dissector misuses a NULL pointer. This was addressed in epan/dissectors/packet-msnip.c by validating an IPv4 address. | 0 | 0 | NETWORK |
| CVE‑2017‑7748 | 2017‑04‑12 23:59:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the WSP dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-wsp.c by adding a length check. | 0 | 0 | NETWORK |
| CVE‑2017‑7747 | 2017‑04‑12 23:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the PacketBB dissector could crash, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-packetbb.c by restricting additions to the protocol tree. | 0 | 0 | NETWORK |
| CVE‑2017‑7746 | 2017‑04‑12 23:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the SLSK dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-slsk.c by adding checks for the remaining length. | 0 | 0 | NETWORK |
| CVE‑2017‑7745 | 2017‑04‑12 23:59:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the SIGCOMP dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-sigcomp.c by correcting a memory-size check. | 0 | 0 | NETWORK |
| CVE‑2017‑7705 | 2017‑04‑12 23:59:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the RPC over RDMA dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-rpcrdma.c by correctly checking for going beyond the maximum offset. | 0 | 0 | NETWORK |
| CVE‑2017‑7704 | 2017‑04‑12 23:59:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.5, the DOF dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-dof.c by using a different integer data type and adjusting a return value. | 0 | 0 | NETWORK |
| CVE‑2017‑7703 | 2017‑04‑12 23:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the IMAP dissector could crash, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-imap.c by calculating a line's end correctly. | 0 | 0 | NETWORK |
| CVE‑2017‑7702 | 2017‑04‑12 23:59:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the WBXML dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-wbxml.c by adding length validation. | 0 | 0 | NETWORK |
| CVE‑2017‑7701 | 2017‑04‑12 23:59:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the BGP dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-bgp.c by using a different integer data type. | 0 | 0 | NETWORK |
| CVE‑2017‑7700 | 2017‑04‑12 23:59:00 | HIGH (7) | In Wireshark 2.2.0 to 2.2.5 and 2.0.0 to 2.0.11, the NetScaler file parser could go into an infinite loop, triggered by a malformed capture file. This was addressed in wiretap/netscaler.c by ensuring a nonzero record size. | 0 | 0 | NETWORK |
| CVE‑2017‑6474 | 2017‑03‑04 03:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is a NetScaler file parser infinite loop, triggered by a malformed capture file. This was addressed in wiretap/netscaler.c by validating record sizes. | 0 | 0 | NETWORK |
| CVE‑2017‑6473 | 2017‑03‑04 03:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is a K12 file parser crash, triggered by a malformed capture file. This was addressed in wiretap/k12.c by validating the relationships between lengths and offsets. | 0 | 0 | NETWORK |
| CVE‑2017‑6472 | 2017‑03‑04 03:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is an RTMPT dissector infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-rtmpt.c by properly incrementing a certain sequence value. | 0 | 0 | NETWORK |
| CVE‑2017‑6471 | 2017‑03‑04 03:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is a WSP infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-wsp.c by validating the capability length. | 0 | 0 | NETWORK |
| CVE‑2017‑6470 | 2017‑03‑04 03:59:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is an IAX2 infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-iax2.c by constraining packet lateness. | 0 | 0 | NETWORK |
| CVE‑2017‑6469 | 2017‑03‑04 03:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is an LDSS dissector crash, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-ldss.c by ensuring that memory is allocated for a certain data structure. | 0 | 0 | NETWORK |
| CVE‑2017‑6468 | 2017‑03‑04 03:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is a NetScaler file parser crash, triggered by a malformed capture file. This was addressed in wiretap/netscaler.c by validating the relationship between pages and records. | 0 | 0 | NETWORK |
| CVE‑2017‑6467 | 2017‑03‑04 03:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.4 and 2.0.0 to 2.0.10, there is a Netscaler file parser infinite loop, triggered by a malformed capture file. This was addressed in wiretap/netscaler.c by changing the restrictions on file size. | 0 | 0 | NETWORK |
| CVE‑2017‑6014 | 2017‑02‑17 07:59:01 | HIGH (8) | In Wireshark 2.2.4 and earlier, a crafted or malformed STANAG 4607 capture file will cause an infinite loop and memory exhaustion. If the packet size field in a packet header is null, the offset to read from will not advance, causing continuous attempts to read the same zero length packet. This will quickly exhaust all system memory. | 0 | 0 | NETWORK |
| CVE‑2017‑5597 | 2017‑01‑25 21:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.3 and 2.0.0 to 2.0.9, the DHCPv6 dissector could go into a large loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-dhcpv6.c by changing a data type to avoid an integer overflow. | 0 | 0 | NETWORK |
| CVE‑2017‑5596 | 2017‑01‑25 21:59:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.3 and 2.0.0 to 2.0.9, the ASTERIX dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-asterix.c by changing a data type to avoid an integer overflow. | 0 | 0 | NETWORK |
| CVE‑2017‑17997 | 2017‑12‑30 07:29:01 | MEDIUM (5) | In Wireshark before 2.2.12, the MRDISC dissector misuses a NULL pointer and crashes. This was addressed in epan/dissectors/packet-mrdisc.c by validating an IPv4 address. This vulnerability is similar to CVE-2017-9343. | 0 | 0 | NETWORK |
| CVE‑2017‑17935 | 2017‑12‑27 17:08:23 | MEDIUM (5) | The File_read_line function in epan/wslua/wslua_file.c in Wireshark through 2.2.11 does not properly strip '\n' characters, which allows remote attackers to cause a denial of service (buffer underflow and application crash) via a crafted packet that triggers the attempted processing of an empty line. | 0 | 0 | NETWORK |
| CVE‑2017‑17085 | 2017‑12‑01 08:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.2 and 2.2.0 to 2.2.10, the CIP Safety dissector could crash. This was addressed in epan/dissectors/packet-cipsafety.c by validating the packet length. | 0 | 0 | NETWORK |
| CVE‑2017‑17084 | 2017‑12‑01 08:29:01 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.2 and 2.2.0 to 2.2.10, the IWARP_MPA dissector could crash. This was addressed in epan/dissectors/packet-iwarp-mpa.c by validating a ULPDU length. | 0 | 0 | NETWORK |
| CVE‑2017‑17083 | 2017‑12‑01 08:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.2 and 2.2.0 to 2.2.10, the NetBIOS dissector could crash. This was addressed in epan/dissectors/packet-netbios.c by ensuring that write operations are bounded by the beginning of a buffer. | 0 | 0 | NETWORK |
| CVE‑2017‑15193 | 2017‑10‑10 21:29:00 | HIGH (8) | In Wireshark 2.4.0 to 2.4.1 and 2.2.0 to 2.2.9, the MBIM dissector could crash or exhaust system memory. This was addressed in epan/dissectors/packet-mbim.c by changing the memory-allocation approach. | 0 | 0 | NETWORK |
| CVE‑2017‑15192 | 2017‑10‑10 21:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.1 and 2.2.0 to 2.2.9, the BT ATT dissector could crash. This was addressed in epan/dissectors/packet-btatt.c by considering a case where not all of the BTATT packets have the same encapsulation level. | 0 | 0 | NETWORK |
| CVE‑2017‑15191 | 2017‑10‑10 21:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.1, 2.2.0 to 2.2.9, and 2.0.0 to 2.0.15, the DMP dissector could crash. This was addressed in epan/dissectors/packet-dmp.c by validating a string length. | 0 | 0 | NETWORK |
| CVE‑2017‑15190 | 2017‑10‑10 21:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.1, the RTSP dissector could crash. This was addressed in epan/dissectors/packet-rtsp.c by correcting the scope of a variable. | 0 | 0 | NETWORK |
| CVE‑2017‑15189 | 2017‑10‑10 21:29:00 | MEDIUM (5) | In Wireshark 2.4.0 to 2.4.1, the DOCSIS dissector could go into an infinite loop. This was addressed in plugins/docsis/packet-docsis.c by adding decrements. | 0 | 0 | NETWORK |
| CVE‑2017‑13767 | 2017‑08‑30 09:29:01 | HIGH (8) | In Wireshark 2.4.0, 2.2.0 to 2.2.8, and 2.0.0 to 2.0.14, the MSDP dissector could go into an infinite loop. This was addressed in epan/dissectors/packet-msdp.c by adding length validation. | 0 | 0 | NETWORK |
| CVE‑2017‑13766 | 2017‑08‑30 09:29:00 | MEDIUM (5) | In Wireshark 2.4.0 and 2.2.0 to 2.2.8, the Profinet I/O dissector could crash with an out-of-bounds write. This was addressed in plugins/profinet/packet-dcerpc-pn-io.c by adding string validation. | 0 | 0 | NETWORK |
| CVE‑2017‑13765 | 2017‑08‑30 09:29:00 | MEDIUM (5) | In Wireshark 2.4.0, 2.2.0 to 2.2.8, and 2.0.0 to 2.0.14, the IrCOMM dissector has a buffer over-read and application crash. This was addressed in plugins/irda/packet-ircomm.c by adding length validation. | 0 | 0 | NETWORK |
| CVE‑2017‑13764 | 2017‑08‑30 09:29:00 | MEDIUM (5) | In Wireshark 2.4.0, the Modbus dissector could crash with a NULL pointer dereference. This was addressed in epan/dissectors/packet-mbtcp.c by adding length validation. | 0 | 0 | NETWORK |
| CVE‑2017‑11411 | 2017‑07‑18 21:29:00 | HIGH (8) | In Wireshark through 2.0.13 and 2.2.x through 2.2.7, the openSAFETY dissector could crash or exhaust system memory. This was addressed in epan/dissectors/packet-opensafety.c by adding length validation. NOTE: this vulnerability exists because of an incomplete fix for CVE-2017-9350. | 0 | 0 | NETWORK |
| CVE‑2017‑11410 | 2017‑07‑18 21:29:00 | HIGH (8) | In Wireshark through 2.0.13 and 2.2.x through 2.2.7, the WBXML dissector could go into an infinite loop, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-wbxml.c by adding validation of the relationships between indexes and lengths. NOTE: this vulnerability exists because of an incomplete fix for CVE-2017-7702. | 0 | 0 | NETWORK |
| CVE‑2017‑11409 | 2017‑07‑18 21:29:00 | HIGH (8) | In Wireshark 2.0.0 to 2.0.13, the GPRS LLC dissector could go into a large loop. This was addressed in epan/dissectors/packet-gprs-llc.c by using a different integer data type. | 0 | 0 | NETWORK |
| CVE‑2017‑11408 | 2017‑07‑18 21:29:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.7 and 2.0.0 to 2.0.13, the AMQP dissector could crash. This was addressed in epan/dissectors/packet-amqp.c by checking for successful list dissection. | 0 | 0 | NETWORK |
| CVE‑2017‑11407 | 2017‑07‑18 21:29:00 | MEDIUM (5) | In Wireshark 2.2.0 to 2.2.7 and 2.0.0 to 2.0.13, the MQ dissector could crash. This was addressed in epan/dissectors/packet-mq.c by validating the fragment length before a reassembly attempt. | 0 | 0 | NETWORK |
| CVE‑2017‑11406 | 2017‑07‑18 21:29:00 | HIGH (8) | In Wireshark 2.2.0 to 2.2.7 and 2.0.0 to 2.0.13, the DOCSIS dissector could go into an infinite loop. This was addressed in plugins/docsis/packet-docsis.c by rejecting invalid Frame Control parameter values. | 0 | 0 | NETWORK |
| CVE‑2016‑9376 | 2016‑11‑17 05:59:05 | MEDIUM (4) | In Wireshark 2.2.0 to 2.2.1 and 2.0.0 to 2.0.7, the OpenFlow dissector could crash with memory exhaustion, triggered by network traffic or a capture file. This was addressed in epan/dissectors/packet-openflow_v5.c by ensuring that certain length values were sufficiently large. | 0 | 0 | NETWORK |
| CVE‑2016‑9375 | 2016‑11‑17 05:59:04 | MEDIUM (4) | In Wireshark 2.2.0 to 2.2.1 and 2.0.0 to 2.0.7, the DTN dissector could go into an infinite loop, triggered by network traffic or a capture file. This was addressed in epan/dissectors/packet-dtn.c by checking whether SDNV evaluation was successful. | 0 | 0 | NETWORK |
| CVE‑2016‑9374 | 2016‑11‑17 05:59:03 | MEDIUM (4) | In Wireshark 2.2.0 to 2.2.1 and 2.0.0 to 2.0.7, the AllJoyn dissector could crash with a buffer over-read, triggered by network traffic or a capture file. This was addressed in epan/dissectors/packet-alljoyn.c by ensuring that a length variable properly tracked the state of a signature variable. | 0 | 0 | NETWORK |
| CVE‑2016‑9373 | 2016‑11‑17 05:59:02 | MEDIUM (4) | In Wireshark 2.2.0 to 2.2.1 and 2.0.0 to 2.0.7, the DCERPC dissector could crash with a use-after-free, triggered by network traffic or a capture file. This was addressed in epan/dissectors/packet-dcerpc-nt.c and epan/dissectors/packet-dcerpc-spoolss.c by using the wmem file scope for private strings. | 0 | 0 | NETWORK |
| CVE‑2016‑9372 | 2016‑11‑17 05:59:00 | MEDIUM (4) | In Wireshark 2.2.0 to 2.2.1, the Profinet I/O dissector could loop excessively, triggered by network traffic or a capture file. This was addressed in plugins/profinet/packet-pn-rtc-one.c by rejecting input with too many I/O objects. | 0 | 0 | NETWORK |
| CVE‑2016‑7958 | 2017‑04‑12 10:59:00 | MEDIUM (5) | In Wireshark 2.2.0, the NCP dissector could crash, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/CMakeLists.txt by registering this dissector. | 0 | 0 | NETWORK |
| CVE‑2016‑7957 | 2017‑04‑12 10:59:00 | MEDIUM (5) | In Wireshark 2.2.0, the Bluetooth L2CAP dissector could crash, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-btl2cap.c by avoiding use of a seven-byte memcmp for potentially shorter strings. | 0 | 0 | NETWORK |
| CVE‑2016‑7180 | 2016‑09‑09 10:59:06 | MEDIUM (4) | epan/dissectors/packet-ipmi-trace.c in the IPMI trace dissector in Wireshark 2.x before 2.0.6 does not properly consider whether a string is constant, which allows remote attackers to cause a denial of service (use-after-free and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑7179 | 2016‑09‑09 10:59:05 | MEDIUM (4) | Stack-based buffer overflow in epan/dissectors/packet-catapult-dct2000.c in the Catapult DCT2000 dissector in Wireshark 2.x before 2.0.6 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑7178 | 2016‑09‑09 10:59:04 | MEDIUM (4) | epan/dissectors/packet-umts_fp.c in the UMTS FP dissector in Wireshark 2.x before 2.0.6 does not ensure that memory is allocated for certain data structures, which allows remote attackers to cause a denial of service (invalid write access and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑7177 | 2016‑09‑09 10:59:03 | MEDIUM (4) | epan/dissectors/packet-catapult-dct2000.c in the Catapult DCT2000 dissector in Wireshark 2.x before 2.0.6 does not restrict the number of channels, which allows remote attackers to cause a denial of service (buffer over-read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑7176 | 2016‑09‑09 10:59:02 | MEDIUM (4) | epan/dissectors/packet-h225.c in the H.225 dissector in Wireshark 2.x before 2.0.6 calls snprintf with one of its input buffers as the output buffer, which allows remote attackers to cause a denial of service (copy overlap and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑7175 | 2016‑09‑09 10:59:00 | MEDIUM (4) | epan/dissectors/packet-qnet6.c in the QNX6 QNET dissector in Wireshark 2.x before 2.0.6 mishandles MAC address data, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6513 | 2016‑08‑06 23:59:14 | MEDIUM (4) | epan/dissectors/packet-wbxml.c in the WBXML dissector in Wireshark 2.x before 2.0.5 does not restrict the recursion depth, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6512 | 2016‑08‑06 23:59:12 | MEDIUM (4) | epan/dissectors/packet-wap.c in Wireshark 2.x before 2.0.5 omits an overflow check in the tvb_get_guintvar function, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet, related to the MMSE, WAP, WBXML, and WSP dissectors. | 0 | 0 | NETWORK |
| CVE‑2016‑6511 | 2016‑08‑06 23:59:11 | MEDIUM (4) | epan/proto.c in Wireshark 1.12.x before 1.12.13 and 2.x before 2.0.5 allows remote attackers to cause a denial of service (OpenFlow dissector large loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6510 | 2016‑08‑06 23:59:09 | MEDIUM (4) | Off-by-one error in epan/dissectors/packet-rlc.c in the RLC dissector in Wireshark 1.12.x before 1.12.13 and 2.x before 2.0.5 allows remote attackers to cause a denial of service (stack-based buffer overflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6509 | 2016‑08‑06 23:59:08 | MEDIUM (4) | epan/dissectors/packet-ldss.c in the LDSS dissector in Wireshark 1.12.x before 1.12.13 and 2.x before 2.0.5 mishandles conversations, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6508 | 2016‑08‑06 23:59:07 | MEDIUM (4) | epan/dissectors/packet-rlc.c in the RLC dissector in Wireshark 1.12.x before 1.12.13 and 2.x before 2.0.5 uses an incorrect integer data type, which allows remote attackers to cause a denial of service (large loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6507 | 2016‑08‑06 23:59:05 | MEDIUM (4) | epan/dissectors/packet-mmse.c in the MMSE dissector in Wireshark 1.12.x before 1.12.13 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6506 | 2016‑08‑06 23:59:04 | MEDIUM (4) | epan/dissectors/packet-wsp.c in the WSP dissector in Wireshark 1.12.x before 1.12.13 and 2.x before 2.0.5 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6505 | 2016‑08‑06 23:59:03 | MEDIUM (4) | epan/dissectors/packet-packetbb.c in the PacketBB dissector in Wireshark 1.12.x before 1.12.13 and 2.x before 2.0.5 allows remote attackers to cause a denial of service (divide-by-zero error and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6504 | 2016‑08‑06 23:59:01 | MEDIUM (4) | epan/dissectors/packet-ncp2222.inc in the NDS dissector in Wireshark 1.12.x before 1.12.13 does not properly maintain a ptvc data structure, which allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑6503 | 2016‑08‑06 23:59:00 | MEDIUM (4) | The CORBA IDL dissectors in Wireshark 2.x before 2.0.5 on 64-bit Windows platforms do not properly interact with Visual C++ compiler options, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑5359 | 2016‑08‑07 16:59:15 | MEDIUM (4) | epan/dissectors/packet-wbxml.c in the WBXML dissector in Wireshark 1.12.x before 1.12.12 mishandles offsets, which allows remote attackers to cause a denial of service (integer overflow and infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑5358 | 2016‑08‑07 16:59:13 | MEDIUM (4) | epan/dissectors/packet-pktap.c in the Ethernet dissector in Wireshark 2.x before 2.0.4 mishandles the packet-header data type, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑5357 | 2016‑08‑07 16:59:12 | MEDIUM (4) | wiretap/netscreen.c in the NetScreen file parser in Wireshark 1.12.x before 1.12.12 and 2.x before 2.0.4 mishandles sscanf unsigned-integer processing, which allows remote attackers to cause a denial of service (application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2016‑5356 | 2016‑08‑07 16:59:11 | MEDIUM (4) | wiretap/cosine.c in the CoSine file parser in Wireshark 1.12.x before 1.12.12 and 2.x before 2.0.4 mishandles sscanf unsigned-integer processing, which allows remote attackers to cause a denial of service (application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2016‑5355 | 2016‑08‑07 16:59:10 | MEDIUM (4) | wiretap/toshiba.c in the Toshiba file parser in Wireshark 1.12.x before 1.12.12 and 2.x before 2.0.4 mishandles sscanf unsigned-integer processing, which allows remote attackers to cause a denial of service (application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2016‑5354 | 2016‑08‑07 16:59:08 | MEDIUM (4) | The USB subsystem in Wireshark 1.12.x before 1.12.12 and 2.x before 2.0.4 mishandles class types, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑5353 | 2016‑08‑07 16:59:06 | MEDIUM (4) | epan/dissectors/packet-umts_fp.c in the UMTS FP dissector in Wireshark 1.12.x before 1.12.12 and 2.x before 2.0.4 mishandles the reserved C/T value, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑5352 | 2016‑08‑07 16:59:05 | MEDIUM (4) | epan/crypt/airpdcap.c in the IEEE 802.11 dissector in Wireshark 2.x before 2.0.4 mishandles certain length values, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑5351 | 2016‑08‑07 16:59:03 | MEDIUM (4) | epan/crypt/airpdcap.c in the IEEE 802.11 dissector in Wireshark 1.12.x before 1.12.12 and 2.x before 2.0.4 mishandles the lack of an EAPOL_RSN_KEY, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑5350 | 2016‑08‑07 16:59:02 | MEDIUM (4) | epan/dissectors/packet-dcerpc-spoolss.c in the SPOOLS component in Wireshark 1.12.x before 1.12.12 and 2.x before 2.0.4 mishandles unexpected offsets, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4421 | 2016‑05‑01 01:59:08 | MEDIUM (4) | epan/dissectors/packet-ber.c in the ASN.1 BER dissector in Wireshark 1.12.x before 1.12.10 and 2.x before 2.0.2 allows remote attackers to cause a denial of service (deep recursion, stack consumption, and application crash) via a packet that specifies deeply nested data. | 0 | 0 | NETWORK |
| CVE‑2016‑4420 | 2016‑05‑01 01:59:07 | MEDIUM (4) | The NFS dissector in Wireshark 2.x before 2.0.2 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4419 | 2016‑05‑01 01:59:06 | MEDIUM (4) | epan/dissectors/packet-spice.c in the SPICE dissector in Wireshark 2.x before 2.0.2 mishandles capability data, which allows remote attackers to cause a denial of service (large loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4418 | 2016‑05‑01 01:59:05 | MEDIUM (4) | epan/dissectors/packet-ber.c in the ASN.1 BER dissector in Wireshark 1.12.x before 1.12.10 and 2.x before 2.0.2 allows remote attackers to cause a denial of service (buffer over-read and application crash) via a crafted packet that triggers an empty set. | 0 | 0 | NETWORK |
| CVE‑2016‑4417 | 2016‑05‑01 01:59:04 | MEDIUM (4) | Off-by-one error in epan/dissectors/packet-gsm_abis_oml.c in the GSM A-bis OML dissector in Wireshark 1.12.x before 1.12.10 and 2.x before 2.0.2 allows remote attackers to cause a denial of service (buffer over-read and application crash) via a crafted packet that triggers a 0xff tag value. | 0 | 0 | NETWORK |
| CVE‑2016‑4416 | 2016‑05‑01 01:59:02 | MEDIUM (4) | epan/dissectors/packet-ieee80211.c in the IEEE 802.11 dissector in Wireshark 2.x before 2.0.2 mishandles the Grouping subfield, which allows remote attackers to cause a denial of service (buffer over-read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4415 | 2016‑05‑01 01:59:01 | MEDIUM (4) | wiretap/vwr.c in the Ixia IxVeriWave file parser in Wireshark 2.x before 2.0.2 incorrectly increases a certain octet count, which allows remote attackers to cause a denial of service (heap-based buffer overflow and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2016‑4085 | 2016‑04‑25 10:59:10 | MEDIUM (4) | Stack-based buffer overflow in epan/dissectors/packet-ncp2222.inc in the NCP dissector in Wireshark 1.12.x before 1.12.11 allows remote attackers to cause a denial of service (application crash) or possibly have unspecified other impact via a long string in a packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4084 | 2016‑04‑25 10:59:09 | MEDIUM (4) | Integer signedness error in epan/dissectors/packet-mswsp.c in the MS-WSP dissector in Wireshark 2.0.x before 2.0.3 allows remote attackers to cause a denial of service (integer overflow and application crash) via a crafted packet that triggers an unexpected array size. | 0 | 0 | NETWORK |
| CVE‑2016‑4083 | 2016‑04‑25 10:59:08 | MEDIUM (4) | epan/dissectors/packet-mswsp.c in the MS-WSP dissector in Wireshark 2.0.x before 2.0.3 does not ensure that data is available before array allocation, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4082 | 2016‑04‑25 10:59:07 | MEDIUM (4) | epan/dissectors/packet-gsm_cbch.c in the GSM CBCH dissector in Wireshark 1.12.x before 1.12.11 and 2.0.x before 2.0.3 uses the wrong variable to index an array, which allows remote attackers to cause a denial of service (out-of-bounds access and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4081 | 2016‑04‑25 10:59:06 | MEDIUM (4) | epan/dissectors/packet-iax2.c in the IAX2 dissector in Wireshark 1.12.x before 1.12.11 and 2.0.x before 2.0.3 uses an incorrect integer data type, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4080 | 2016‑04‑25 10:59:05 | MEDIUM (4) | epan/dissectors/packet-pktc.c in the PKTC dissector in Wireshark 1.12.x before 1.12.11 and 2.0.x before 2.0.3 misparses timestamp fields, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4079 | 2016‑04‑25 10:59:04 | MEDIUM (4) | epan/dissectors/packet-pktc.c in the PKTC dissector in Wireshark 1.12.x before 1.12.11 and 2.0.x before 2.0.3 does not verify BER identifiers, which allows remote attackers to cause a denial of service (out-of-bounds write and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4078 | 2016‑04‑25 10:59:03 | MEDIUM (4) | The IEEE 802.11 dissector in Wireshark 1.12.x before 1.12.11 and 2.0.x before 2.0.3 does not properly restrict element lists, which allows remote attackers to cause a denial of service (deep recursion and application crash) via a crafted packet, related to epan/dissectors/packet-capwap.c and epan/dissectors/packet-ieee80211.c. | 0 | 0 | NETWORK |
| CVE‑2016‑4077 | 2016‑04‑25 10:59:02 | MEDIUM (4) | epan/reassemble.c in TShark in Wireshark 2.0.x before 2.0.3 relies on incorrect special-case handling of truncated Tvb data structures, which allows remote attackers to cause a denial of service (use-after-free and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4076 | 2016‑04‑25 10:59:01 | MEDIUM (4) | epan/dissectors/packet-ncp2222.inc in the NCP dissector in Wireshark 2.0.x before 2.0.3 does not properly initialize memory for search patterns, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑4006 | 2016‑04‑25 10:59:00 | MEDIUM (4) | epan/proto.c in Wireshark 1.12.x before 1.12.11 and 2.0.x before 2.0.3 does not limit the protocol-tree depth, which allows remote attackers to cause a denial of service (stack memory consumption and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2532 | 2016‑02‑28 04:59:11 | MEDIUM (4) | The dissect_llrp_parameters function in epan/dissectors/packet-llrp.c in the LLRP dissector in Wireshark 1.12.x before 1.12.10 and 2.0.x before 2.0.2 does not limit the recursion depth, which allows remote attackers to cause a denial of service (memory consumption or application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2531 | 2016‑02‑28 04:59:10 | MEDIUM (4) | Off-by-one error in epan/dissectors/packet-rsl.c in the RSL dissector in Wireshark 1.12.x before 1.12.10 and 2.0.x before 2.0.2 allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet that triggers a 0xff tag value, a different vulnerability than CVE-2016-2530. | 0 | 0 | NETWORK |
| CVE‑2016‑2530 | 2016‑02‑28 04:59:09 | MEDIUM (4) | The dissct_rsl_ipaccess_msg function in epan/dissectors/packet-rsl.c in the RSL dissector in Wireshark 1.12.x before 1.12.10 and 2.0.x before 2.0.2 mishandles the case of an unrecognized TLV type, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet, a different vulnerability than CVE-2016-2531. | 0 | 0 | NETWORK |
| CVE‑2016‑2529 | 2016‑02‑28 04:59:08 | MEDIUM (4) | The iseries_check_file_type function in wiretap/iseries.c in the iSeries file parser in Wireshark 2.0.x before 2.0.2 does not consider that a line may lack the "OBJECT PROTOCOL" substring, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2016‑2528 | 2016‑02‑28 04:59:07 | MEDIUM (4) | The dissect_nhdr_extopt function in epan/dissectors/packet-lbmc.c in the LBMC dissector in Wireshark 2.0.x before 2.0.2 does not validate length values, which allows remote attackers to cause a denial of service (stack-based buffer overflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2527 | 2016‑02‑28 04:59:06 | MEDIUM (4) | wiretap/nettrace_3gpp_32_423.c in the 3GPP TS 32.423 Trace file parser in Wireshark 2.0.x before 2.0.2 does not ensure that a '\0' character is present at the end of certain strings, which allows remote attackers to cause a denial of service (stack-based buffer overflow and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2016‑2526 | 2016‑02‑28 04:59:05 | MEDIUM (4) | epan/dissectors/packet-hiqnet.c in the HiQnet dissector in Wireshark 2.0.x before 2.0.2 does not validate the data type, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2525 | 2016‑02‑28 04:59:04 | MEDIUM (4) | epan/dissectors/packet-http2.c in the HTTP/2 dissector in Wireshark 2.0.x before 2.0.2 does not limit the amount of header data, which allows remote attackers to cause a denial of service (memory consumption or application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2524 | 2016‑02‑28 04:59:03 | MEDIUM (4) | epan/dissectors/packet-x509af.c in the X.509AF dissector in Wireshark 2.0.x before 2.0.2 mishandles the algorithm ID, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2523 | 2016‑02‑28 04:59:02 | HIGH (7) | The dnp3_al_process_object function in epan/dissectors/packet-dnp.c in the DNP3 dissector in Wireshark 1.12.x before 1.12.10 and 2.0.x before 2.0.2 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2522 | 2016‑02‑28 04:59:01 | MEDIUM (4) | The dissect_ber_constrained_bitstring function in epan/dissectors/packet-ber.c in the ASN.1 BER dissector in Wireshark 2.0.x before 2.0.2 does not verify that a certain length is nonzero, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2016‑2521 | 2016‑02‑28 04:59:00 | HIGH (7) | Untrusted search path vulnerability in the WiresharkApplication class in ui/qt/wireshark_application.cpp in Wireshark 1.12.x before 1.12.10 and 2.0.x before 2.0.2 on Windows allows local users to gain privileges via a Trojan horse riched20.dll.dll file in the current working directory, related to use of QLibrary. | 0 | 0 | LOCAL |
| CVE‑2015‑8742 | 2016‑01‑04 05:59:33 | MEDIUM (4) | The dissect_CPMSetBindings function in epan/dissectors/packet-mswsp.c in the MS-WSP dissector in Wireshark 2.0.x before 2.0.1 does not validate the column size, which allows remote attackers to cause a denial of service (memory consumption or application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8741 | 2016‑01‑04 05:59:32 | MEDIUM (4) | The dissect_ppi function in epan/dissectors/packet-ppi.c in the PPI dissector in Wireshark 2.0.x before 2.0.1 does not initialize a packet-header data structure, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8740 | 2016‑01‑04 05:59:31 | MEDIUM (4) | The dissect_tds7_colmetadata_token function in epan/dissectors/packet-tds.c in the TDS dissector in Wireshark 2.0.x before 2.0.1 does not validate the number of columns, which allows remote attackers to cause a denial of service (stack-based buffer overflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8739 | 2016‑01‑04 05:59:30 | MEDIUM (4) | The ipmi_fmt_udpport function in epan/dissectors/packet-ipmi.c in the IPMI dissector in Wireshark 2.0.x before 2.0.1 improperly attempts to access a packet scope, which allows remote attackers to cause a denial of service (assertion failure and application exit) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8738 | 2016‑01‑04 05:59:29 | MEDIUM (4) | The s7comm_decode_ud_cpu_szl_subfunc function in epan/dissectors/packet-s7comm_szl_ids.c in the S7COMM dissector in Wireshark 2.0.x before 2.0.1 does not validate the list count in an SZL response, which allows remote attackers to cause a denial of service (divide-by-zero error and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8737 | 2016‑01‑04 05:59:28 | MEDIUM (4) | The mp2t_open function in wiretap/mp2t.c in the MP2T file parser in Wireshark 2.0.x before 2.0.1 does not validate the bit rate, which allows remote attackers to cause a denial of service (divide-by-zero error and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2015‑8736 | 2016‑01‑04 05:59:27 | MEDIUM (4) | The mp2t_find_next_pcr function in wiretap/mp2t.c in the MP2T file parser in Wireshark 2.0.x before 2.0.1 does not reserve memory for a trailer, which allows remote attackers to cause a denial of service (stack-based buffer overflow and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2015‑8735 | 2016‑01‑04 05:59:26 | MEDIUM (4) | The get_value function in epan/dissectors/packet-btatt.c in the Bluetooth Attribute (aka BT ATT) dissector in Wireshark 2.0.x before 2.0.1 uses an incorrect integer data type, which allows remote attackers to cause a denial of service (invalid write operation and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8734 | 2016‑01‑04 05:59:25 | MEDIUM (4) | The dissect_nwp function in epan/dissectors/packet-nwp.c in the NWP dissector in Wireshark 2.0.x before 2.0.1 mishandles the packet type, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8733 | 2016‑01‑04 05:59:24 | MEDIUM (4) | The ngsniffer_process_record function in wiretap/ngsniffer.c in the Sniffer file parser in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate the relationships between record lengths and record header lengths, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2015‑8732 | 2016‑01‑04 05:59:23 | MEDIUM (4) | The dissect_zcl_pwr_prof_pwrprofstatersp function in epan/dissectors/packet-zbee-zcl-general.c in the ZigBee ZCL dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate the Total Profile Number field, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8731 | 2016‑01‑04 05:59:22 | MEDIUM (4) | The dissct_rsl_ipaccess_msg function in epan/dissectors/packet-rsl.c in the RSL dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not reject unknown TLV types, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8730 | 2016‑01‑04 05:59:21 | MEDIUM (4) | epan/dissectors/packet-nbap.c in the NBAP dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate the number of items, which allows remote attackers to cause a denial of service (invalid read operation and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8729 | 2016‑01‑04 05:59:20 | MEDIUM (4) | The ascend_seek function in wiretap/ascendtext.c in the Ascend file parser in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not ensure the presence of a '\0' character at the end of a date string, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2015‑8728 | 2016‑01‑04 05:59:19 | MEDIUM (4) | The Mobile Identity parser in (1) epan/dissectors/packet-ansi_a.c in the ANSI A dissector and (2) epan/dissectors/packet-gsm_a_common.c in the GSM A dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 improperly uses the tvb_bcd_dig_to_wmem_packet_str function, which allows remote attackers to cause a denial of service (buffer overflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8727 | 2016‑01‑04 05:59:18 | MEDIUM (4) | The dissect_rsvp_common function in epan/dissectors/packet-rsvp.c in the RSVP dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not properly maintain request-key data, which allows remote attackers to cause a denial of service (use-after-free and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8726 | 2016‑01‑04 05:59:17 | MEDIUM (4) | wiretap/vwr.c in the VeriWave file parser in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate certain signature and Modulation and Coding Scheme (MCS) data, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2015‑8725 | 2016‑01‑04 05:59:16 | MEDIUM (4) | The dissect_diameter_base_framed_ipv6_prefix function in epan/dissectors/packet-diameter.c in the DIAMETER dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate the IPv6 prefix length, which allows remote attackers to cause a denial of service (stack-based buffer overflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8724 | 2016‑01‑04 05:59:15 | MEDIUM (4) | The AirPDcapDecryptWPABroadcastKey function in epan/crypt/airpdcap.c in the 802.11 dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not verify the WPA broadcast key length, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8723 | 2016‑01‑04 05:59:14 | MEDIUM (4) | The AirPDcapPacketProcess function in epan/crypt/airpdcap.c in the 802.11 dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate the relationship between the total length and the capture length, which allows remote attackers to cause a denial of service (stack-based buffer overflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8722 | 2016‑01‑04 05:59:13 | MEDIUM (4) | epan/dissectors/packet-sctp.c in the SCTP dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate the frame pointer, which allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8721 | 2016‑01‑04 05:59:12 | MEDIUM (4) | Buffer overflow in the tvb_uncompress function in epan/tvbuff_zlib.c in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 allows remote attackers to cause a denial of service (application crash) via a crafted packet with zlib compression. | 0 | 0 | NETWORK |
| CVE‑2015‑8720 | 2016‑01‑04 05:59:11 | MEDIUM (4) | The dissect_ber_GeneralizedTime function in epan/dissectors/packet-ber.c in the BER dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 improperly checks an sscanf return value, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8719 | 2016‑01‑04 05:59:10 | MEDIUM (4) | The dissect_dns_answer function in epan/dissectors/packet-dns.c in the DNS dissector in Wireshark 1.12.x before 1.12.9 mishandles the EDNS0 Client Subnet option, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8718 | 2016‑01‑04 05:59:09 | MEDIUM (4) | Double free vulnerability in epan/dissectors/packet-nlm.c in the NLM dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1, when the "Match MSG/RES packets for async NLM" option is enabled, allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8717 | 2016‑01‑04 05:59:07 | MEDIUM (4) | The dissect_sdp function in epan/dissectors/packet-sdp.c in the SDP dissector in Wireshark 1.12.x before 1.12.9 does not prevent use of a negative media count, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8716 | 2016‑01‑04 05:59:06 | MEDIUM (4) | The init_t38_info_conv function in epan/dissectors/packet-t38.c in the T.38 dissector in Wireshark 1.12.x before 1.12.9 does not ensure that a conversation exists, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8715 | 2016‑01‑04 05:59:05 | MEDIUM (4) | epan/dissectors/packet-alljoyn.c in the AllJoyn dissector in Wireshark 1.12.x before 1.12.9 does not check for empty arguments, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8714 | 2016‑01‑04 05:59:04 | MEDIUM (4) | The dissect_dcom_OBJREF function in epan/dissectors/packet-dcom.c in the DCOM dissector in Wireshark 1.12.x before 1.12.9 does not initialize a certain IPv4 data structure, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8713 | 2016‑01‑04 05:59:04 | MEDIUM (4) | epan/dissectors/packet-umts_fp.c in the UMTS FP dissector in Wireshark 1.12.x before 1.12.9 does not properly reserve memory for channel ID mappings, which allows remote attackers to cause a denial of service (out-of-bounds memory access and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8712 | 2016‑01‑04 05:59:03 | MEDIUM (4) | The dissect_hsdsch_channel_info function in epan/dissectors/packet-umts_fp.c in the UMTS FP dissector in Wireshark 1.12.x before 1.12.9 does not validate the number of PDUs, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑8711 | 2016‑01‑04 05:59:01 | MEDIUM (4) | epan/dissectors/packet-nbap.c in the NBAP dissector in Wireshark 1.12.x before 1.12.9 and 2.0.x before 2.0.1 does not validate conversation data, which allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑7830 | 2015‑11‑15 03:59:02 | MEDIUM (4) | The pcapng_read_if_descr_block function in wiretap/pcapng.c in the pcapng parser in Wireshark 1.12.x before 1.12.8 uses too many levels of pointer indirection, which allows remote attackers to cause a denial of service (incorrect free and application crash) via a crafted packet that triggers interface-filter copying. | 0 | 0 | NETWORK |
| CVE‑2015‑6249 | 2015‑08‑24 23:59:10 | MEDIUM (4) | The dissect_wccp2r1_address_table_info function in epan/dissectors/packet-wccp.c in the WCCP dissector in Wireshark 1.12.x before 1.12.7 does not prevent the conflicting use of a table for both IPv4 and IPv6 addresses, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑6248 | 2015‑08‑24 23:59:08 | MEDIUM (4) | The ptvcursor_add function in the ptvcursor implementation in epan/proto.c in Wireshark 1.12.x before 1.12.7 does not check whether the expected amount of data is available, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑6247 | 2015‑08‑24 23:59:07 | MEDIUM (4) | The dissect_openflow_tablemod_v5 function in epan/dissectors/packet-openflow_v5.c in the OpenFlow dissector in Wireshark 1.12.x before 1.12.7 does not validate a certain offset value, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑6246 | 2015‑08‑24 23:59:06 | MEDIUM (4) | The dissect_wa_payload function in epan/dissectors/packet-waveagent.c in the WaveAgent dissector in Wireshark 1.12.x before 1.12.7 mishandles large tag values, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑6245 | 2015‑08‑24 23:59:05 | MEDIUM (4) | epan/dissectors/packet-gsm_rlcmac.c in the GSM RLC/MAC dissector in Wireshark 1.12.x before 1.12.7 uses incorrect integer data types, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑6244 | 2015‑08‑24 23:59:04 | MEDIUM (4) | The dissect_zbee_secure function in epan/dissectors/packet-zbee-security.c in the ZigBee dissector in Wireshark 1.12.x before 1.12.7 improperly relies on length fields contained in packet data, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑6243 | 2015‑08‑24 23:59:03 | MEDIUM (4) | The dissector-table implementation in epan/packet.c in Wireshark 1.12.x before 1.12.7 mishandles table searches for empty strings, which allows remote attackers to cause a denial of service (application crash) via a crafted packet, related to the (1) dissector_get_string_handle and (2) dissector_get_default_string_handle functions. | 0 | 0 | NETWORK |
| CVE‑2015‑6242 | 2015‑08‑24 23:59:02 | MEDIUM (4) | The wmem_block_split_free_chunk function in epan/wmem/wmem_allocator_block.c in the wmem block allocator in the memory manager in Wireshark 1.12.x before 1.12.7 does not properly consider a certain case of multiple realloc operations that restore a memory chunk to its original size, which allows remote attackers to cause a denial of service (incorrect free operation and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑6241 | 2015‑08‑24 23:59:00 | MEDIUM (4) | The proto_tree_add_bytes_item function in epan/proto.c in the protocol-tree implementation in Wireshark 1.12.x before 1.12.7 does not properly terminate a data structure after a failure to locate a number within a string, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑4652 | 2015‑07‑22 01:59:05 | MEDIUM (4) | epan/dissectors/packet-gsm_a_dtap.c in the GSM DTAP dissector in Wireshark 1.12.x before 1.12.6 does not properly validate digit characters, which allows remote attackers to cause a denial of service (application crash) via a crafted packet, related to the de_emerg_num_list and de_bcd_num functions. | 0 | 0 | NETWORK |
| CVE‑2015‑4651 | 2015‑07‑22 01:59:03 | MEDIUM (5) | The dissect_wccp2r1_address_table_info function in epan/dissectors/packet-wccp.c in the WCCP dissector in Wireshark 1.12.x before 1.12.6 does not properly determine whether enough memory is available for storing IP address strings, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑3906 | 2015‑05‑26 15:59:12 | MEDIUM (5) | The logcat_dump_text function in wiretap/logcat.c in the Android Logcat file parser in Wireshark 1.12.x before 1.12.5 does not properly handle a lack of \0 termination, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted message in a packet, a different vulnerability than CVE-2015-3815. | 0 | 0 | NETWORK |
| CVE‑2015‑3815 | 2015‑05‑26 15:59:09 | MEDIUM (5) | The detect_version function in wiretap/logcat.c in the Android Logcat file parser in Wireshark 1.12.x before 1.12.5 does not check the length of the payload, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a packet with a crafted payload, as demonstrated by a length of zero, a different vulnerability than CVE-2015-3906. | 0 | 0 | NETWORK |
| CVE‑2015‑3814 | 2015‑05‑26 15:59:08 | MEDIUM (5) | The (1) dissect_tfs_request and (2) dissect_tfs_response functions in epan/dissectors/packet-ieee80211.c in the IEEE 802.11 dissector in Wireshark 1.10.x before 1.10.14 and 1.12.x before 1.12.5 interpret a zero value as a length rather than an error condition, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑3813 | 2015‑05‑26 15:59:07 | MEDIUM (5) | The fragment_add_work function in epan/reassemble.c in the packet-reassembly feature in Wireshark 1.12.x before 1.12.5 does not properly determine the defragmentation state in a case of an insufficient snapshot length, which allows remote attackers to cause a denial of service (memory consumption) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑3812 | 2015‑05‑26 15:59:06 | HIGH (8) | Multiple memory leaks in the x11_init_protocol function in epan/dissectors/packet-x11.c in the X11 dissector in Wireshark 1.10.x before 1.10.14 and 1.12.x before 1.12.5 allow remote attackers to cause a denial of service (memory consumption) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑3811 | 2015‑05‑26 15:59:05 | MEDIUM (5) | epan/dissectors/packet-wcp.c in the WCP dissector in Wireshark 1.10.x before 1.10.14 and 1.12.x before 1.12.5 improperly refers to previously processed bytes, which allows remote attackers to cause a denial of service (application crash) via a crafted packet, a different vulnerability than CVE-2015-2188. | 0 | 0 | NETWORK |
| CVE‑2015‑3810 | 2015‑05‑26 15:59:04 | HIGH (8) | epan/dissectors/packet-websocket.c in the WebSocket dissector in Wireshark 1.12.x before 1.12.5 uses a recursive algorithm, which allows remote attackers to cause a denial of service (CPU consumption) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑3809 | 2015‑05‑26 15:59:03 | HIGH (8) | The dissect_lbmr_pser function in epan/dissectors/packet-lbmr.c in the LBMR dissector in Wireshark 1.12.x before 1.12.5 does not properly track the current offset, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑3808 | 2015‑05‑26 15:59:02 | HIGH (8) | The dissect_lbmr_pser function in epan/dissectors/packet-lbmr.c in the LBMR dissector in Wireshark 1.12.x before 1.12.5 does not reject a zero length, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑3182 | 2016‑01‑04 05:59:00 | MEDIUM (4) | epan/dissectors/packet-dec-dnart.c in the DECnet NSP/RT dissector in Wireshark 1.10.12 through 1.10.14 mishandles a certain strdup return value, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑2192 | 2015‑03‑08 02:59:07 | MEDIUM (5) | Integer overflow in the dissect_osd2_cdb_continuation function in epan/dissectors/packet-scsi-osd.c in the SCSI OSD dissector in Wireshark 1.12.x before 1.12.4 allows remote attackers to cause a denial of service (infinite loop) via a crafted length field in a packet. | 0 | 0 | NETWORK |
| CVE‑2015‑2191 | 2015‑03‑08 02:59:06 | MEDIUM (5) | Integer overflow in the dissect_tnef function in epan/dissectors/packet-tnef.c in the TNEF dissector in Wireshark 1.10.x before 1.10.13 and 1.12.x before 1.12.4 allows remote attackers to cause a denial of service (infinite loop) via a crafted length field in a packet. | 0 | 0 | NETWORK |
| CVE‑2015‑2190 | 2015‑03‑08 02:59:05 | MEDIUM (5) | epan/proto.c in Wireshark 1.12.x before 1.12.4 does not properly handle integer data types greater than 32 bits in size, which allows remote attackers to cause a denial of service (assertion failure and application exit) via a crafted packet that is improperly handled by the LLDP dissector. | 0 | 0 | NETWORK |
| CVE‑2015‑2189 | 2015‑03‑08 02:59:04 | MEDIUM (5) | Off-by-one error in the pcapng_read function in wiretap/pcapng.c in the pcapng file parser in Wireshark 1.10.x before 1.10.13 and 1.12.x before 1.12.4 allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via an invalid Interface Statistics Block (ISB) interface ID in a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑2188 | 2015‑03‑08 02:59:03 | MEDIUM (5) | epan/dissectors/packet-wcp.c in the WCP dissector in Wireshark 1.10.x before 1.10.13 and 1.12.x before 1.12.4 does not properly initialize a data structure, which allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via a crafted packet that is improperly handled during decompression. | 0 | 0 | NETWORK |
| CVE‑2015‑2187 | 2015‑03‑08 02:59:02 | MEDIUM (5) | The dissect_atn_cpdlc_heur function in asn1/atn-cpdlc/packet-atn-cpdlc-template.c in the ATN-CPDLC dissector in Wireshark 1.12.x before 1.12.4 does not properly follow the TRY/ENDTRY code requirements, which allows remote attackers to cause a denial of service (stack memory corruption and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑0564 | 2015‑01‑10 02:59:42 | MEDIUM (5) | Buffer underflow in the ssl_decrypt_record function in epan/dissectors/packet-ssl-utils.c in Wireshark 1.10.x before 1.10.12 and 1.12.x before 1.12.3 allows remote attackers to cause a denial of service (application crash) via a crafted packet that is improperly handled during decryption of an SSL session. | 0 | 0 | NETWORK |
| CVE‑2015‑0563 | 2015‑01‑10 02:59:42 | MEDIUM (5) | epan/dissectors/packet-smtp.c in the SMTP dissector in Wireshark 1.10.x before 1.10.12 and 1.12.x before 1.12.3 uses an incorrect length value for certain string-append operations, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑0562 | 2015‑01‑10 02:59:41 | MEDIUM (5) | Multiple use-after-free vulnerabilities in epan/dissectors/packet-dec-dnart.c in the DEC DNA Routing Protocol dissector in Wireshark 1.10.x before 1.10.12 and 1.12.x before 1.12.3 allow remote attackers to cause a denial of service (application crash) via a crafted packet, related to the use of packet-scope memory instead of pinfo-scope memory. | 0 | 0 | NETWORK |
| CVE‑2015‑0561 | 2015‑01‑10 02:59:40 | MEDIUM (5) | asn1/lpp/lpp.cnf in the LPP dissector in Wireshark 1.10.x before 1.10.12 and 1.12.x before 1.12.3 does not validate a certain index value, which allows remote attackers to cause a denial of service (out-of-bounds memory access and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑0560 | 2015‑01‑10 02:59:39 | MEDIUM (5) | The dissect_wccp2r1_address_table_info function in epan/dissectors/packet-wccp.c in the WCCP dissector in Wireshark 1.10.x before 1.10.12 and 1.12.x before 1.12.3 does not initialize certain data structures, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2015‑0559 | 2015‑01‑10 02:59:38 | MEDIUM (5) | Multiple use-after-free vulnerabilities in epan/dissectors/packet-wccp.c in the WCCP dissector in Wireshark 1.10.x before 1.10.12 and 1.12.x before 1.12.3 allow remote attackers to cause a denial of service (application crash) via a crafted packet, related to the use of packet-scope memory instead of pinfo-scope memory. | 0 | 0 | NETWORK |
| CVE‑2014‑8714 | 2014‑11‑23 02:59:06 | MEDIUM (5) | The dissect_write_structured_field function in epan/dissectors/packet-tn5250.c in the TN5250 dissector in Wireshark 1.10.x before 1.10.11 and 1.12.x before 1.12.2 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑8713 | 2014‑11‑23 02:59:05 | MEDIUM (5) | Stack-based buffer overflow in the build_expert_data function in epan/dissectors/packet-ncp2222.inc in the NCP dissector in Wireshark 1.10.x before 1.10.11 and 1.12.x before 1.12.2 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑8712 | 2014‑11‑23 02:59:04 | MEDIUM (5) | The build_expert_data function in epan/dissectors/packet-ncp2222.inc in the NCP dissector in Wireshark 1.10.x before 1.10.11 and 1.12.x before 1.12.2 does not properly initialize a data structure, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑8711 | 2014‑11‑23 02:59:03 | MEDIUM (5) | Multiple integer overflows in epan/dissectors/packet-amqp.c in the AMQP dissector in Wireshark 1.10.x before 1.10.11 and 1.12.x before 1.12.2 allow remote attackers to cause a denial of service (application crash) via a crafted amqp_0_10 PDU in a packet. | 0 | 0 | NETWORK |
| CVE‑2014‑8710 | 2014‑11‑23 02:59:01 | MEDIUM (5) | The decompress_sigcomp_message function in epan/sigcomp-udvm.c in the SigComp UDVM dissector in Wireshark 1.10.x before 1.10.11 allows remote attackers to cause a denial of service (buffer over-read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑6432 | 2014‑09‑20 10:55:07 | MEDIUM (5) | The SnifferDecompress function in wiretap/ngsniffer.c in the DOS Sniffer file parser in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 does not prevent data overwrites during copy operations, which allows remote attackers to cause a denial of service (application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2014‑6431 | 2014‑09‑20 10:55:07 | MEDIUM (5) | Buffer overflow in the SnifferDecompress function in wiretap/ngsniffer.c in the DOS Sniffer file parser in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 allows remote attackers to cause a denial of service (application crash) via a crafted file that triggers writes of uncompressed bytes beyond the end of the output buffer. | 0 | 0 | NETWORK |
| CVE‑2014‑6430 | 2014‑09‑20 10:55:07 | MEDIUM (5) | The SnifferDecompress function in wiretap/ngsniffer.c in the DOS Sniffer file parser in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 does not validate bitmask data, which allows remote attackers to cause a denial of service (application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2014‑6429 | 2014‑09‑20 10:55:07 | MEDIUM (5) | The SnifferDecompress function in wiretap/ngsniffer.c in the DOS Sniffer file parser in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 does not properly handle empty input data, which allows remote attackers to cause a denial of service (application crash) via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2014‑6428 | 2014‑09‑20 10:55:06 | MEDIUM (5) | The dissect_spdu function in epan/dissectors/packet-ses.c in the SES dissector in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 does not initialize a certain ID value, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑6427 | 2014‑09‑20 10:55:06 | MEDIUM (5) | Off-by-one error in the is_rtsp_request_or_reply function in epan/dissectors/packet-rtsp.c in the RTSP dissector in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 allows remote attackers to cause a denial of service (application crash) via a crafted packet that triggers parsing of a token located one position beyond the current position. | 0 | 0 | NETWORK |
| CVE‑2014‑6426 | 2014‑09‑20 10:55:06 | MEDIUM (5) | The dissect_hip_tlv function in epan/dissectors/packet-hip.c in the HIP dissector in Wireshark 1.12.x before 1.12.1 does not properly handle a NULL tree, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑6425 | 2014‑09‑20 10:55:06 | MEDIUM (5) | The (1) get_quoted_string and (2) get_unquoted_string functions in epan/dissectors/packet-cups.c in the CUPS dissector in Wireshark 1.12.x before 1.12.1 allow remote attackers to cause a denial of service (buffer over-read and application crash) via a CUPS packet that lacks a trailing '\0' character. | 0 | 0 | NETWORK |
| CVE‑2014‑6424 | 2014‑09‑20 10:55:06 | MEDIUM (5) | The dissect_v9_v10_pdu_data function in epan/dissectors/packet-netflow.c in the Netflow dissector in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 refers to incorrect offset and start variables, which allows remote attackers to cause a denial of service (uninitialized memory read and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑6423 | 2014‑09‑20 10:55:06 | MEDIUM (5) | The tvb_raw_text_add function in epan/dissectors/packet-megaco.c in the MEGACO dissector in Wireshark 1.10.x before 1.10.10 and 1.12.x before 1.12.1 allows remote attackers to cause a denial of service (infinite loop) via an empty line. | 0 | 0 | NETWORK |
| CVE‑2014‑6422 | 2014‑09‑20 10:55:06 | MEDIUM (5) | The SDP dissector in Wireshark 1.10.x before 1.10.10 creates duplicate hashtables for a media channel, which allows remote attackers to cause a denial of service (application crash) via a crafted packet to the RTP dissector. | 0 | 0 | NETWORK |
| CVE‑2014‑6421 | 2014‑09‑20 10:55:06 | MEDIUM (5) | Use-after-free vulnerability in the SDP dissector in Wireshark 1.10.x before 1.10.10 allows remote attackers to cause a denial of service (application crash) via a crafted packet that leverages split memory ownership between the SDP and RTP dissectors. | 0 | 0 | NETWORK |
| CVE‑2014‑5165 | 2014‑08‑01 11:13:10 | MEDIUM (5) | The dissect_ber_constrained_bitstring function in epan/dissectors/packet-ber.c in the ASN.1 BER dissector in Wireshark 1.10.x before 1.10.9 does not properly validate padding values, which allows remote attackers to cause a denial of service (buffer underflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑5164 | 2014‑08‑01 11:13:10 | MEDIUM (5) | The rlc_decode_li function in epan/dissectors/packet-rlc.c in the RLC dissector in Wireshark 1.10.x before 1.10.9 initializes a certain structure member only after this member is used, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑5163 | 2014‑08‑01 11:13:10 | MEDIUM (5) | The APN decode functionality in (1) epan/dissectors/packet-gtp.c and (2) epan/dissectors/packet-gsm_a_gm.c in the GTP and GSM Management dissectors in Wireshark 1.10.x before 1.10.9 does not completely initialize a certain buffer, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑5162 | 2014‑08‑01 11:13:10 | MEDIUM (5) | The read_new_line function in wiretap/catapult_dct2000.c in the Catapult DCT2000 dissector in Wireshark 1.10.x before 1.10.9 does not properly strip '\n' and '\r' characters, which allows remote attackers to cause a denial of service (off-by-one buffer underflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑5161 | 2014‑08‑01 11:13:10 | MEDIUM (5) | The dissect_log function in plugins/irda/packet-irda.c in the IrDA dissector in Wireshark 1.10.x before 1.10.9 does not properly strip '\n' characters, which allows remote attackers to cause a denial of service (buffer underflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑4174 | 2014‑06‑18 16:55:08 | HIGH (9) | wiretap/libpcap.c in the libpcap file parser in Wireshark 1.10.x before 1.10.4 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption and application crash) via a crafted packet-trace file that includes a large packet. | 0 | 0 | NETWORK |
| CVE‑2014‑4020 | 2014‑06‑18 16:55:08 | MEDIUM (4) | The dissect_frame function in epan/dissectors/packet-frame.c in the frame metadissector in Wireshark 1.10.x before 1.10.8 interprets a negative integer as a length value even though it was intended to represent an error condition, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑2907 | 2014‑04‑24 10:55:02 | MEDIUM (4) | The srtp_add_address function in epan/dissectors/packet-rtp.c in the RTP dissector in Wireshark 1.10.x before 1.10.7 does not properly update SRTP conversation data, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2014‑2299 | 2014‑03‑11 13:01:10 | HIGH (9) | Buffer overflow in the mpeg_read function in wiretap/mpeg.c in the MPEG parser in Wireshark 1.8.x before 1.8.13 and 1.10.x before 1.10.6 allows remote attackers to execute arbitrary code or cause a denial of service (application crash) via a large record in MPEG data. | 0 | 0 | NETWORK |
| CVE‑2014‑2283 | 2014‑03‑11 13:01:10 | MEDIUM (4) | epan/dissectors/packet-rlc in the RLC dissector in Wireshark 1.8.x before 1.8.13 and 1.10.x before 1.10.6 uses inconsistent memory-management approaches, which allows remote attackers to cause a denial of service (use-after-free error and application crash) via a crafted UMTS Radio Link Control packet. | 0 | 0 | NETWORK |
| CVE‑2014‑2282 | 2014‑03‑11 13:01:10 | MEDIUM (4) | The dissect_protocol_data_parameter function in epan/dissectors/packet-m3ua.c in the M3UA dissector in Wireshark 1.10.x before 1.10.6 does not properly allocate memory, which allows remote attackers to cause a denial of service (application crash) via a crafted SS7 MTP3 packet. | 0 | 0 | NETWORK |
| CVE‑2014‑2281 | 2014‑03‑11 13:01:10 | MEDIUM (4) | The nfs_name_snoop_add_name function in epan/dissectors/packet-nfs.c in the NFS dissector in Wireshark 1.8.x before 1.8.13 and 1.10.x before 1.10.6 does not validate a certain length value, which allows remote attackers to cause a denial of service (memory corruption and application crash) via a crafted NFS packet. | 0 | 0 | NETWORK |
| CVE‑2013‑7114 | 2013‑12‑19 22:55:05 | MEDIUM (5) | Multiple buffer overflows in the create_ntlmssp_v2_key function in epan/dissectors/packet-ntlmssp.c in the NTLMSSP v2 dissector in Wireshark 1.8.x before 1.8.12 and 1.10.x before 1.10.4 allow remote attackers to cause a denial of service (application crash) via a long domain name in a packet. | 0 | 0 | NETWORK |
| CVE‑2013‑7113 | 2013‑12‑19 22:55:05 | MEDIUM (5) | epan/dissectors/packet-bssgp.c in the BSSGP dissector in Wireshark 1.10.x before 1.10.4 incorrectly relies on a global variable, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑7112 | 2013‑12‑19 22:55:05 | MEDIUM (5) | The dissect_sip_common function in epan/dissectors/packet-sip.c in the SIP dissector in Wireshark 1.8.x before 1.8.12 and 1.10.x before 1.10.4 does not check for empty lines, which allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑6340 | 2013‑11‑04 16:55:05 | MEDIUM (4) | epan/dissectors/packet-tcp.c in the TCP dissector in Wireshark 1.8.x before 1.8.11 and 1.10.x before 1.10.3 does not properly determine the amount of remaining data, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑6339 | 2013‑11‑04 16:55:05 | MEDIUM (4) | The dissect_openwire_type function in epan/dissectors/packet-openwire.c in the OpenWire dissector in Wireshark 1.8.x before 1.8.11 and 1.10.x before 1.10.3 allows remote attackers to cause a denial of service (loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑6338 | 2013‑11‑04 16:55:05 | MEDIUM (4) | The dissect_sip_common function in epan/dissectors/packet-sip.c in the SIP dissector in Wireshark 1.8.x before 1.8.11 and 1.10.x before 1.10.3 does not properly initialize a data structure, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑6337 | 2013‑11‑04 16:55:05 | MEDIUM (4) | Unspecified vulnerability in the NBAP dissector in Wireshark 1.8.x before 1.8.11 and 1.10.x before 1.10.3 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑6336 | 2013‑11‑04 16:55:05 | MEDIUM (4) | The ieee802154_map_rec function in epan/dissectors/packet-ieee802154.c in the IEEE 802.15.4 dissector in Wireshark 1.8.x before 1.8.11 and 1.10.x before 1.10.3 uses an incorrect pointer chain, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑5722 | 2013‑09‑16 13:01:47 | MEDIUM (4) | Unspecified vulnerability in the LDAP dissector in Wireshark 1.8.x before 1.8.10 and 1.10.x before 1.10.2 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑5721 | 2013‑09‑16 13:01:47 | MEDIUM (4) | The dissect_mq_rr function in epan/dissectors/packet-mq.c in the MQ dissector in Wireshark 1.8.x before 1.8.10 and 1.10.x before 1.10.2 does not properly determine when to enter a certain loop, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑5720 | 2013‑09‑16 13:01:47 | MEDIUM (5) | Buffer overflow in the RTPS dissector in Wireshark 1.8.x before 1.8.10 and 1.10.x before 1.10.2 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑5719 | 2013‑09‑16 13:01:47 | MEDIUM (4) | epan/dissectors/packet-assa_r3.c in the ASSA R3 dissector in Wireshark 1.8.x before 1.8.10 and 1.10.x before 1.10.2 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑5718 | 2013‑09‑16 13:01:47 | MEDIUM (4) | The dissect_nbap_T_dCH_ID function in epan/dissectors/packet-nbap.c in the NBAP dissector in Wireshark 1.8.x before 1.8.10 and 1.10.x before 1.10.2 does not restrict the dch_id value, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑5717 | 2013‑09‑16 13:01:47 | MEDIUM (4) | The Bluetooth HCI ACL dissector in Wireshark 1.10.x before 1.10.2 does not properly maintain a certain free list, which allows remote attackers to cause a denial of service (application crash) via a crafted packet that is not properly handled by the wmem_block_alloc function in epan/wmem/wmem_allocator_block.c. | 0 | 0 | NETWORK |
| CVE‑2013‑4936 | 2013‑07‑30 00:56:16 | MEDIUM (5) | The IsDFP_Frame function in plugins/profinet/packet-pn-rt.c in the PROFINET Real-Time dissector in Wireshark 1.10.x before 1.10.1 does not validate MAC addresses, which allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4935 | 2013‑07‑30 00:56:16 | MEDIUM (4) | The dissect_per_length_determinant function in epan/dissectors/packet-per.c in the ASN.1 PER dissector in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 does not initialize a length field in certain abnormal situations, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4934 | 2013‑07‑30 00:56:16 | MEDIUM (4) | The netmon_open function in wiretap/netmon.c in the Netmon file parser in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 does not initialize certain structure members, which allows remote attackers to cause a denial of service (application crash) via a crafted packet-trace file. | 0 | 0 | NETWORK |
| CVE‑2013‑4933 | 2013‑07‑30 00:56:16 | MEDIUM (5) | The netmon_open function in wiretap/netmon.c in the Netmon file parser in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 does not properly allocate memory, which allows remote attackers to cause a denial of service (application crash) via a crafted packet-trace file. | 0 | 0 | NETWORK |
| CVE‑2013‑4932 | 2013‑07‑30 00:56:16 | MEDIUM (5) | Multiple array index errors in epan/dissectors/packet-gsm_a_common.c in the GSM A Common dissector in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 allow remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4931 | 2013‑07‑30 00:56:16 | MEDIUM (5) | epan/proto.c in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 allows remote attackers to cause a denial of service (loop) via a crafted packet that is not properly handled by the GSM RR dissector. | 0 | 0 | NETWORK |
| CVE‑2013‑4930 | 2013‑07‑30 00:56:16 | MEDIUM (5) | The dissect_dvbci_tpdu_hdr function in epan/dissectors/packet-dvbci.c in the DVB-CI dissector in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 does not validate a certain length value before decrementing it, which allows remote attackers to cause a denial of service (assertion failure and application exit) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4929 | 2013‑07‑30 00:56:16 | HIGH (8) | The parseFields function in epan/dissectors/packet-dis-pdus.c in the DIS dissector in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 does not terminate packet-data processing after finding zero remaining bytes, which allows remote attackers to cause a denial of service (loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4928 | 2013‑07‑30 00:56:16 | HIGH (8) | Integer signedness error in the dissect_headers function in epan/dissectors/packet-btobex.c in the Bluetooth OBEX dissector in Wireshark 1.10.x before 1.10.1 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4927 | 2013‑07‑30 00:56:16 | HIGH (8) | Integer signedness error in the get_type_length function in epan/dissectors/packet-btsdp.c in the Bluetooth SDP dissector in Wireshark 1.8.x before 1.8.9 and 1.10.x before 1.10.1 allows remote attackers to cause a denial of service (loop and CPU consumption) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4926 | 2013‑07‑30 00:56:16 | MEDIUM (5) | epan/dissectors/packet-dcom-sysact.c in the DCOM ISystemActivator dissector in Wireshark 1.10.x before 1.10.1 does not properly determine whether there is remaining packet data to process, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4925 | 2013‑07‑30 00:56:16 | MEDIUM (5) | Integer signedness error in epan/dissectors/packet-dcom-sysact.c in the DCOM ISystemActivator dissector in Wireshark 1.10.x before 1.10.1 allows remote attackers to cause a denial of service (assertion failure and daemon exit) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4924 | 2013‑07‑30 00:56:16 | MEDIUM (5) | epan/dissectors/packet-dcom-sysact.c in the DCOM ISystemActivator dissector in Wireshark 1.10.x before 1.10.1 does not properly validate certain index values, which allows remote attackers to cause a denial of service (assertion failure and application exit) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4923 | 2013‑07‑30 00:56:16 | MEDIUM (5) | Memory leak in the dissect_dcom_ActivationProperties function in epan/dissectors/packet-dcom-sysact.c in the DCOM ISystemActivator dissector in Wireshark 1.10.x before 1.10.1 allows remote attackers to cause a denial of service (memory consumption) via crafted packets. | 0 | 0 | NETWORK |
| CVE‑2013‑4922 | 2013‑07‑30 00:56:16 | MEDIUM (5) | Double free vulnerability in the dissect_dcom_ActivationProperties function in epan/dissectors/packet-dcom-sysact.c in the DCOM ISystemActivator dissector in Wireshark 1.10.x before 1.10.1 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4921 | 2013‑07‑30 00:56:16 | MEDIUM (5) | Off-by-one error in the dissect_radiotap function in epan/dissectors/packet-ieee80211-radiotap.c in the Radiotap dissector in Wireshark 1.10.x before 1.10.1 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4920 | 2013‑07‑30 00:56:14 | MEDIUM (5) | The P1 dissector in Wireshark 1.10.x before 1.10.1 does not properly initialize a global variable, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4083 | 2013‑06‑09 21:55:02 | MEDIUM (5) | The dissect_pft function in epan/dissectors/packet-dcp-etsi.c in the DCP ETSI dissector in Wireshark 1.6.x before 1.6.16, 1.8.x before 1.8.8, and 1.10.0 does not validate a certain fragment length value, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4082 | 2013‑06‑09 21:55:02 | MEDIUM (5) | The vwr_read function in wiretap/vwr.c in the Ixia IxVeriWave file parser in Wireshark 1.8.x before 1.8.8 does not validate the relationship between a record length and a trailer length, which allows remote attackers to cause a denial of service (heap-based buffer overflow and application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4081 | 2013‑06‑09 21:55:02 | MEDIUM (5) | The http_payload_subdissector function in epan/dissectors/packet-http.c in the HTTP dissector in Wireshark 1.6.x before 1.6.16 and 1.8.x before 1.8.8 does not properly determine when to use a recursive approach, which allows remote attackers to cause a denial of service (stack consumption) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4080 | 2013‑06‑09 21:55:02 | MEDIUM (5) | The dissect_r3_upstreamcommand_queryconfig function in epan/dissectors/packet-assa_r3.c in the Assa Abloy R3 dissector in Wireshark 1.8.x before 1.8.8 does not properly handle a zero-length item, which allows remote attackers to cause a denial of service (infinite loop, and CPU and memory consumption) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4079 | 2013‑06‑09 21:55:02 | MEDIUM (5) | The dissect_schedule_message function in epan/dissectors/packet-gsm_cbch.c in the GSM CBCH dissector in Wireshark 1.8.x before 1.8.8 allows remote attackers to cause a denial of service (infinite loop and application hang) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4078 | 2013‑06‑09 21:55:02 | MEDIUM (5) | epan/dissectors/packet-rdp.c in the RDP dissector in Wireshark 1.8.x before 1.8.8 does not validate return values during checks for data availability, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4077 | 2013‑06‑09 21:55:01 | MEDIUM (5) | Array index error in the NBAP dissector in Wireshark 1.8.x before 1.8.8 allows remote attackers to cause a denial of service (application crash) via a crafted packet, related to nbap.cnf and packet-nbap.c. | 0 | 0 | NETWORK |
| CVE‑2013‑4076 | 2013‑06‑09 21:55:01 | MEDIUM (5) | Buffer overflow in the dissect_iphc_crtp_fh function in epan/dissectors/packet-ppp.c in the PPP dissector in Wireshark 1.8.x before 1.8.8 allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4075 | 2013‑06‑09 21:55:01 | MEDIUM (5) | epan/dissectors/packet-gmr1_bcch.c in the GMR-1 BCCH dissector in Wireshark 1.8.x before 1.8.8 does not properly initialize memory, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑4074 | 2013‑06‑09 21:55:01 | MEDIUM (5) | The dissect_capwap_data function in epan/dissectors/packet-capwap.c in the CAPWAP dissector in Wireshark 1.6.x before 1.6.16 and 1.8.x before 1.8.8 incorrectly uses a -1 data value to represent an error condition, which allows remote attackers to cause a denial of service (application crash) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2013‑3562 | 2013‑05‑25 03:18:16 | MEDIUM (5) | Multiple integer signedness errors in the tvb_unmasked function in epan/dissectors/packet-websocket.c in the Websocket dissector in Wireshark 1.8.x before 1.8.7 allow remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2013‑3561 | 2013‑05‑25 03:18:16 | HIGH (8) | Multiple integer overflows in Wireshark 1.8.x before 1.8.7 allow remote attackers to cause a denial of service (loop or application crash) via a malformed packet, related to a crash of the Websocket dissector, an infinite loop in the MySQL dissector, and a large loop in the ETCH dissector. | 0 | 0 | NETWORK |
| CVE‑2013‑3560 | 2013‑05‑25 03:18:16 | MEDIUM (5) | The dissect_dsmcc_un_download function in epan/dissectors/packet-mpeg-dsmcc.c in the MPEG DSM-CC dissector in Wireshark 1.8.x before 1.8.7 uses an incorrect format string, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2013‑3559 | 2013‑05‑25 03:18:16 | MEDIUM (5) | epan/dissectors/packet-dcp-etsi.c in the DCP ETSI dissector in Wireshark 1.8.x before 1.8.7 uses incorrect integer data types, which allows remote attackers to cause a denial of service (integer overflow, and heap memory corruption or NULL pointer dereference, and application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2013‑3558 | 2013‑05‑25 03:18:16 | MEDIUM (5) | The dissect_ccp_bsdcomp_opt function in epan/dissectors/packet-ppp.c in the PPP CCP dissector in Wireshark 1.8.x before 1.8.7 does not terminate a bit-field list, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2013‑3557 | 2013‑05‑25 03:18:16 | MEDIUM (5) | The dissect_ber_choice function in epan/dissectors/packet-ber.c in the ASN.1 BER dissector in Wireshark 1.6.x before 1.6.15 and 1.8.x before 1.8.7 does not properly initialize a certain variable, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2013‑3556 | 2013‑05‑25 03:18:16 | MEDIUM (5) | The fragment_add_seq_common function in epan/reassemble.c in the ASN.1 BER dissector in Wireshark before r48943 has an incorrect pointer dereference during a comparison, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2013‑3555 | 2013‑05‑25 03:18:16 | MEDIUM (5) | epan/dissectors/packet-gtpv2.c in the GTPv2 dissector in Wireshark 1.8.x before 1.8.7 calls incorrect functions in certain contexts related to ciphers, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2013‑2488 | 2013‑03‑07 15:55:02 | MEDIUM (5) | The DTLS dissector in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6 does not validate the fragment offset before invoking the reassembly state machine, which allows remote attackers to cause a denial of service (application crash) via a large offset value that triggers write access to an invalid memory location. | 0 | 0 | NETWORK |
| CVE‑2013‑2487 | 2013‑03‑07 15:55:02 | HIGH (8) | epan/dissectors/packet-reload.c in the REsource LOcation And Discovery (aka RELOAD) dissector in Wireshark 1.8.x before 1.8.6 uses incorrect integer data types, which allows remote attackers to cause a denial of service (infinite loop) via crafted integer values in a packet, related to the (1) dissect_icecandidates, (2) dissect_kinddata, (3) dissect_nodeid_list, (4) dissect_storeans, (5) dissect_storereq, (6) dissect_storeddataspecifier, (7) dissect_fetchreq, (8) dissect_findans, (9) dissect_diagnosticinfo, (10) dissect_diagnosticresponse, (11) dissect_reload_messagecontents, and (12) dissect_reload_message functions, a different vulnerability than CVE-2013-2486. | 0 | 0 | NETWORK |
| CVE‑2013‑2486 | 2013‑03‑07 15:55:02 | MEDIUM (6) | The dissect_diagnosticrequest function in epan/dissectors/packet-reload.c in the REsource LOcation And Discovery (aka RELOAD) dissector in Wireshark 1.8.x before 1.8.6 uses an incorrect integer data type, which allows remote attackers to cause a denial of service (infinite loop) via crafted integer values in a packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2485 | 2013‑03‑07 15:55:02 | MEDIUM (6) | The FCSP dissector in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6 allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2484 | 2013‑03‑07 15:55:02 | LOW (3) | The CIMD dissector in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6 allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2483 | 2013‑03‑07 15:55:02 | LOW (3) | The acn_add_dmp_data function in epan/dissectors/packet-acn.c in the ACN dissector in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6 allows remote attackers to cause a denial of service (divide-by-zero error and application crash) via an invalid count value in ACN_DMP_ADT_D_RE DMP data. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2482 | 2013‑03‑07 15:55:02 | MEDIUM (6) | The AMPQ dissector in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6 allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2481 | 2013‑03‑07 15:55:02 | LOW (3) | Integer signedness error in the dissect_mount_dirpath_call function in epan/dissectors/packet-mount.c in the Mount dissector in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6, when nfs_file_name_snooping is enabled, allows remote attackers to cause a denial of service (application crash) via a negative length value. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2480 | 2013‑03‑07 15:55:02 | LOW (3) | The RTPS and RTPS2 dissectors in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6 allow remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2479 | 2013‑03‑07 15:55:02 | LOW (3) | The dissect_mpls_echo_tlv_dd_map function in epan/dissectors/packet-mpls-echo.c in the MPLS Echo dissector in Wireshark 1.8.x before 1.8.6 allows remote attackers to cause a denial of service (infinite loop) via invalid Sub-tlv data. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2478 | 2013‑03‑07 15:55:02 | LOW (3) | The dissect_server_info function in epan/dissectors/packet-ms-mms.c in the MS-MMS dissector in Wireshark 1.6.x before 1.6.14 and 1.8.x before 1.8.6 does not properly manage string lengths, which allows remote attackers to cause a denial of service (application crash) via a malformed packet that (1) triggers an integer overflow or (2) has embedded '\0' characters in a string. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2477 | 2013‑03‑07 15:55:01 | LOW (3) | The CSN.1 dissector in Wireshark 1.8.x before 1.8.6 does not properly manage function pointers, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2476 | 2013‑03‑07 15:55:01 | MEDIUM (6) | The dissect_hartip function in epan/dissectors/packet-hartip.c in the HART/IP dissector in Wireshark 1.8.x before 1.8.6 allows remote attackers to cause a denial of service (infinite loop) via a packet with a header that is too short. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑2475 | 2013‑03‑07 15:55:01 | LOW (3) | The TCP dissector in Wireshark 1.8.x before 1.8.6 allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1590 | 2013‑02‑03 01:55:08 | LOW (3) | Buffer overflow in the NTLMSSP dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1589 | 2013‑02‑03 01:55:08 | LOW (3) | Double free vulnerability in epan/proto.c in the dissection engine in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1588 | 2013‑02‑03 01:55:08 | LOW (3) | Multiple buffer overflows in the dissect_pft_fec_detailed function in the DCP-ETSI dissector in epan/dissectors/packet-dcp-etsi.c in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 allow remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1587 | 2013‑02‑03 01:55:08 | LOW (3) | The dissect_rohc_ir_packet function in epan/dissectors/packet-rohc.c in the ROHC dissector in Wireshark 1.8.x before 1.8.5 does not properly handle unknown profiles, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1586 | 2013‑02‑03 01:55:08 | LOW (3) | The fragment_set_tot_len function in epan/reassemble.c in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly determine the length of a reassembled packet for the DTLS dissector, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1585 | 2013‑02‑03 01:55:08 | LOW (3) | epan/tvbuff.c in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly validate certain length values for the MS-MMC dissector, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1584 | 2013‑02‑03 01:55:08 | LOW (3) | The dissect_version_5_and_6_primary_header function in epan/dissectors/packet-dtn.c in the DTN dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 accesses an inappropriate pointer, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1583 | 2013‑02‑03 01:55:07 | LOW (3) | The dissect_version_4_primary_header function in epan/dissectors/packet-dtn.c in the DTN dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 accesses an inappropriate pointer, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1582 | 2013‑02‑03 01:55:07 | LOW (3) | The dissect_clnp function in epan/dissectors/packet-clnp.c in the CLNP dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly manage an offset variable, which allows remote attackers to cause a denial of service (infinite loop or application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1581 | 2013‑02‑03 01:55:07 | LOW (3) | The dissect_pft_fec_detailed function in epan/dissectors/packet-dcp-etsi.c in the DCP-ETSI dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly handle fragment gaps, which allows remote attackers to cause a denial of service (loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1580 | 2013‑02‑03 01:55:07 | LOW (3) | The dissect_cmstatus_tlv function in plugins/docsis/packet-cmstatus.c in the DOCSIS CM-STATUS dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 uses an incorrect data type for a position variable, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1579 | 2013‑02‑03 01:55:07 | LOW (3) | The rtps_util_add_bitmap function in epan/dissectors/packet-rtps.c in the RTPS dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly implement certain nested loops for processing bitmap data, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1578 | 2013‑02‑03 01:55:07 | LOW (3) | The dissect_pw_eth_heuristic function in epan/dissectors/packet-pw-eth.c in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly handle apparent Ethernet address values at the beginning of MPLS data, which allows remote attackers to cause a denial of service (loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1577 | 2013‑02‑03 01:55:07 | LOW (3) | The dissect_sip_p_charging_func_addresses function in epan/dissectors/packet-sip.c in the SIP dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly handle offset data associated with a quoted string, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1576 | 2013‑02‑03 01:55:07 | LOW (3) | The dissect_sdp_media_attribute function in epan/dissectors/packet-sdp.c in the SDP dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly process crypto-suite parameters, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1575 | 2013‑02‑03 01:55:06 | LOW (3) | The dissect_r3_cmd_alarmconfigure function in epan/dissectors/packet-assa_r3.c in the R3 dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly handle a certain alarm length, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1574 | 2013‑02‑03 01:55:06 | LOW (3) | The dissect_bthci_eir_ad_data function in epan/dissectors/packet-bthci_cmd.c in the Bluetooth HCI dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 uses an incorrect data type for a counter variable, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1573 | 2013‑02‑03 01:55:06 | LOW (3) | The csnStreamDissector function in epan/dissectors/packet-csn1.c in the CSN.1 dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly handle a large number of padding bits, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2013‑1572 | 2013‑02‑03 01:55:06 | LOW (3) | The dissect_oampdu_event_notification function in epan/dissectors/packet-slowprotocols.c in the IEEE 802.3 Slow Protocols dissector in Wireshark 1.6.x before 1.6.13 and 1.8.x before 1.8.5 does not properly handle certain short lengths, which allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑6062 | 2012‑12‑05 11:57:20 | MEDIUM (5) | The dissect_rtcp_app function in epan/dissectors/packet-rtcp.c in the RTCP dissector in Wireshark 1.6.x before 1.6.12 and 1.8.x before 1.8.4 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | NETWORK |
| CVE‑2012‑6061 | 2012‑12‑05 11:57:20 | MEDIUM (5) | The dissect_wtp_common function in epan/dissectors/packet-wtp.c in the WTP dissector in Wireshark 1.6.x before 1.6.12 and 1.8.x before 1.8.4 uses an incorrect data type for a certain length field, which allows remote attackers to cause a denial of service (integer overflow and infinite loop) via a crafted value in a packet. | 0 | 0 | NETWORK |
| CVE‑2012‑6060 | 2012‑12‑05 11:57:20 | MEDIUM (5) | Integer overflow in the dissect_iscsi_pdu function in epan/dissectors/packet-iscsi.c in the iSCSI dissector in Wireshark 1.6.x before 1.6.12 and 1.8.x before 1.8.4 allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2012‑6059 | 2012‑12‑05 11:57:20 | MEDIUM (5) | The dissect_isakmp function in epan/dissectors/packet-isakmp.c in the ISAKMP dissector in Wireshark 1.6.x before 1.6.12 and 1.8.x before 1.8.4 uses an incorrect data structure to determine IKEv2 decryption parameters, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2012‑6058 | 2012‑12‑05 11:57:20 | MEDIUM (5) | Integer overflow in the dissect_icmpv6 function in epan/dissectors/packet-icmpv6.c in the ICMPv6 dissector in Wireshark 1.6.x before 1.6.12 and 1.8.x before 1.8.4 allows remote attackers to cause a denial of service (infinite loop) via a crafted Number of Sources value. | 0 | 0 | NETWORK |
| CVE‑2012‑6057 | 2012‑12‑05 11:57:20 | MEDIUM (5) | The dissect_eigrp_metric_comm function in epan/dissectors/packet-eigrp.c in the EIGRP dissector in Wireshark 1.8.x before 1.8.4 uses the wrong data type for a certain offset value, which allows remote attackers to cause a denial of service (integer overflow and infinite loop) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2012‑6056 | 2012‑12‑05 11:57:20 | MEDIUM (5) | Integer overflow in the dissect_sack_chunk function in epan/dissectors/packet-sctp.c in the SCTP dissector in Wireshark 1.8.x before 1.8.4 allows remote attackers to cause a denial of service (infinite loop) via a crafted Duplicate TSN count. | 0 | 0 | NETWORK |
| CVE‑2012‑6055 | 2012‑12‑05 11:57:20 | MEDIUM (5) | epan/dissectors/packet-3g-a11.c in the 3GPP2 A11 dissector in Wireshark 1.8.x before 1.8.4 allows remote attackers to cause a denial of service (infinite loop) via a zero value in a sub-type length field. | 0 | 0 | NETWORK |
| CVE‑2012‑6054 | 2012‑12‑05 11:57:20 | MEDIUM (5) | The dissect_sflow_245_address_type function in epan/dissectors/packet-sflow.c in the sFlow dissector in Wireshark 1.8.x before 1.8.4 does not properly handle length calculations for an invalid IP address type, which allows remote attackers to cause a denial of service (infinite loop) via a packet that is neither IPv4 nor IPv6. | 0 | 0 | NETWORK |
| CVE‑2012‑6053 | 2012‑12‑05 11:57:20 | MEDIUM (5) | epan/dissectors/packet-usb.c in the USB dissector in Wireshark 1.6.x before 1.6.12 and 1.8.x before 1.8.4 relies on a length field to calculate an offset value, which allows remote attackers to cause a denial of service (infinite loop) via a zero value for this field. | 0 | 0 | NETWORK |
| CVE‑2012‑6052 | 2012‑12‑05 11:57:20 | MEDIUM (5) | Wireshark 1.8.x before 1.8.4 allows remote attackers to obtain sensitive hostname information by reading pcap-ng files. | 0 | 0 | NETWORK |
| CVE‑2012‑5240 | 2012‑10‑04 19:55:01 | MEDIUM (6) | Buffer overflow in the dissect_tlv function in epan/dissectors/packet-ldp.c in the LDP dissector in Wireshark 1.8.x before 1.8.3 allows remote attackers to cause a denial of service (application crash) or possibly have unspecified other impact via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑5238 | 2012‑10‑04 19:55:01 | LOW (3) | epan/dissectors/packet-ppp.c in the PPP dissector in Wireshark 1.8.x before 1.8.3 uses incorrect OUI data structures during the decoding of (1) PPP and (2) LCP data, which allows remote attackers to cause a denial of service (assertion failure and application exit) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑5237 | 2012‑10‑04 19:55:01 | LOW (3) | The dissect_hsrp function in epan/dissectors/packet-hsrp.c in the HSRP dissector in Wireshark 1.8.x before 1.8.3 allows remote attackers to cause a denial of service (infinite loop) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4298 | 2012‑08‑16 10:38:09 | MEDIUM (5) | Integer signedness error in the vwr_read_rec_data_ethernet function in wiretap/vwr.c in the Ixia IxVeriWave file parser in Wireshark 1.8.x before 1.8.2 allows user-assisted remote attackers to execute arbitrary code via a crafted packet-trace file that triggers a buffer overflow. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4297 | 2012‑08‑16 10:38:09 | HIGH (8) | Buffer overflow in the dissect_gsm_rlcmac_downlink function in epan/dissectors/packet-gsm_rlcmac.c in the GSM RLC MAC dissector in Wireshark 1.6.x before 1.6.10 and 1.8.x before 1.8.2 allows remote attackers to execute arbitrary code via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4296 | 2012‑08‑16 10:38:09 | LOW (3) | Buffer overflow in epan/dissectors/packet-rtps2.c in the RTPS2 dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 allows remote attackers to cause a denial of service (CPU consumption) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4295 | 2012‑08‑16 10:38:09 | LOW (3) | Array index error in the channelised_fill_sdh_g707_format function in epan/dissectors/packet-erf.c in the ERF dissector in Wireshark 1.8.x before 1.8.2 might allow remote attackers to cause a denial of service (application crash) via a crafted speed (aka rate) value. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4294 | 2012‑08‑16 10:38:09 | MEDIUM (6) | Buffer overflow in the channelised_fill_sdh_g707_format function in epan/dissectors/packet-erf.c in the ERF dissector in Wireshark 1.8.x before 1.8.2 allows remote attackers to execute arbitrary code via a large speed (aka rate) value. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4293 | 2012‑08‑16 10:38:09 | LOW (3) | plugins/ethercat/packet-ecatmb.c in the EtherCAT Mailbox dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 does not properly handle certain integer fields, which allows remote attackers to cause a denial of service (application exit) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4292 | 2012‑08‑16 10:38:09 | LOW (3) | The dissect_stun_message function in epan/dissectors/packet-stun.c in the STUN dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 does not properly interact with key-destruction behavior in a certain tree library, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4291 | 2012‑08‑16 10:38:09 | LOW (3) | The CIP dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 allows remote attackers to cause a denial of service (memory consumption) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4290 | 2012‑08‑16 10:38:09 | LOW (3) | The CTDB dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 allows remote attackers to cause a denial of service (loop and CPU consumption) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4289 | 2012‑08‑16 10:38:09 | LOW (3) | epan/dissectors/packet-afp.c in the AFP dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 allows remote attackers to cause a denial of service (loop and CPU consumption) via a large number of ACL entries. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4288 | 2012‑08‑16 10:38:08 | LOW (3) | Integer overflow in the dissect_xtp_ecntl function in epan/dissectors/packet-xtp.c in the XTP dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 allows remote attackers to cause a denial of service (loop or application crash) via a large value for a span length. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4287 | 2012‑08‑16 10:38:08 | MEDIUM (5) | epan/dissectors/packet-mongo.c in the MongoDB dissector in Wireshark 1.8.x before 1.8.2 allows remote attackers to cause a denial of service (loop and CPU consumption) via a small value for a BSON document length. | 0 | 0 | NETWORK |
| CVE‑2012‑4286 | 2012‑08‑16 10:38:08 | MEDIUM (4) | The pcapng_read_packet_block function in wiretap/pcapng.c in the pcap-ng file parser in Wireshark 1.8.x before 1.8.2 allows user-assisted remote attackers to cause a denial of service (divide-by-zero error and application crash) via a crafted pcap-ng file. | 0 | 0 | NETWORK |
| CVE‑2012‑4285 | 2012‑08‑16 10:38:08 | LOW (3) | The dissect_pft function in epan/dissectors/packet-dcp-etsi.c in the DCP ETSI dissector in Wireshark 1.4.x before 1.4.15, 1.6.x before 1.6.10, and 1.8.x before 1.8.2 allows remote attackers to cause a denial of service (divide-by-zero error and application crash) via a zero-length message. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4049 | 2012‑07‑24 19:55:03 | LOW (3) | epan/dissectors/packet-nfs.c in the NFS dissector in Wireshark 1.4.x before 1.4.14, 1.6.x before 1.6.9, and 1.8.x before 1.8.1 allows remote attackers to cause a denial of service (loop and CPU consumption) via a crafted packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑4048 | 2012‑07‑24 19:55:01 | LOW (3) | The PPP dissector in Wireshark 1.4.x before 1.4.14, 1.6.x before 1.6.9, and 1.8.x before 1.8.1 allows remote attackers to cause a denial of service (invalid pointer dereference and application crash) via a crafted packet, as demonstrated by a usbmon dump. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑3826 | 2012‑06‑30 10:15:05 | LOW (3) | Multiple integer underflows in Wireshark 1.4.x before 1.4.13 and 1.6.x before 1.6.8 allow remote attackers to cause a denial of service (loop) via vectors related to the R3 dissector, a different vulnerability than CVE-2012-2392. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑3825 | 2012‑06‑30 10:15:05 | LOW (3) | Multiple integer overflows in Wireshark 1.4.x before 1.4.13 and 1.6.x before 1.6.8 allow remote attackers to cause a denial of service (infinite loop) via vectors related to the (1) BACapp and (2) Bluetooth HCI dissectors, a different vulnerability than CVE-2012-2392. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑3548 | 2012‑08‑30 22:55:06 | MEDIUM (4) | The dissect_drda function in epan/dissectors/packet-drda.c in Wireshark 1.6.x through 1.6.10 and 1.8.x through 1.8.2 allows remote attackers to cause a denial of service (infinite loop and CPU consumption) via a small value for a certain length field in a capture file. | 0 | 0 | NETWORK |
| CVE‑2012‑2394 | 2012‑06‑30 10:15:05 | LOW (3) | Wireshark 1.4.x before 1.4.13 and 1.6.x before 1.6.8 on the SPARC and Itanium platforms does not properly perform data alignment for a certain structure member, which allows remote attackers to cause a denial of service (application crash) via a (1) ICMP or (2) ICMPv6 Echo Request packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑2393 | 2012‑06‑30 10:15:05 | LOW (3) | epan/dissectors/packet-diameter.c in the DIAMETER dissector in Wireshark 1.4.x before 1.4.13 and 1.6.x before 1.6.8 does not properly construct certain array data structures, which allows remote attackers to cause a denial of service (application crash) via a crafted packet that triggers incorrect memory allocation. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑2392 | 2012‑06‑30 10:15:05 | LOW (3) | Wireshark 1.4.x before 1.4.13 and 1.6.x before 1.6.8 allows remote attackers to cause a denial of service (infinite loop) via vectors related to the (1) ANSI MAP, (2) ASF, (3) IEEE 802.11, (4) IEEE 802.3, and (5) LTP dissectors. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑1596 | 2012‑04‑11 10:39:27 | MEDIUM (5) | The mp2t_process_fragmented_payload function in epan/dissectors/packet-mp2t.c in the MP2T dissector in Wireshark 1.4.x before 1.4.12 and 1.6.x before 1.6.6 allows remote attackers to cause a denial of service (application crash) via a packet containing an invalid pointer value that triggers an incorrect memory-allocation attempt. | 0 | 0 | NETWORK |
| CVE‑2012‑1595 | 2012‑04‑11 10:39:27 | MEDIUM (4) | The pcap_process_pseudo_header function in wiretap/pcap-common.c in Wireshark 1.4.x before 1.4.12 and 1.6.x before 1.6.6 allows remote attackers to cause a denial of service (application crash) via a WTAP_ENCAP_ERF file containing an Extension or Multi-Channel header with an invalid pseudoheader size, related to the pcap and pcap-ng file parsers. | 0 | 0 | NETWORK |
| CVE‑2012‑1594 | 2012‑04‑11 10:39:27 | LOW (3) | epan/dissectors/packet-ieee80211.c in the IEEE 802.11 dissector in Wireshark 1.6.x before 1.6.6 allows remote attackers to cause a denial of service (infinite loop) via a crafted packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑1593 | 2012‑04‑11 10:39:27 | LOW (3) | epan/dissectors/packet-ansi_a.c in the ANSI A dissector in Wireshark 1.4.x before 1.4.12 and 1.6.x before 1.6.6 allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a malformed packet. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑0068 | 2012‑04‑11 10:39:26 | MEDIUM (4) | The lanalyzer_read function in wiretap/lanalyzer.c in Wireshark 1.4.x before 1.4.11 and 1.6.x before 1.6.5 allows remote attackers to cause a denial of service (application crash) via a Novell capture file containing a record that is too small. | 0 | 0 | NETWORK |
| CVE‑2012‑0067 | 2012‑04‑11 10:39:26 | MEDIUM (4) | wiretap/iptrace.c in Wireshark 1.4.x before 1.4.11 and 1.6.x before 1.6.5 allows remote attackers to cause a denial of service (application crash) via a long packet in an AIX iptrace file. | 0 | 0 | NETWORK |
| CVE‑2012‑0066 | 2012‑04‑11 10:39:26 | MEDIUM (4) | Wireshark 1.4.x before 1.4.11 and 1.6.x before 1.6.5 allows remote attackers to cause a denial of service (application crash) via a long packet in a (1) Accellent 5Views (aka .5vw) file, (2) I4B trace file, or (3) NETMON 2 capture file. | 0 | 0 | NETWORK |
| CVE‑2012‑0043 | 2012‑04‑11 10:39:26 | MEDIUM (6) | Buffer overflow in the reassemble_message function in epan/dissectors/packet-rlc.c in the RLC dissector in Wireshark 1.4.x before 1.4.11 and 1.6.x before 1.6.5 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a series of fragmented RLC packets. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑0042 | 2012‑04‑11 10:39:26 | LOW (3) | Wireshark 1.4.x before 1.4.11 and 1.6.x before 1.6.5 does not properly perform certain string conversions, which allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a crafted packet, related to epan/to_str.c. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2012‑0041 | 2012‑04‑11 10:39:26 | MEDIUM (4) | The dissect_packet function in epan/packet.c in Wireshark 1.4.x before 1.4.11 and 1.6.x before 1.6.5 allows remote attackers to cause a denial of service (application crash) via a long packet in a capture file, as demonstrated by an airopeek file. | 0 | 0 | NETWORK |
| CVE‑2011‑4102 | 2011‑11‑03 15:55:01 | MEDIUM (4) | Heap-based buffer overflow in the erf_read_header function in wiretap/erf.c in the ERF file parser in Wireshark 1.4.0 through 1.4.9 and 1.6.x before 1.6.3 allows remote attackers to cause a denial of service (application crash) via a malformed file. | 0 | 0 | NETWORK |
| CVE‑2011‑4101 | 2011‑11‑03 15:55:01 | MEDIUM (4) | The dissect_infiniband_common function in epan/dissectors/packet-infiniband.c in the Infiniband dissector in Wireshark 1.4.0 through 1.4.9 and 1.6.x before 1.6.3 allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2011‑4100 | 2011‑11‑03 15:55:01 | MEDIUM (4) | The csnStreamDissector function in epan/dissectors/packet-csn1.c in the CSN.1 dissector in Wireshark 1.6.x before 1.6.3 does not initialize a certain variable, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2011‑3484 | 2011‑09‑20 10:55:05 | MEDIUM (4) | The unxorFrame function in epan/dissectors/packet-opensafety.c in the OpenSafety dissector in Wireshark 1.6.x before 1.6.2 does not properly validate a certain frame size, which allows remote attackers to cause a denial of service (loop and application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2011‑3483 | 2011‑09‑20 10:55:05 | MEDIUM (4) | Wireshark 1.6.x before 1.6.2 allows remote attackers to cause a denial of service (application crash) via a malformed capture file that leads to an invalid root tvbuff, related to a "buffer exception handling vulnerability." | 0 | 0 | NETWORK |
| CVE‑2011‑3482 | 2011‑09‑20 10:55:05 | MEDIUM (4) | The csnStreamDissector function in epan/dissectors/packet-csn1.c in the CSN.1 dissector in Wireshark 1.6.x before 1.6.2 does not initialize a certain structure member, which allows remote attackers to cause a denial of service (application crash) via a malformed packet. | 0 | 0 | NETWORK |
| CVE‑2011‑3360 | 2011‑09‑20 10:55:05 | HIGH (9) | Untrusted search path vulnerability in Wireshark 1.4.x before 1.4.9 and 1.6.x before 1.6.2 allows local users to gain privileges via a Trojan horse Lua script in an unspecified directory. | 0 | 0 | NETWORK |
| CVE‑2011‑3266 | 2011‑08‑24 00:55:01 | LOW (3) | The proto_tree_add_item function in Wireshark 1.6.0 through 1.6.1 and 1.4.0 through 1.4.8, when the IKEv1 protocol dissector is used, allows user-assisted remote attackers to cause a denial of service (infinite loop) via vectors involving a malformed IKE packet and many items in a tree. | 0 | 0 | NETWORK |
| CVE‑2011‑2698 | 2011‑08‑23 21:55:02 | MEDIUM (4) | Off-by-one error in the elem_cell_id_aux function in epan/dissectors/packet-ansi_a.c in the ANSI MAP dissector in Wireshark 1.4.x before 1.4.8 and 1.6.x before 1.6.1 allows remote attackers to cause a denial of service (infinite loop) via an invalid packet. | 0 | 0 | NETWORK |
| CVE‑2011‑2597 | 2011‑07‑07 19:55:03 | MEDIUM (4) | The Lucent/Ascend file parser in Wireshark 1.2.x before 1.2.18, 1.4.x through 1.4.7, and 1.6.0 allows remote attackers to cause a denial of service (infinite loop) via malformed packets. | 0 | 0 | NETWORK |
| CVE‑2011‑2175 | 2011‑06‑06 19:55:03 | MEDIUM (4) | Integer underflow in the visual_read function in wiretap/visual.c in Wireshark 1.2.x before 1.2.17 and 1.4.x before 1.4.7 allows remote attackers to cause a denial of service (application crash) via a malformed Visual Networks file that triggers a heap-based buffer over-read. | 0 | 0 | NETWORK |
| CVE‑2011‑2174 | 2011‑06‑06 19:55:03 | MEDIUM (4) | Double free vulnerability in the tvb_uncompress function in epan/tvbuff.c in Wireshark 1.2.x before 1.2.17 and 1.4.x before 1.4.7 allows remote attackers to cause a denial of service (application crash) via a packet with malformed data that uses zlib compression. | 0 | 0 | NETWORK |
| CVE‑2011‑1959 | 2011‑06‑06 19:55:03 | MEDIUM (4) | The snoop_read function in wiretap/snoop.c in Wireshark 1.2.x before 1.2.17 and 1.4.x before 1.4.7 does not properly handle certain virtualizable buffers, which allows remote attackers to cause a denial of service (application crash) via a large length value in a snoop file that triggers a stack-based buffer over-read. | 0 | 0 | NETWORK |
| CVE‑2011‑1958 | 2011‑06‑06 19:55:03 | MEDIUM (4) | Wireshark 1.2.x before 1.2.17 and 1.4.x before 1.4.7 allows user-assisted remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a crafted Diameter dictionary file. | 0 | 0 | NETWORK |
| CVE‑2011‑1957 | 2011‑06‑06 19:55:03 | MEDIUM (4) | The dissect_dcm_main function in epan/dissectors/packet-dcm.c in the DICOM dissector in Wireshark 1.2.x before 1.2.17 and 1.4.x before 1.4.7 allows remote attackers to cause a denial of service (infinite loop) via an invalid PDU length. | 0 | 0 | NETWORK |
| CVE‑2011‑1956 | 2011‑06‑06 19:55:03 | MEDIUM (4) | The bytes_repr_len function in Wireshark 1.4.5 uses an incorrect pointer argument, which allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via arbitrary TCP traffic. | 0 | 0 | NETWORK |
| CVE‑2011‑1592 | 2011‑04‑29 22:55:03 | MEDIUM (4) | The NFS dissector in epan/dissectors/packet-nfs.c in Wireshark 1.4.x before 1.4.5 on Windows uses an incorrect integer data type during decoding of SETCLIENTID calls, which allows remote attackers to cause a denial of service (application crash) via a crafted .pcap file. | 0 | 0 | NETWORK |
| CVE‑2011‑1591 | 2011‑04‑29 22:55:03 | HIGH (9) | Stack-based buffer overflow in the DECT dissector in epan/dissectors/packet-dect.c in Wireshark 1.4.x before 1.4.5 allows remote attackers to execute arbitrary code via a crafted .pcap file. | 0 | 0 | NETWORK |
| CVE‑2011‑1590 | 2011‑04‑29 22:55:03 | MEDIUM (4) | The X.509if dissector in Wireshark 1.2.x before 1.2.16 and 1.4.x before 1.4.5 does not properly initialize certain global variables, which allows remote attackers to cause a denial of service (application crash) via a crafted .pcap file. | 0 | 0 | NETWORK |
| CVE‑2011‑1143 | 2011‑03‑03 01:00:02 | MEDIUM (4) | epan/dissectors/packet-ntlmssp.c in the NTLMSSP dissector in Wireshark before 1.4.4 allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via a crafted .pcap file. | 0 | 0 | NETWORK |
| CVE‑2011‑1142 | 2011‑03‑03 01:00:02 | MEDIUM (5) | Stack consumption vulnerability in the dissect_ber_choice function in the BER dissector in Wireshark 1.2.x through 1.2.15 and 1.4.x through 1.4.4 might allow remote attackers to cause a denial of service (infinite loop) via vectors involving self-referential ASN.1 CHOICE values. | 0 | 0 | NETWORK |
| CVE‑2011‑1141 | 2011‑03‑03 01:00:02 | MEDIUM (4) | epan/dissectors/packet-ldap.c in Wireshark 1.0.x, 1.2.0 through 1.2.14, and 1.4.0 through 1.4.3 allows remote attackers to cause a denial of service (memory consumption) via (1) a long LDAP filter string or (2) an LDAP filter string containing many elements. | 0 | 0 | NETWORK |
| CVE‑2011‑1140 | 2011‑03‑03 01:00:01 | MEDIUM (4) | Multiple stack consumption vulnerabilities in the dissect_ms_compressed_string and dissect_mscldap_string functions in Wireshark 1.0.x, 1.2.0 through 1.2.14, and 1.4.0 through 1.4.3 allow remote attackers to cause a denial of service (infinite recursion) via a crafted (1) SMB or (2) Connection-less LDAP (CLDAP) packet. | 0 | 0 | NETWORK |
| CVE‑2011‑1139 | 2011‑03‑03 01:00:01 | MEDIUM (4) | wiretap/pcapng.c in Wireshark 1.2.0 through 1.2.14 and 1.4.0 through 1.4.3 allows remote attackers to cause a denial of service (application crash) via a pcap-ng file that contains a large packet-length field. | 0 | 0 | NETWORK |
| CVE‑2011‑1138 | 2011‑03‑03 01:00:01 | MEDIUM (4) | Off-by-one error in the dissect_6lowpan_iphc function in packet-6lowpan.c in Wireshark 1.4.0 through 1.4.3 on 32-bit platforms allows remote attackers to cause a denial of service (application crash) via a malformed 6LoWPAN IPv6 packet. | 0 | 0 | NETWORK |
| CVE‑2011‑0713 | 2011‑03‑03 01:00:01 | MEDIUM (7) | Heap-based buffer overflow in wiretap/dct3trace.c in Wireshark 1.2.0 through 1.2.14 and 1.4.0 through 1.4.3 allows remote attackers to cause a denial of service (application crash) or possibly have unspecified other impact via a long record in a Nokia DCT3 trace file. | 0 | 0 | NETWORK |
| CVE‑2011‑0538 | 2011‑02‑08 22:00:02 | MEDIUM (7) | Wireshark 1.2.0 through 1.2.14, 1.4.0 through 1.4.3, and 1.5.0 frees an uninitialized pointer during processing of a .pcap file in the pcap-ng format, which allows remote attackers to cause a denial of service (memory corruption) or possibly have unspecified other impact via a malformed file. | 0 | 0 | NETWORK |
| CVE‑2011‑0445 | 2011‑01‑13 01:00:03 | MEDIUM (5) | The ASN.1 BER dissector in Wireshark 1.4.0 through 1.4.2 allows remote attackers to cause a denial of service (assertion failure) via crafted packets, as demonstrated by fuzz-2010-12-30-28473.pcap. | 0 | 0 | NETWORK |
| CVE‑2011‑0444 | 2011‑01‑13 01:00:03 | HIGH (10) | Buffer overflow in the MAC-LTE dissector (epan/dissectors/packet-mac-lte.c) in Wireshark 1.2.0 through 1.2.13 and 1.4.0 through 1.4.2 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a large number of RARs. | 0 | 0 | NETWORK |
| CVE‑2011‑0024 | 2011‑03‑28 16:55:04 | HIGH (9) | Heap-based buffer overflow in wiretap/pcapng.c in Wireshark before 1.2 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted capture file. | 0 | 0 | NETWORK |
| CVE‑2010‑4538 | 2011‑01‑07 19:00:19 | HIGH (9) | Buffer overflow in the sect_enttec_dmx_da function in epan/dissectors/packet-enttec.c in Wireshark 1.4.2 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted ENTTEC DMX packet with Run Length Encoding (RLE) compression. | 0 | 0 | NETWORK |
| CVE‑2010‑4301 | 2010‑11‑26 19:00:10 | MEDIUM (5) | epan/dissectors/packet-zbee-zcl.c in the ZigBee ZCL dissector in Wireshark 1.4.0 through 1.4.1 allows remote attackers to cause a denial of service (infinite loop) via a crafted ZCL packet, related to Discover Attributes. | 0 | 0 | NETWORK |
| CVE‑2010‑4300 | 2010‑11‑26 19:00:10 | HIGH (8) | Heap-based buffer overflow in the dissect_ldss_transfer function (epan/dissectors/packet-ldss.c) in the LDSS dissector in Wireshark 1.2.0 through 1.2.12 and 1.4.0 through 1.4.1 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via an LDSS packet with a long digest line that triggers memory corruption. | 0 | 0 | NETWORK |
| CVE‑2010‑3445 | 2010‑11‑26 19:00:08 | MEDIUM (5) | Stack consumption vulnerability in the dissect_ber_unknown function in epan/dissectors/packet-ber.c in the BER dissector in Wireshark 1.4.x before 1.4.1 and 1.2.x before 1.2.12 allows remote attackers to cause a denial of service (NULL pointer dereference and crash) via a long string in an unknown ASN.1/BER encoded packet, as demonstrated using SNMP. | 0 | 0 | NETWORK |
| CVE‑2010‑3133 | 2010‑08‑26 18:36:36 | HIGH (9) | Untrusted search path vulnerability in Wireshark 0.8.4 through 1.0.15 and 1.2.0 through 1.2.10 allows local users, and possibly remote attackers, to execute arbitrary code and conduct DLL hijacking attacks via a Trojan horse airpcap.dll, and possibly other DLLs, that is located in the same folder as a file that automatically launches Wireshark. | 0 | 0 | NETWORK |
| CVE‑2010‑2995 | 2010‑08‑13 18:43:27 | HIGH (10) | The SigComp Universal Decompressor Virtual Machine (UDVM) in Wireshark 0.10.8 through 1.0.14 and 1.2.0 through 1.2.9 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via vectors related to sigcomp-udvm.c and an off-by-one error, which triggers a buffer overflow, different vulnerabilities than CVE-2010-2287. | 0 | 0 | NETWORK |
| CVE‑2010‑2994 | 2010‑08‑13 18:43:27 | HIGH (10) | Stack-based buffer overflow in the ASN.1 BER dissector in Wireshark 0.10.13 through 1.0.14 and 1.2.0 through 1.2.9 has unknown impact and remote attack vectors. NOTE: this issue exists because of a CVE-2010-2284 regression. | 0 | 0 | NETWORK |
| CVE‑2010‑2993 | 2010‑08‑13 18:43:27 | MEDIUM (5) | The IPMI dissector in Wireshark 1.2.0 through 1.2.9 allows remote attackers to cause a denial of service (infinite loop) via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2010‑2992 | 2010‑08‑13 18:43:16 | MEDIUM (5) | packet-gsm_a_rr.c in the GSM A RR dissector in Wireshark 1.2.2 through 1.2.9 allows remote attackers to cause a denial of service (crash) via unknown vectors that trigger a NULL pointer dereference. | 0 | 0 | NETWORK |
| CVE‑2010‑2287 | 2010‑06‑15 14:04:27 | HIGH (8) | Buffer overflow in the SigComp Universal Decompressor Virtual Machine dissector in Wireshark 0.10.8 through 1.0.13 and 1.2.0 through 1.2.8 has unknown impact and remote attack vectors. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2010‑2286 | 2010‑06‑15 14:04:27 | LOW (3) | The SigComp Universal Decompressor Virtual Machine dissector in Wireshark 0.10.7 through 1.0.13 and 1.2.0 through 1.2.8 allows remote attackers to cause a denial of service (infinite loop) via unknown vectors. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2010‑2285 | 2010‑06‑15 14:04:26 | LOW (3) | The SMB PIPE dissector in Wireshark 0.8.20 through 1.0.13 and 1.2.0 through 1.2.8 allows remote attackers to cause a denial of service (NULL pointer dereference) via unknown vectors. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2010‑2284 | 2010‑06‑15 14:04:26 | HIGH (8) | Buffer overflow in the ASN.1 BER dissector in Wireshark 0.10.13 through 1.0.13 and 1.2.0 through 1.2.8 has unknown impact and remote attack vectors. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2010‑2283 | 2010‑06‑15 14:04:26 | LOW (3) | The SMB dissector in Wireshark 0.99.6 through 1.0.13, and 1.2.0 through 1.2.8 allows remote attackers to cause a denial of service (NULL pointer dereference) via unknown vectors. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2010‑1455 | 2010‑05‑12 11:46:31 | MEDIUM (4) | The DOCSIS dissector in Wireshark 0.9.6 through 1.0.12 and 1.2.0 through 1.2.7 allows user-assisted remote attackers to cause a denial of service (application crash) via a malformed packet trace file. | 0 | 0 | NETWORK |
| CVE‑2010‑0304 | 2010‑02‑03 18:30:01 | HIGH (8) | Multiple buffer overflows in the LWRES dissector in Wireshark 0.9.15 through 1.0.10 and 1.2.0 through 1.2.5 allow remote attackers to cause a denial of service (crash) via a malformed packet, as demonstrated using a stack-based buffer overflow to the dissect_getaddrsbyname_request function. | 0 | 0 | NETWORK |

Get the IT stuff done that nobody wants to do.
Patch more applications, achieve compliance, and prevent problems while reducing stress with Lavawall®.
Security First
A security tool by security auditors. From Passkeys and Argon2i to source validation and MVSP principles, Lavawall® has you covered.
Constant Improvement
More features and more security added nearly every day.
More patchable programs added every week
While Ninite and other patching tools have had the same patch offerings for decades, we're monitoring stats to keep adding the most useful prorgams.
Details matter
From wrapping TLS communications in extra encryption and uninstalling remote support tools when they aren't used to detailed statistical analysis of system and network performance, Lavawall® goes in-depth.
Chromium extensions and Notification Validation
Lavawall®p; goes beyond patches and breach detection. We also monitor for risky Chromium extensions and allowed notifications that might be part of a phishing or ransomware attack.
Extended Cloud Security
Extend the security features of Cloudflare, Microsoft, Google, Sophos, and other cloud providers to create a Lavawall® of protection
Secure Remote Management
Even if you used breached remote management tools like ScreenConnect through Lavawall® when it was vulnerable, your computers stayed safe because we only install the agent when it needs to be used.
Integrations and automation
Easily deploy, monitor, and analyze security tools like Huntress, AutoElevate, and Sophos. Magically gain details from ZenDesk, ConnectWise, Datto, Panorama9, Microsoft, and Google.
Human and automated support
Get immediate fixes, user notifications, admin notifications -- and even security-certified human level 3 support when our advanced statistical analysis confirms a problem or anomaly.
| 2025‑10‑02 | 1.0.82.360 | Processes and Packages improvements |
| 2025‑09‑23 | 1.0.79.357 | |
| 2025‑07‑16 | 1.0.42.320 | |
| 2025‑06‑13 | 1.0.14.292 | |
| 2025‑06‑03 | 1.0.2.280 | |
| 2025‑05‑12 | 0.12.77.264 | |
| 2025‑05‑07 | 0.12.76.263 | add tpm complience check and ensure consistent memory gathering in windows/linux/mac |
| 2025‑05‑05 | 0.12.74.261 | add tpm complience check and ensure consistent memory gathering in windows/linux/mac |
| 2025‑04‑23 | 0.12.68.255 | Uninstallation and update refinements |
| 2025‑04‑17 | 0.12.66.253 | Reliability improvements |
| 2025‑04‑15 | 0.12.65.252 | |
| 2025‑03‑27 | 0.12.64.251 | Add efficiency to package management system |
| 2025‑03‑10 | 0.12.60.247 | |
| 2025‑03‑04 | 0.12.58.245 | |
| 2025‑03‑03 | 0.12.57.244 | Add TPM complience check and ensure consistent memory gathering in windows/linux/mac |
| 2025‑02‑28 | 0.12.56.243 | Windows RAM reporting and persistent scalability framework enhancements |
| 2025‑02‑27 | 0.12.55.242 | Battery health refinements |
| 2025‑02‑26 | 0.12.54.241 | Add battery health statistics |
| 2025‑02‑26 | 0.12.53.240 | |
| 2025‑01‑29 | 0.12.35.222 | Risk score refinements |
| 2025‑01‑17 | 0.12.29.216 | Enhanced compliance and non-standard AV |
| 2025‑01‑13 | 0.12.28.215 | Improved process graphs |
| 2025‑01‑07 | 0.12.27.214 | Antivirus details, compliance |
| 2024‑12‑27 | 0.12.24.211 | |
| 2024‑12‑02 | 0.12.19.206 | |
| 2024‑11‑22 | 0.12.18.205 | |
| 2024‑10‑30 | 0.12.8.195 | Mac update refinements |
| 2024‑10‑25 | 0.12.3.190 | |
| 2024‑10‑21 | 0.12.0.187 | Macos implementaiton, linux and windows improvements |
| 2024‑10‑16 | 0.11.128.186 | Linux stats and system information improvements, improvements for application shutdown |
| 2024‑09‑12 | 0.11.113.171 | CPU Optimizations and Packages reliability improvements |
| 2024‑09‑05 | 0.11.106.164 | Phased deployment enhancements |
| 2024‑09‑04 | 0.11.103.161 | |
| 2024‑09‑02 | 0.11.102.160 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑30 | 0.11.99.157 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑29 | 0.11.98.156 | CPU utilization and console event optimization |
| 2024‑08‑28 | 0.11.97.155 | Reliability to detect unusual updates like redistributables. |
| 2024‑08‑27 | 0.11.96.154 | |
| 2024‑08‑26 | 0.11.95.153 | Faster response for reboot requests |
| 2024‑08‑20 | 0.11.92.150 | Additional package upgrade pre-requisites |
| 2024‑08‑15 | 0.11.89.147 | |
| 2024‑08‑06 | 0.11.87.145 | |
| 2024‑07‑26 | 0.11.83.141 | Add resiliency for MAC duplicates and uptime |
| 2024‑07‑25 | 0.11.82.140 | Changes to facilitate cross-platform use. Bitlocker and Windows key refinements |
| 2024‑07‑15 | 0.11.80.138 | Antivirus and temperature added to configuration checks |
| 2024‑07‑15 | 0.11.79.137 | Add configuration checks for execution policy and secure boot |
| 2024‑07‑11 | 0.11.77.135 | load balancing refinements |
| 2024‑07‑10 | 0.11.76.134 | Add additional load balancing and data residency capabilities, add randomness to recurring task timings to decrease server load |
| 2024‑07‑05 | 0.11.74.132 | changes to graph and residual work on user imporsonation |
| 2024‑07‑04 | 0.11.73.131 | Add configuration checks for execution policy and secure boot. |
| 2024‑05‑20 | 253 | Added cleanup of old .json files during a re-install |
| 2024‑05‑13 | 252 | Added apt-get update to install |
| 2024‑05‑06 | 248 | Allow restart to use /var/run/reboot-required if needrestart is not installed |
| 2024‑04‑22 | 239 | Improve internal update and version tracking |
| 2024‑04‑15 | 235 | Add support for Yum packages |
| 2024‑04‑08 | 233 | Align patching with Windows patch reporting |
| 2024‑04‑02 | 228 | Add support for needrestart |
| 2024‑03‑04 | 224 | Schedule restarts |
| 2024‑03‑25 | 221 | Add support for apt packages |
| 2024‑03‑18 | 212 | Implement release management |
| 2024‑03‑11 | 202 | Add user login monitoring |
| 2024‑03‑04 | 189 | Enhance installation reliability |
| 2024‑02‑26 | 187 | Exapand triggers to identify if the instance needs to be restarted |
| 2024‑02‑19 | 146 | Improve compatibility for non-AWS instances |
| 2024‑02‑14 | 138 | Add self-uninstall capabilities |
| 2024‑02‑12 | 135 | Enhance scheduling flexibility |
| 2024‑02‑07 | 132 | Add kernel version tracking |
| 2024‑02‑05 | 124 | Add device hash to cryptographic self-update script validation |
| 2024‑01‑29 | 107 | Enhance encryption of patch data |
| 2024‑01‑22 | 98 | Improve how available storage is calculated |
| 2024‑01‑15 | 97 | Move initial tasks from installation file to sub scripts |
| 2024‑05‑21 | 91 | Improve multi-distribution compatibility |
| 2024‑05‑21 | 79 | Improve encryption reliability |
| 2023‑12‑11 | 68 | Enhance cryptographic validation of new scripts before updating |
| 2023‑11‑20 | 62 | Add inner layer of AES encryption in case TLS inspection doesn't allow for a secure connection |
| 2023‑11‑27 | 56 | Additional base cases for resiliancy |
| 2023‑11‑20 | 54 | Additional headers added to authentication process during installation. |
| 2023‑11‑20 | 53 | Enhanced key management |
| 2023‑11‑15 | 51 | Add insecure installation parameter to allow installation in environments with TLS inspection or other machine-in-the-middle situations. |
| 2023‑11‑06 | 42 | Enhance redundant encryption during installation. |
| 2023‑10‑30 | 33 | Improve install-over compatibility |
| 2023‑10‑23 | 18 | Add reboot configuration and scheduling |
| 2023‑10‑23 | 17 | Add self-updating functionality. |
| 2023‑10‑16 | 15 | Add Linux patching information for apt |
| 2023‑10‑09 | 14 | Collect system information |
| 2023‑10‑09 | 13 | Add Linux distribution information |
| 2023‑09‑30 | 12 | Add memory monitoring |
| 2023‑09‑30 | 10 | Add hardware information |
| 2023‑09‑23 | 9 | Add AWS information |
| 2023‑09‑23 | 8 | Add customized schedule capability for configuration updates |
| 2023‑09‑23 | 7 | Add support for package monitoring using package and dpkg logs |
| 2023‑09‑16 | 6 | Add storage data configuration gathering |
| 2023‑09‑16 | 5 | Add CPU information |
Lavawall® was built from the ground up with these concerns and the Minimum Viable Secure Product requirements in mind.
Some of the controls we implemented include:
- PassKeys as the preferred primary authentication at no additional cost
- Single Sign-on using modern, maintained, and industry-standard protocols for all customers at no additional cost
- Multi-Factor Authentication as a non-negotiable default
- Encrypting communications the same way as TLS again within the TLS tunnel, so we can allow TLS inspection without breaking like Huntress or disclosing security vulnerabilities to eavesdroppers.
- Encouraging external vulnerability reports and customer testing
- Passwords checked against popular disclosed passwords, hashed before they leave your computer, and then stored using Argon2id
- Not requiring the use of passwords at all. We consider them a temporary backup authentication in case you can't use passkeys or SSO.
Lavawall® databases and front-end systems are hosted with AWS in Montréal, Québec, Canada.
We send emails through AWS in Ireland and dedicated servers in Calgary, Alberta, Canada.
We send text messages for additional identity verification through Twilio in the United States.
We store executables and pass requests through Cloudflare at your nearest edge location.
We use Cloudflare for risk management, turnstile, and web application firewall services.
We use LeadPages for landing pages.
We use Google and Facebook for analytics on our public-facing pages, but they do not have access to the console.
We integrate with third-party tools, such as Microsoft, Google, Huntress, Screen Connect, Axcient, and Datto in their respective locations. However, you must initiate these integrations through single sign-on or by enabling them in your Lavawall® console.
Active security by design
Lavawall® is under active development with the latest release on
5+
Interfaces
150+
Monitored Applications
7+
System Metrics
Actively manage your IT with Lavawall®
Patching
Updates Beyond Windows
Lavawall® prevents the 80% of breaches and failed audits due to missing patches and updates.
You can reduce application patching delays from 67 days to nearly immediate with the 150+ applications that Lavawall® monitors and patches.
Patch release monitoring
Monitor everything without having to select packages or “managed applications”
Patch impact classification
Standard and optional Windows patches
The above listing includes products that Lavawall® monitors through public information and/or proprietary statistical analysis.
Although we do have a partner relationship with some of the listed products and companies, they do not necessarily endorse Lavawall® or have integrations with our systems.
Learn More
Flexible Term; Flexible Service
Flexibility for your dynamic business
You need to get your arms around compliance and security and don't want to get locked into “high watermark” monthly invoices or multi-year contracts.
Pay-as-you-need monthly pricing
DIY, full management, and coaching options
CMMI, PCI, SOC2, Canadian Cybersecurity, Minimum Viable Secure Product, and other compliance support
Choose the plan that's right for you
Simple pricing. No hidden fees. Advanced features for you business.
Month
Annual
Get 2 months free with Annual!
DIY
Security-focused RMM
C$3.25 /computer/Month
C$32.50 /computer/Year
-
1 computer
or 1 of the following cloud integrations:
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
(each integration counts as 1 computer) -
150+ application patches
-
30-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall® support
-
Sophos MDR: C$13.50/desktopSophos MDR: C$162/desktop
-
Huntress: C$5.40/deviceHuntress: C$64.80/device
-
Available white-label support for end users
-
Level 3+ IT support for IT
-
Weekly IT coaching sessions
Managed Security & Support
Unlimited end-user support
C$160 /user/Month
C$1,600 /user/Year
-
1 computer/user
Additional devices charged at DIY prices -
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
-
150+ application patches
-
90-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall® support
-
Sophos MDR Essentials
-
Huntress
-
White-label email and phone support for end users
-
Level 3+ IT support for IT
-
Weekly IT coaching sessions
-
Automatic discount and upgrade to Support & Coaching after 15 users
Support & Coaching
Improve your IT performance
$2,250 /Month
$22,500 /Year
-
25 computers included
Additional computers charged at DIY prices -
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
-
150+ application patches
-
90-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall®-only support
-
Sophos MDR Essentials
-
Huntress
-
White-label email and phone support for 15 users included Additional: C$150/user Additional: C$1,500/user
-
L3 IT support for IT
-
Weekly IT coaching sessions
Frequently Asked Questions
If you can not find answer to your question in our FAQ, you can always contact us or email us. We will answer you shortly!
General Questions
- Two years after a missing Plex Media Server led to the LastPass breach, the
Remote Monitorign and Management (RMM) tools availabel for Manged IT Service Providers (MSPs)
still didn't monitor for it.
Going through industry-specific applications, we noticed many were missing from the big RMM and patching providers. MSPs, insurance providers, and organizations that put their cleints at risk need to know about these risks, which lead to the largest number of critical audit findings and breaches - After 20 years of writing the same audit findings about system configurations, Payment Card Industry (PCI) compliance, and missing patches, our technical co-founder wanted to make it easier fo avoid these findings
- The existing risk visibility tools for insurance underwriters took a shallow look at Internet-facing risks. They -- along with all businesses -- need a deeper view of the threats that could actually lead to breaches.
- Domain risks
- Operating System (OS) patches
- Application patches
- Network vulnerabilities
- Cloud vulnerabilities
- OS configurations
- Axcient*
- Cloudflare
- Connectwise Screen Connect
- Datto RMM
- FreshDesk*
- Huntress
- Microsoft 365
- Panorama9
- ZenDesk
You can use your own logo for the console and notifications. You can also use a CNAME to automatically brand your console.
Note: you cannot currently re-proxy the CNAME to Lavawall® through Cloudflare.
Privacy & Security
However, we do allow passwords and use passwords as part of the zero-knowledge encryption for your clients' sensitive data, such as Bitlocker keys and Personally-Identifiable Information (PII).
These passwords use Argon2id slow hashes with individual salts and peppers.
We have added an additional secure tunnel that mimics the TLS process within the public TLS tunnel. This extra tunnel provides authentication and privacy for the workstations and the Lavawall® servers to prevent attacks such as the one that took down Solar Winds.
Remote access is not enabled for read-only and audit situations.
Get In Touch
Have a quick question and don't want to talk? Send us a quick note with the form below and we'll reply within one business day.
NW Calgary:
ThreeShield Information Security Corporation
600 Crowfoot Crescent N.W., Suite 340
Calgary, Alberta
T3G 0B4
SE Calgary:
ThreeShield Information Security Corporation
105, 11500 - 29th St. SE
Calgary, Alberta
T2Z 3W9
Canada