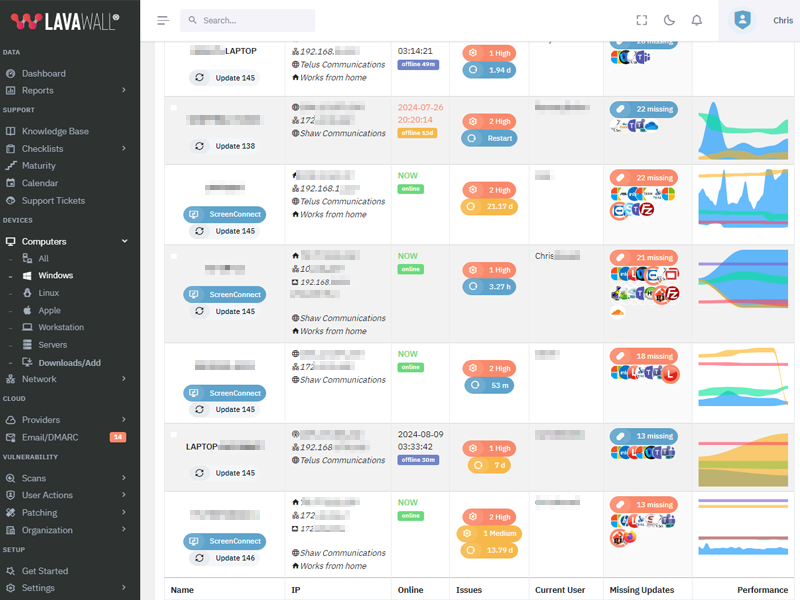
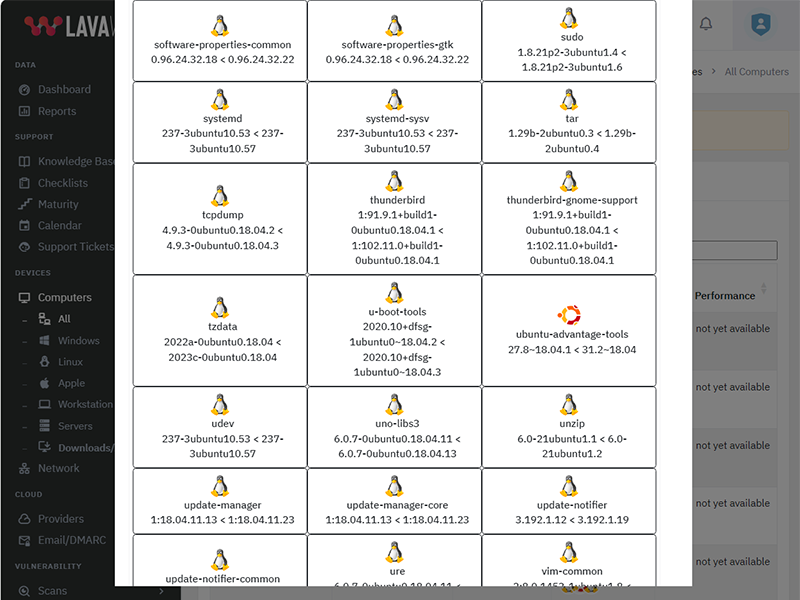
Update NVIDIA Graphics Driver to version 582.08
What patches are you missing?
CVE Vulnerabilities for NVIDIA Graphics Driver
| CVE | Published | Severity | Details | Exploitability | Impact | Vector |
| CVE‑2021‑1056 | 2021‑01‑08 01:15:15 | HIGH (7) | NVIDIA GPU Display Driver for Linux, all versions, contains a vulnerability in the kernel mode layer (nvidia.ko) in which it does not completely honor operating system file system permissions to provide GPU device-level isolation, which may lead to denial of service or information disclosure. | 2 | 5 | LOCAL |
| CVE‑2021‑1055 | 2021‑01‑08 01:15:15 | MEDIUM (5) | NVIDIA GPU Display Driver for Windows, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which improper access control may lead to denial of service and information disclosure. | 2 | 3 | LOCAL |
| CVE‑2021‑1054 | 2021‑01‑08 01:15:15 | MEDIUM (6) | NVIDIA GPU Display Driver for Windows, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which the software does not perform or incorrectly performs an authorization check when an actor attempts to access a resource or perform an action, which may lead to denial of service. | 2 | 4 | LOCAL |
| CVE‑2021‑1053 | 2021‑01‑08 01:15:14 | MEDIUM (6) | NVIDIA GPU Display Driver for Windows and Linux, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape or IOCTL in which improper validation of a user pointer may lead to denial of service. | 2 | 4 | LOCAL |
| CVE‑2021‑1052 | 2021‑01‑08 01:15:14 | HIGH (8) | NVIDIA GPU Display Driver for Windows and Linux, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape or IOCTL in which user-mode clients can access legacy privileged APIs, which may lead to denial of service, escalation of privileges, and information disclosure. | 2 | 6 | LOCAL |
| CVE‑2021‑1051 | 2021‑01‑08 01:15:14 | HIGH (8) | NVIDIA GPU Display Driver for Windows contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which a local user can get elevated privileges to modify display configuration data, which may result in denial of service of the display. | 2 | 6 | LOCAL |
| CVE‑2019‑5695 | 2019‑11‑12 21:15:12 | MEDIUM (7) | NVIDIA GeForce Experience (prior to 3.20.1) and Windows GPU Display Driver (all versions) contains a vulnerability in the local service provider component in which an attacker with local system and privileged access can incorrectly load Windows system DLLs without validating the path or signature (also known as a binary planting or DLL preloading attack), which may lead to denial of service or information disclosure through code execution. | 1 | 6 | LOCAL |
| CVE‑2019‑5694 | 2019‑11‑09 02:15:12 | MEDIUM (7) | NVIDIA Windows GPU Display Driver, R390 driver version, contains a vulnerability in NVIDIA Control Panel in which it incorrectly loads Windows system DLLs without validating the path or signature (also known as a binary planting or DLL preloading attack), which may lead to denial of service or information disclosure through code execution. The attacker requires local system access. | 1 | 6 | LOCAL |
| CVE‑2019‑5693 | 2019‑11‑09 02:15:12 | MEDIUM (6) | NVIDIA Windows GPU Display Driver, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) in which the program accesses or uses a pointer that has not been initialized, which may lead to denial of service. | 2 | 4 | LOCAL |
| CVE‑2019‑5692 | 2019‑11‑09 02:15:12 | HIGH (8) | NVIDIA Windows GPU Display Driver, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which the product uses untrusted input when calculating or using an array index, which may lead to escalation of privileges or denial of service. | 2 | 6 | LOCAL |
| CVE‑2019‑5691 | 2019‑11‑09 02:15:12 | HIGH (8) | NVIDIA Windows GPU Display Driver, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which a NULL pointer is dereferenced, which may lead to denial of service or escalation of privileges. | 2 | 6 | LOCAL |
| CVE‑2019‑5690 | 2019‑11‑09 02:15:12 | HIGH (8) | NVIDIA Windows GPU Display Driver, all versions, contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which the size of an input buffer is not validated, which may lead to denial of service or escalation of privileges. | 2 | 6 | LOCAL |
| CVE‑2019‑5687 | 2019‑08‑06 20:15:13 | LOW (4) | NVIDIA Windows GPU Display Driver (all versions) contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which an incorrect use of default permissions for an object exposes it to an unintended actor | 0 | 0 | LOCAL |
| CVE‑2019‑5686 | 2019‑08‑06 20:15:13 | MEDIUM (5) | NVIDIA Windows GPU Display Driver (all versions) contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which the software uses an API function or data structure in a way that relies on properties that are not always guaranteed to be valid, which may lead to denial of service. | 0 | 0 | LOCAL |
| CVE‑2019‑5685 | 2019‑08‑06 20:15:13 | HIGH (10) | NVIDIA Windows GPU Display Driver (all versions) contains a vulnerability in DirectX drivers, in which a specially crafted shader can cause an out of bounds access to a shader local temporary array, which may lead to denial of service or code execution. | 0 | 0 | NETWORK |
| CVE‑2019‑5684 | 2019‑08‑06 20:15:13 | HIGH (10) | NVIDIA Windows GPU Display Driver (all versions) contains a vulnerability in DirectX drivers, in which a specially crafted shader can cause an out of bounds access of an input texture array, which may lead to denial of service or code execution. | 0 | 0 | NETWORK |
| CVE‑2019‑5683 | 2019‑08‑06 20:15:12 | HIGH (7) | NVIDIA Windows GPU Display Driver (all versions) contains a vulnerability in the user mode video driver trace logger component. When an attacker has access to the system and creates a hard link, the software does not check for hard link attacks. This behavior may lead to code execution, denial of service, or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2019‑5677 | 2019‑05‑10 21:29:01 | MEDIUM (5) | NVIDIA Windows GPU Display driver software for Windows (all versions) contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DeviceIoControl where the software reads from a buffer using buffer access mechanisms such as indexes or pointers that reference memory locations after the targeted buffer, which may lead to denial of service. | 0 | 0 | LOCAL |
| CVE‑2019‑5675 | 2019‑05‑10 21:29:01 | HIGH (7) | NVIDIA Windows GPU Display driver software for Windows (all versions) contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where the product does not properly synchronize shared data, such as static variables across threads, which can lead to undefined behavior and unpredictable data changes, which may lead to denial of service, escalation of privileges, or information disclosure. | 0 | 0 | LOCAL |
| CVE‑2019‑5671 | 2019‑02‑27 23:29:01 | MEDIUM (5) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape in which the software does not release a resource after its effective lifetime has ended, which may lead to denial of service. | 0 | 0 | LOCAL |
| CVE‑2019‑5670 | 2019‑02‑27 23:29:01 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler for DxgkDdiEscape in which the software uses a sequential operation to read from or write to a buffer, but it uses an incorrect length value that causes it to access memory that is outside of the bounds of the buffer which may lead to denial of service, escalation of privileges, code execution or information disclosure. | 0 | 0 | LOCAL |
| CVE‑2019‑5669 | 2019‑02‑27 23:29:01 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler for DxgkDdiEscape in which the software uses a sequential operation to read from or write to a buffer, but it uses an incorrect length value that causes it to access memory that is outside of the bounds of the buffer, which may lead to denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2019‑5668 | 2019‑02‑27 23:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiSubmitCommandVirtual in which the application dereferences a pointer that it expects to be valid, but is NULL, which may lead to denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2019‑5667 | 2019‑02‑27 23:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiSetRootPageTable in which the application dereferences a pointer that it expects to be valid, but is NULL, which may lead to code execution, denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2019‑5666 | 2019‑02‑27 23:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) create context command DDI DxgkDdiCreateContext in which the product uses untrusted input when calculating or using an array index, but the product does not validate or incorrectly validates the index to ensure the index references a valid position within the array, which may lead to denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2019‑5665 | 2019‑02‑27 23:29:00 | HIGH (7) | NVIDIA Windows GPU Display driver contains a vulnerability in the 3D vision component in which the stereo service software, when opening a file, does not check for hard links. This behavior may lead to code execution, denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2018‑6260 | 2018‑11‑13 17:29:00 | LOW (2) | NVIDIA graphics driver contains a vulnerability that may allow access to application data processed on the GPU through a side channel exposed by the GPU performance counters. Local user access is required. This is not a network or remote attack vector. | 0 | 0 | LOCAL |
| CVE‑2018‑6253 | 2018‑04‑02 16:29:01 | MEDIUM (5) | NVIDIA GPU Display Driver contains a vulnerability in the DirectX and OpenGL Usermode drivers where a specially crafted pixel shader can cause infinite recursion leading to denial of service. | 0 | 0 | LOCAL |
| CVE‑2018‑6252 | 2018‑04‑02 16:29:01 | MEDIUM (5) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler for DxgkDdiEscape where the software allows an actor access to restricted functionality that is unnecessary to production usage, and which may result in denial of service. | 0 | 0 | LOCAL |
| CVE‑2018‑6251 | 2018‑04‑02 16:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the DirectX 10 Usermode driver, where a specially crafted pixel shader can cause writing to unallocated memory, leading to denial of service or potential code execution. | 0 | 0 | LOCAL |
| CVE‑2018‑6250 | 2018‑04‑02 16:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a NULL pointer dereference occurs which may lead to denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2018‑6249 | 2018‑04‑02 16:29:00 | HIGH (7) | NVIDIA GPU Display Driver contains a vulnerability in kernel mode layer handler where a NULL pointer dereference may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2018‑6248 | 2018‑04‑02 16:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler for DxgkDdiEscape where the software uses a sequential operation to read or write a buffer, but it uses an incorrect length value that causes it to access memory that is outside of the bounds of the buffer which may lead to denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2018‑6247 | 2018‑04‑02 16:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a NULL pointer dereference may lead to denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6277 | 2017‑09‑22 17:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a value passed from a user to the driver is not correctly validated and used as the index to an array which may lead to denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6272 | 2017‑09‑22 17:29:00 | HIGH (7) | NVIDIA GPU Display Driver contains a vulnerability in the kernel mode layer handler where a value passed from a user to the driver is not correctly validated and used as the index to an array which may lead to a denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6271 | 2017‑09‑22 17:29:00 | MEDIUM (5) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler for DxgkDdiCreateAllocation where untrusted user input is used as a divisor without validation while processing block linear information which may lead to a potential divide by zero and denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑6270 | 2017‑09‑22 17:29:00 | MEDIUM (5) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler for DxgkDdiCreateAllocation where untrusted user input is used as a divisor without validation during a calculation which may lead to a potential divide by zero and denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑6269 | 2017‑09‑22 17:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a pointer passed from a user to the driver is used without validation which may lead to denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6268 | 2017‑09‑22 17:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a value passed from a user to the driver is not correctly validated and used as the index to an array which may lead to denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6267 | 2017‑09‑22 17:29:00 | MEDIUM (5) | NVIDIA GPU Display Driver contains a vulnerability in the kernel mode layer handler where an incorrect initialization of internal objects can cause an infinite loop which may lead to a denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑6266 | 2017‑09‑22 17:29:00 | MEDIUM (5) | NVIDIA GPU Display Driver contains a vulnerability in the kernel mode layer handler where improper access controls could allow unprivileged users to cause a denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑6260 | 2017‑07‑28 19:29:00 | MEDIUM (5) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer helper function where an incorrect calculation of string length may lead to denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑6259 | 2017‑07‑28 19:29:00 | HIGH (7) | NVIDIA GPU Display Driver contains a vulnerability in the kernel mode layer handler where an incorrect detection and recovery from an invalid state produced by specific user actions may lead to denial of service. | 0 | 0 | NETWORK |
| CVE‑2017‑6257 | 2017‑07‑28 19:29:00 | HIGH (7) | NVIDIA GPU Display Driver contains a vulnerability in the kernel mode layer handler where a NULL pointer dereference may lead to denial of service or potential escalation of privileges | 0 | 0 | LOCAL |
| CVE‑2017‑6256 | 2017‑07‑28 19:29:00 | MEDIUM (5) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a value passed from a user to the driver is not correctly validated and used as the index to an array which may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6255 | 2017‑07‑28 19:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where an improper input parameter handling may lead to a denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6254 | 2017‑07‑28 19:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a pointer passed from an user to the driver is used without validation which may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6253 | 2017‑07‑28 19:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where the size of an input buffer is not validated which may lead to denial of service or potential escalation of privileges | 0 | 0 | LOCAL |
| CVE‑2017‑6252 | 2017‑07‑28 19:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler where a NULL pointer dereference may lead to a denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑6251 | 2017‑07‑28 19:29:00 | HIGH (7) | NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer handler where a missing permissions check may allow users to gain access to arbitrary physical system memory, which may lead to an escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0355 | 2017‑05‑09 21:29:01 | MEDIUM (5) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer handler for DxgkDdiEscape where it may access paged memory while holding a spinlock, leading to a denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑0354 | 2017‑05‑09 21:29:01 | MEDIUM (5) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer handler for DxgkDdiEscape where a call to certain function requiring lower IRQL can be made under raised IRQL which may lead to a denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑0353 | 2017‑05‑09 21:29:01 | MEDIUM (5) | All versions of the NVIDIA GPU Display Driver contain a vulnerability in the kernel mode layer handler for DxgDdiEscape where due to improper locking on certain conditions may lead to a denial of service | 0 | 0 | LOCAL |
| CVE‑2017‑0352 | 2017‑05‑09 21:29:01 | HIGH (7) | All versions of the NVIDIA GPU Display Driver contain a vulnerability in the GPU firmware where incorrect access control may allow CPU access sensitive GPU control registers, leading to an escalation of privileges | 0 | 0 | LOCAL |
| CVE‑2017‑0351 | 2017‑05‑09 21:29:01 | HIGH (7) | All versions of the NVIDIA GPU Display Driver contain a vulnerability in the kernel mode layer handler where a NULL pointer dereference caused by invalid user input may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0350 | 2017‑05‑09 21:29:01 | HIGH (7) | All versions of the NVIDIA GPU Display Driver contain a vulnerability in the kernel mode layer handler where a value passed from a user to the driver is not correctly validated and used in an offset calculation may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0349 | 2017‑05‑09 21:29:01 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a pointer passed from a user to the driver is not correctly validated before it is dereferenced for a write operation, may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0348 | 2017‑05‑09 21:29:00 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler where a NULL pointer dereference may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0347 | 2017‑05‑09 21:29:00 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a value passed from a user to the driver is not correctly validated and used as the index to an array, which may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0346 | 2017‑05‑09 21:29:00 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where the size of an input buffer is not validated, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0345 | 2017‑05‑09 21:29:00 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where user provided input used as an array size is not correctly validated allows out of bound access in kernel memory and may lead to denial of service or potential escalation of privileges | 0 | 0 | LOCAL |
| CVE‑2017‑0344 | 2017‑05‑09 21:29:00 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape may allow users to gain access to arbitrary physical memory, leading to escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0343 | 2017‑05‑09 21:29:00 | MEDIUM (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) where user can trigger a race condition due to lack of synchronization in two functions leading to a denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0342 | 2017‑05‑09 21:29:00 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler where incorrect calculation may cause an invalid address access leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0341 | 2017‑05‑09 21:29:00 | HIGH (7) | All versions of the NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where user provided input can trigger an access to a pointer that has not been initialized which may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0324 | 2017‑02‑15 23:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where the size of an input buffer is not validated, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0323 | 2017‑02‑15 23:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer handler where a NULL pointer dereference caused by invalid user input may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0322 | 2017‑02‑15 23:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler where a value passed from a user to the driver is not correctly validated and used as the index to an array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0321 | 2017‑02‑15 23:59:01 | HIGH (7) | All versions of NVIDIA GPU Display Driver contain a vulnerability in the kernel mode layer handler where a NULL pointer dereference caused by invalid user input may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0320 | 2017‑02‑15 23:59:00 | MEDIUM (5) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer handler where improper handling of values may cause a denial of service on the system. | 0 | 0 | LOCAL |
| CVE‑2017‑0319 | 2017‑02‑15 23:59:00 | MEDIUM (5) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer handler where improper handling of values may cause a denial of service on the system. | 0 | 0 | LOCAL |
| CVE‑2017‑0318 | 2017‑02‑15 23:59:00 | MEDIUM (5) | All versions of NVIDIA Linux GPU Display Driver contain a vulnerability in the kernel mode layer handler where improper validation of an input parameter may cause a denial of service on the system. | 0 | 0 | LOCAL |
| CVE‑2017‑0317 | 2017‑02‑15 23:59:00 | MEDIUM (7) | All versions of NVIDIA GPU and GeForce Experience installer contain a vulnerability where it fails to set proper permissions on the package extraction path thus allowing a non-privileged user to tamper with the extracted files, potentially leading to escalation of privileges via code execution. | 0 | 0 | LOCAL |
| CVE‑2017‑0315 | 2017‑02‑15 23:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where an attempt to access an invalid object pointer may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0314 | 2017‑02‑15 23:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) implementation of the SubmitCommandVirtual DDI (DxgkDdiSubmitCommandVirtual) where untrusted input is used to reference memory outside of the intended boundary of the buffer leading to denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0313 | 2017‑02‑15 23:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) implementation of the SubmitCommandVirtual DDI (DxgkDdiSubmitCommandVirtual) where untrusted input is used to reference memory outside of the intended boundary of the buffer leading to denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0312 | 2017‑02‑15 23:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscapeID 0x100008b where user provided input is used as the limit for a loop may lead to denial of service or potential escalation of privileges | 0 | 0 | LOCAL |
| CVE‑2017‑0311 | 2017‑02‑15 23:59:00 | HIGH (7) | NVIDIA GPU Display Driver R378 contains a vulnerability in the kernel mode layer handler where improper access control may lead to denial of service or possible escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0310 | 2017‑02‑15 23:59:00 | MEDIUM (5) | All versions of NVIDIA GPU Display Driver contain a vulnerability in the kernel mode layer handler where improper access controls allowing unprivileged user to cause a denial of service. | 0 | 0 | LOCAL |
| CVE‑2017‑0309 | 2017‑02‑15 23:59:00 | HIGH (7) | All versions of NVIDIA GPU Display Driver contain a vulnerability in the kernel mode layer handler where multiple integer overflows may cause improper memory allocation leading to a denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2017‑0308 | 2017‑02‑15 23:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where untrusted input is used for buffer size calculation leading to denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8826 | 2016‑12‑16 21:59:01 | MEDIUM (5) | All versions of NVIDIA GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys for Windows or nvidia.ko for Linux) where a user can cause a GPU interrupt storm, leading to a denial of service. | 0 | 0 | LOCAL |
| CVE‑2016‑8825 | 2016‑12‑16 21:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where the size of an input buffer is not validated, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8824 | 2016‑12‑16 21:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where improper access controls allow a regular user to write a part of the registry intended for privileged users only, leading to escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8823 | 2016‑12‑16 21:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer handler for DxgDdiEscape where the size of an input buffer is not validated leading to a denial of service or possible escalation of privileges | 0 | 0 | LOCAL |
| CVE‑2016‑8822 | 2016‑12‑16 21:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x600000E, 0x600000F, and 0x6000010 where a value passed from a user to the driver is used without validation as the index to an internal array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8821 | 2016‑12‑16 21:59:01 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer handler for DxgDdiEscape where improper access controls may allow a user to access arbitrary physical memory, leading to an escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8820 | 2016‑12‑16 21:59:00 | MEDIUM (6) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where a check on a function return value is missing, potentially allowing an uninitialized value to be used as the source of a strcpy() call, leading to denial of service or information disclosure. | 0 | 0 | LOCAL |
| CVE‑2016‑8819 | 2016‑12‑16 21:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape where a handle to a kernel object may be returned to the user, leading to possible denial of service or escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8818 | 2016‑12‑16 21:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where a pointer passed from a user to the driver is used without validation, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8817 | 2016‑12‑16 21:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where a value passed from a user to the driver is used without validation as the size input to memcpy(), causing a buffer overflow, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8816 | 2016‑12‑16 21:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where a value passed from a user to the driver is used without validation as the index to an array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8815 | 2016‑12‑16 21:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where a value passed from a user to the driver is used without validation as the index to an array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8814 | 2016‑12‑16 21:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where multiple pointers are used without checking for NULL, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8813 | 2016‑12‑16 21:59:00 | HIGH (7) | All versions of NVIDIA Windows GPU Display Driver contain a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where multiple pointers are used without checking for NULL, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8811 | 2016‑11‑08 20:59:25 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x7000170 where the size of an input buffer is not validated, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8810 | 2016‑11‑08 20:59:24 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x100009a where a value passed from an user to the driver is used without validation as the index to an internal array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8809 | 2016‑11‑08 20:59:23 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x70001b2 where the size of an input buffer is not validated, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8808 | 2016‑11‑08 20:59:22 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x70000d5 where a value passed from an user to the driver is used without validation as the index to an internal array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8807 | 2016‑11‑08 20:59:21 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x10000e9 where a value is passed from an user to the driver is used without validation as the size input to memcpy() causing a stack buffer overflow, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8806 | 2016‑11‑08 20:59:20 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x5000027 where a pointer passed from an user to the driver is used without validation, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑8805 | 2016‑11‑08 20:59:19 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x7000014 where a value passed from an user to the driver is used without validation as the index to an internal array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7391 | 2016‑11‑08 20:59:18 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x100010b where a missing array bounds check can allow a user to write to kernel memory, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7390 | 2016‑11‑08 20:59:17 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x7000194 where a value passed from a user to the driver is used without validation as the index to an internal array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7389 | 2016‑11‑08 20:59:16 | HIGH (7) | For the NVIDIA Quadro, NVS, GeForce, and Tesla products, NVIDIA GPU Display Driver on Linux R304 before 304.132, R340 before 340.98, R367 before 367.55, R361_93 before 361.93.03, and R370 before 370.28 contains a vulnerability in the kernel mode layer (nvidia.ko) handler for mmap() where improper input validation may allow users to gain access to arbitrary physical memory, leading to an escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7388 | 2016‑11‑08 20:59:15 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler where a NULL pointer dereference caused by invalid user input may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7387 | 2016‑11‑08 20:59:13 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x600000D where a value passed from a user to the driver is used without validation as the index to an internal array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7386 | 2016‑11‑08 20:59:12 | LOW (2) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x70000D4 which may lead to leaking of kernel memory contents to user space through an uninitialized buffer. | 0 | 0 | LOCAL |
| CVE‑2016‑7385 | 2016‑11‑08 20:59:11 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape ID 0x700010d where a value passed from a user to the driver is used without validation as the index to an internal array, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7384 | 2016‑11‑08 20:59:10 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) where unchecked input/output lengths in UVMLiteController Device IO Control handling may lead to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7383 | 2016‑11‑08 20:59:09 | MEDIUM (6) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in a memory mapping API in the kernel mode layer (nvlddmkm.sys) handler, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7382 | 2016‑11‑08 20:59:08 | HIGH (7) | For the NVIDIA Quadro, NVS, GeForce, and Tesla products, NVIDIA GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys for Windows or nvidia.ko for Linux) handler where a missing permissions check may allow users to gain access to arbitrary physical memory, leading to an escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑7381 | 2016‑11‑08 20:59:07 | HIGH (7) | For the NVIDIA Quadro, NVS, and GeForce products, NVIDIA Windows GPU Display Driver R340 before 342.00 and R375 before 375.63 contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgDdiEscape where a user input to index an array is not bounds checked, leading to denial of service or potential escalation of privileges. | 0 | 0 | LOCAL |
| CVE‑2016‑5025 | 2016‑11‑08 20:59:05 | MEDIUM (6) | For the NVIDIA Quadro, NVS, and GeForce products, improper sanitization of parameters in the NVAPI support layer causes a denial of service vulnerability (blue screen crash) within the NVIDIA Windows graphics drivers. | 0 | 0 | LOCAL |
| CVE‑2016‑4959 | 2016‑11‑08 20:59:01 | HIGH (8) | For the NVIDIA Quadro, NVS, and GeForce products, there is a Remote Desktop denial of service. A successful exploit of a vulnerable system will result in a kernel null pointer dereference, causing a blue screen crash. | 0 | 0 | NETWORK |
| CVE‑2015‑8328 | 2015‑11‑24 20:59:23 | MEDIUM (7) | Unspecified vulnerability in the NVAPI support layer in the NVIDIA GPU graphics driver R340 before 341.92, R352 before 354.35, and R358 before 358.87 on Windows allows local users to obtain sensitive information, cause a denial of service (crash), or possibly gain privileges via unknown vectors. NOTE: this identifier was SPLIT from CVE-2015-7869 per ADT2 and ADT3 due to different vulnerability types and affected versions. | 0 | 0 | LOCAL |
| CVE‑2015‑7869 | 2015‑11‑24 20:59:14 | MEDIUM (7) | Multiple integer overflows in the kernel mode driver for the NVIDIA GPU graphics driver R340 before 341.92, R352 before 354.35, and R358 before 358.87 on Windows and R304 before 304.131, R340 before 340.96, R352 before 352.63, and R358 before 358.16 on Linux allow local users to obtain sensitive information, cause a denial of service (crash), or possibly gain privileges via unknown vectors, which trigger uninitialized or out of bounds memory access. NOTE: this identifier has been SPLIT per ADT2 and ADT3 due to different vulnerability type and affected versions. See CVE-2015-8328 for the vulnerability in the NVAPI support layer in NVIDIA drivers for Windows. | 0 | 0 | LOCAL |
| CVE‑2015‑7866 | 2015‑11‑24 20:59:12 | HIGH (7) | Unquoted Windows search path vulnerability in the Smart Maximize Helper (nvSmartMaxApp.exe) in the Control Panel in the NVIDIA GPU graphics driver R340 before 341.92, R352 before 354.35, and R358 before 358.87 on Windows allows local users to gain privileges via a Trojan horse application, as demonstrated by C:\Program.exe. | 0 | 0 | LOCAL |
| CVE‑2015‑7865 | 2015‑11‑24 20:59:11 | HIGH (8) | nvSCPAPISvr.exe in the Stereoscopic 3D Driver Service in the NVIDIA GPU graphics driver R340 before 341.92, R352 before 354.35, and R358 before 358.87 on Windows does not properly restrict access to the stereosvrpipe named pipe, which allows local users to gain privileges via a commandline in a number 2 command, which is stored in the HKEY_LOCAL_MACHINE explorer Run registry key, a different vulnerability than CVE-2011-4784. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2015‑5950 | 2015‑09‑30 01:59:17 | MEDIUM (7) | The NVIDIA display driver R352 before 353.82 and R340 before 341.81 on Windows; R304 before 304.128, R340 before 340.93, and R352 before 352.41 on Linux; and R352 before 352.46 on GRID vGPU and vSGA allows local users to write to an arbitrary kernel memory location and consequently gain privileges via a crafted ioctl call. | 0 | 0 | LOCAL |
| CVE‑2015‑5053 | 2015‑11‑24 20:59:02 | HIGH (10) | The host memory mapping path feature in the NVIDIA GPU graphics driver R346 before 346.87 and R352 before 352.41 for Linux and R352 before 352.46 for GRID vGPU and vSGA does not properly restrict access to third-party device IO memory, which allows attackers to gain privileges, cause a denial of service (resource consumption), or possibly have unspecified other impact via unknown vectors related to the follow_pfn kernel-mode API call. | 0 | 0 | NETWORK |
| CVE‑2015‑3625 | 2015‑07‑18 00:59:00 | HIGH (7) | The NVIDIA GPU driver for FreeBSD R352 before 352.09, 346 before 346.72, R349 before 349.16, R343 before 343.36, R340 before 340.76, R337 before 337.25, R334 before 334.21, R331 before 331.113, and R304 before 304.125 allows local users with certain permissions to read or write arbitrary kernel memory via unspecified vectors that trigger an untrusted pointer dereference. | 0 | 0 | LOCAL |
| CVE‑2014‑8298 | 2014‑12‑10 15:59:17 | HIGH (8) | The NVIDIA Linux Discrete GPU drivers before R304.125, R331.x before R331.113, R340.x before R340.65, R343.x before R343.36, and R346.x before R346.22, Linux for Tegra (L4T) driver before R21.2, and Chrome OS driver before R40 allows remote attackers to cause a denial of service (segmentation fault and X server crash) or possibly execute arbitrary code via a crafted GLX indirect rendering protocol request. | 0 | 0 | NETWORK |
| CVE‑2013‑5987 | 2014‑01‑21 18:55:10 | HIGH (7) | Unspecified vulnerability in NVIDIA graphics driver Release 331, 325, 319, 310, and 304 allows local users to bypass intended access restrictions for the GPU and gain privileges via unknown vectors. | 0 | 0 | LOCAL |
| CVE‑2013‑5986 | 2014‑01‑21 18:55:10 | HIGH (10) | Unspecified vulnerability in NVIDIA graphics driver Release 331, 325, 319, 310, and 304 has unknown impact and attack vectors, a different vulnerability than CVE-2013-5987. | 0 | 0 | NETWORK |
| CVE‑2013‑0131 | 2013‑04‑08 16:55:02 | HIGH (7) | Buffer overflow in the NVIDIA GPU driver before 304.88, 310.x before 310.44, and 313.x before 313.30 for the X Window System on UNIX, when NoScanout mode is enabled, allows remote authenticated users to execute arbitrary code via a large ARGB cursor. | 0 | 0 | NETWORK |

Get the IT stuff done that nobody wants to do.
Patch more applications, achieve compliance, and prevent problems while reducing stress with Lavawall®.
Security First
A security tool by security auditors. From Passkeys and Argon2i to source validation and MVSP principles, Lavawall® has you covered.
Constant Improvement
More features and more security added nearly every day.
More patchable programs added every week
While Ninite and other patching tools have had the same patch offerings for decades, we're monitoring stats to keep adding the most useful prorgams.
Details matter
From wrapping TLS communications in extra encryption and uninstalling remote support tools when they aren't used to detailed statistical analysis of system and network performance, Lavawall® goes in-depth.
Chromium extensions and Notification Validation
Lavawall®p; goes beyond patches and breach detection. We also monitor for risky Chromium extensions and allowed notifications that might be part of a phishing or ransomware attack.
Extended Cloud Security
Extend the security features of Cloudflare, Microsoft, Google, Sophos, and other cloud providers to create a Lavawall® of protection
Secure Remote Management
Even if you used breached remote management tools like ScreenConnect through Lavawall® when it was vulnerable, your computers stayed safe because we only install the agent when it needs to be used.
Integrations and automation
Easily deploy, monitor, and analyze security tools like Huntress, AutoElevate, and Sophos. Magically gain details from ZenDesk, ConnectWise, Datto, Panorama9, Microsoft, and Google.
Human and automated support
Get immediate fixes, user notifications, admin notifications -- and even security-certified human level 3 support when our advanced statistical analysis confirms a problem or anomaly.
| 2026‑02‑12 | 1.0.104.382 | Processes and Packages improvements |
| 2026‑02‑10 | 1.0.100.378 | Processes and Packages improvements |
| 2025‑10‑02 | 1.0.82.360 | Processes and Packages improvements |
| 2025‑09‑23 | 1.0.79.357 | |
| 2025‑07‑16 | 1.0.42.320 | |
| 2025‑06‑13 | 1.0.14.292 | |
| 2025‑06‑03 | 1.0.2.280 | |
| 2025‑05‑12 | 0.12.77.264 | |
| 2025‑05‑07 | 0.12.76.263 | add tpm complience check and ensure consistent memory gathering in windows/linux/mac |
| 2025‑05‑05 | 0.12.74.261 | add tpm complience check and ensure consistent memory gathering in windows/linux/mac |
| 2025‑04‑23 | 0.12.68.255 | Uninstallation and update refinements |
| 2025‑04‑17 | 0.12.66.253 | Reliability improvements |
| 2025‑04‑15 | 0.12.65.252 | |
| 2025‑03‑27 | 0.12.64.251 | Add efficiency to package management system |
| 2025‑03‑10 | 0.12.60.247 | |
| 2025‑03‑04 | 0.12.58.245 | |
| 2025‑03‑03 | 0.12.57.244 | Add TPM complience check and ensure consistent memory gathering in windows/linux/mac |
| 2025‑02‑28 | 0.12.56.243 | Windows RAM reporting and persistent scalability framework enhancements |
| 2025‑02‑27 | 0.12.55.242 | Battery health refinements |
| 2025‑02‑26 | 0.12.54.241 | Add battery health statistics |
| 2025‑02‑26 | 0.12.53.240 | |
| 2025‑01‑29 | 0.12.35.222 | Risk score refinements |
| 2025‑01‑17 | 0.12.29.216 | Enhanced compliance and non-standard AV |
| 2025‑01‑13 | 0.12.28.215 | Improved process graphs |
| 2025‑01‑07 | 0.12.27.214 | Antivirus details, compliance |
| 2024‑12‑27 | 0.12.24.211 | |
| 2024‑12‑02 | 0.12.19.206 | |
| 2024‑11‑22 | 0.12.18.205 | |
| 2024‑10‑30 | 0.12.8.195 | Mac update refinements |
| 2024‑10‑25 | 0.12.3.190 | |
| 2024‑10‑21 | 0.12.0.187 | Macos implementaiton, linux and windows improvements |
| 2024‑10‑16 | 0.11.128.186 | Linux stats and system information improvements, improvements for application shutdown |
| 2024‑09‑12 | 0.11.113.171 | CPU Optimizations and Packages reliability improvements |
| 2024‑09‑05 | 0.11.106.164 | Phased deployment enhancements |
| 2024‑09‑04 | 0.11.103.161 | |
| 2024‑09‑02 | 0.11.102.160 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑30 | 0.11.99.157 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑29 | 0.11.98.156 | CPU utilization and console event optimization |
| 2024‑08‑28 | 0.11.97.155 | Reliability to detect unusual updates like redistributables. |
| 2024‑08‑27 | 0.11.96.154 | |
| 2024‑08‑26 | 0.11.95.153 | Faster response for reboot requests |
| 2024‑08‑20 | 0.11.92.150 | Additional package upgrade pre-requisites |
| 2024‑08‑15 | 0.11.89.147 | |
| 2024‑08‑06 | 0.11.87.145 | |
| 2024‑07‑26 | 0.11.83.141 | Add resiliency for MAC duplicates and uptime |
| 2024‑07‑25 | 0.11.82.140 | Changes to facilitate cross-platform use. Bitlocker and Windows key refinements |
| 2024‑07‑15 | 0.11.80.138 | Antivirus and temperature added to configuration checks |
| 2024‑07‑15 | 0.11.79.137 | Add configuration checks for execution policy and secure boot |
| 2024‑07‑11 | 0.11.77.135 | load balancing refinements |
| 2024‑07‑10 | 0.11.76.134 | Add additional load balancing and data residency capabilities, add randomness to recurring task timings to decrease server load |
| 2024‑05‑20 | 253 | Added cleanup of old .json files during a re-install |
| 2024‑05‑13 | 252 | Added apt-get update to install |
| 2024‑05‑06 | 248 | Allow restart to use /var/run/reboot-required if needrestart is not installed |
| 2024‑04‑22 | 239 | Improve internal update and version tracking |
| 2024‑04‑15 | 235 | Add support for Yum packages |
| 2024‑04‑08 | 233 | Align patching with Windows patch reporting |
| 2024‑04‑02 | 228 | Add support for needrestart |
| 2024‑03‑04 | 224 | Schedule restarts |
| 2024‑03‑25 | 221 | Add support for apt packages |
| 2024‑03‑18 | 212 | Implement release management |
| 2024‑03‑11 | 202 | Add user login monitoring |
| 2024‑03‑04 | 189 | Enhance installation reliability |
| 2024‑02‑26 | 187 | Exapand triggers to identify if the instance needs to be restarted |
| 2024‑02‑19 | 146 | Improve compatibility for non-AWS instances |
| 2024‑02‑14 | 138 | Add self-uninstall capabilities |
| 2024‑02‑12 | 135 | Enhance scheduling flexibility |
| 2024‑02‑07 | 132 | Add kernel version tracking |
| 2024‑02‑05 | 124 | Add device hash to cryptographic self-update script validation |
| 2024‑01‑29 | 107 | Enhance encryption of patch data |
| 2024‑01‑22 | 98 | Improve how available storage is calculated |
| 2024‑01‑15 | 97 | Move initial tasks from installation file to sub scripts |
| 2024‑05‑21 | 91 | Improve multi-distribution compatibility |
| 2024‑05‑21 | 79 | Improve encryption reliability |
| 2023‑12‑11 | 68 | Enhance cryptographic validation of new scripts before updating |
| 2023‑11‑20 | 62 | Add inner layer of AES encryption in case TLS inspection doesn't allow for a secure connection |
| 2023‑11‑27 | 56 | Additional base cases for resiliancy |
| 2023‑11‑20 | 54 | Additional headers added to authentication process during installation. |
| 2023‑11‑20 | 53 | Enhanced key management |
| 2023‑11‑15 | 51 | Add insecure installation parameter to allow installation in environments with TLS inspection or other machine-in-the-middle situations. |
| 2023‑11‑06 | 42 | Enhance redundant encryption during installation. |
| 2023‑10‑30 | 33 | Improve install-over compatibility |
| 2023‑10‑23 | 18 | Add reboot configuration and scheduling |
| 2023‑10‑23 | 17 | Add self-updating functionality. |
| 2023‑10‑16 | 15 | Add Linux patching information for apt |
| 2023‑10‑09 | 14 | Collect system information |
| 2023‑10‑09 | 13 | Add Linux distribution information |
| 2023‑09‑30 | 12 | Add memory monitoring |
| 2023‑09‑30 | 10 | Add hardware information |
| 2023‑09‑23 | 9 | Add AWS information |
| 2023‑09‑23 | 8 | Add customized schedule capability for configuration updates |
| 2023‑09‑23 | 7 | Add support for package monitoring using package and dpkg logs |
| 2023‑09‑16 | 6 | Add storage data configuration gathering |
| 2023‑09‑16 | 5 | Add CPU information |
Lavawall® was built from the ground up with these concerns and the Minimum Viable Secure Product requirements in mind.
Some of the controls we implemented include:
- PassKeys as the preferred primary authentication at no additional cost
- Single Sign-on using modern, maintained, and industry-standard protocols for all customers at no additional cost
- Multi-Factor Authentication as a non-negotiable default
- Encrypting communications the same way as TLS again within the TLS tunnel, so we can allow TLS inspection without breaking like Huntress or disclosing security vulnerabilities to eavesdroppers.
- Encouraging external vulnerability reports and customer testing
- Passwords checked against popular disclosed passwords, hashed before they leave your computer, and then stored using Argon2id
- Not requiring the use of passwords at all. We consider them a temporary backup authentication in case you can't use passkeys or SSO.
Lavawall® databases and front-end systems are hosted with AWS in Montréal, Québec, Canada.
We send emails through AWS in Ireland and dedicated servers in Calgary, Alberta, Canada.
We send text messages for additional identity verification through Twilio in the United States.
We store executables and pass requests through Cloudflare at your nearest edge location.
We use Cloudflare for risk management, turnstile, and web application firewall services.
We use LeadPages for landing pages.
We use Google and Facebook for analytics on our public-facing pages, but they do not have access to the console.
We integrate with third-party tools, such as Microsoft, Google, Huntress, Screen Connect, Axcient, and Datto in their respective locations. However, you must initiate these integrations through single sign-on or by enabling them in your Lavawall® console.
Active security by design
Lavawall® is under active development with the latest release on
5+
Interfaces
150+
Monitored Applications
7+
System Metrics
Actively manage your IT with Lavawall®
Patching
Updates Beyond Windows
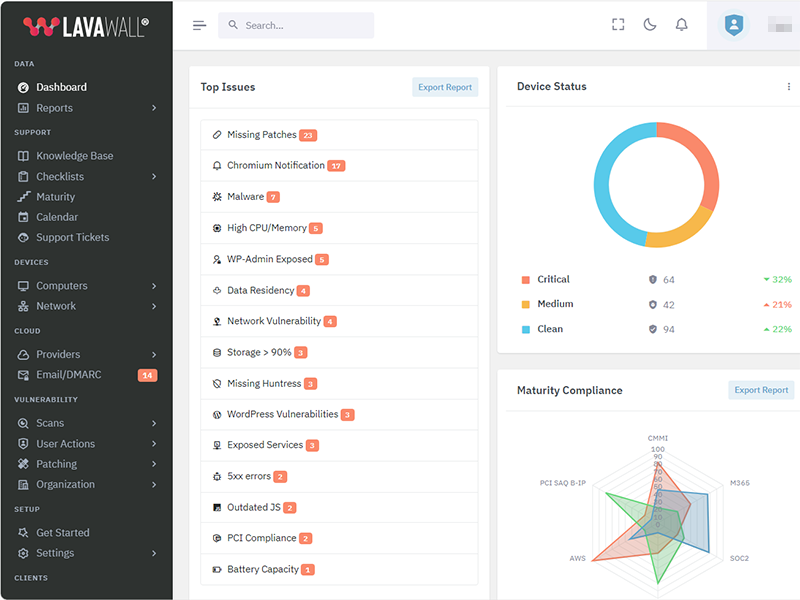
Lavawall® prevents the 80% of breaches and failed audits due to missing patches and updates.
You can reduce application patching delays from 67 days to nearly immediate with the 150+ applications that Lavawall® monitors and patches.
Patch release monitoring
Monitor everything without having to select packages or “managed applications”
Patch impact classification
Standard and optional Windows patches
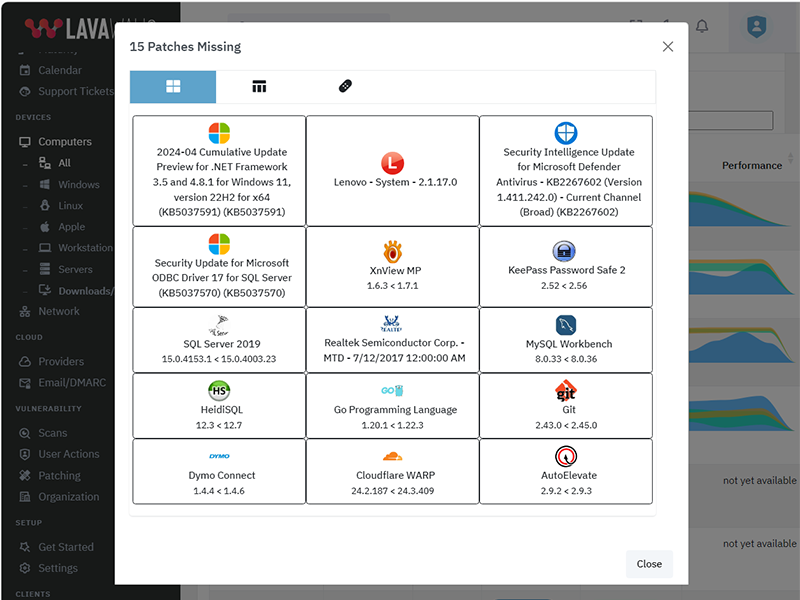
The above listing includes products that Lavawall® monitors through public information and/or proprietary statistical analysis.
Although we do have a partner relationship with some of the listed products and companies, they do not necessarily endorse Lavawall® or have integrations with our systems.
Learn More
Flexible Term; Flexible Service
Flexibility for your dynamic business
You need to get your arms around compliance and security and don't want to get locked into “high watermark” monthly invoices or multi-year contracts.
Pay-as-you-need monthly pricing
DIY, full management, and coaching options
CMMI, PCI, SOC2, Canadian Cybersecurity, Minimum Viable Secure Product, and other compliance support
Choose the plan that's right for you
Simple pricing. No hidden fees. Advanced features for you business.
Month
Annual
Get 2 months free with Annual!
DIY
Security-focused RMM
C$3.25 /computer/Month
C$32.50 /computer/Year
-
1 computer
or 1 of the following cloud integrations:
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
(each integration counts as 1 computer) -
150+ application patches
-
30-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall® support
-
Sophos MDR: C$13.50/desktopSophos MDR: C$162/desktop
-
Huntress: C$5.40/deviceHuntress: C$64.80/device
-
Available white-label support for end users
-
Level 3+ IT support for IT
-
Weekly IT coaching sessions
Managed Security & Support
Unlimited end-user support
C$160 /user/Month
C$1,600 /user/Year
-
1 computer/user
Additional devices charged at DIY prices -
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
-
150+ application patches
-
90-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall® support
-
Sophos MDR Essentials
-
Huntress
-
White-label email and phone support for end users
-
Level 3+ IT support for IT
-
Weekly IT coaching sessions
-
Automatic discount and upgrade to Support & Coaching after 15 users
Support & Coaching
Improve your IT performance
$2,250 /Month
$22,500 /Year
-
25 computers included
Additional computers charged at DIY prices -
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
-
150+ application patches
-
90-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall®-only support
-
Sophos MDR Essentials
-
Huntress
-
White-label email and phone support for 15 users included Additional: C$150/user Additional: C$1,500/user
-
L3 IT support for IT
-
Weekly IT coaching sessions
Frequently Asked Questions
If you can not find answer to your question in our FAQ, you can always contact us or email us. We will answer you shortly!
General Questions
- Two years after a missing Plex Media Server led to the LastPass breach, the
Remote Monitorign and Management (RMM) tools availabel for Manged IT Service Providers (MSPs)
still didn't monitor for it.
Going through industry-specific applications, we noticed many were missing from the big RMM and patching providers. MSPs, insurance providers, and organizations that put their cleints at risk need to know about these risks, which lead to the largest number of critical audit findings and breaches - After 20 years of writing the same audit findings about system configurations, Payment Card Industry (PCI) compliance, and missing patches, our technical co-founder wanted to make it easier fo avoid these findings
- The existing risk visibility tools for insurance underwriters took a shallow look at Internet-facing risks. They -- along with all businesses -- need a deeper view of the threats that could actually lead to breaches.
- Domain risks
- Operating System (OS) patches
- Application patches
- Network vulnerabilities
- Cloud vulnerabilities
- OS configurations
- Axcient*
- Cloudflare
- Connectwise Screen Connect
- Datto RMM
- FreshDesk*
- Huntress
- Microsoft 365
- Panorama9
- ZenDesk
You can use your own logo for the console and notifications. You can also use a CNAME to automatically brand your console.
Note: you cannot currently re-proxy the CNAME to Lavawall® through Cloudflare.
Privacy & Security
However, we do allow passwords and use passwords as part of the zero-knowledge encryption for your clients' sensitive data, such as Bitlocker keys and Personally-Identifiable Information (PII).
These passwords use Argon2id slow hashes with individual salts and peppers.
We have added an additional secure tunnel that mimics the TLS process within the public TLS tunnel. This extra tunnel provides authentication and privacy for the workstations and the Lavawall® servers to prevent attacks such as the one that took down Solar Winds.
Remote access is not enabled for read-only and audit situations.
Get In Touch
Have a quick question and don't want to talk? Send us a quick note with the form below and we'll reply within one business day.
NW Calgary:
ThreeShield Information Security Corporation
600 Crowfoot Crescent N.W., Suite 340
Calgary, Alberta
T3G 0B4
SE Calgary:
ThreeShield Information Security Corporation
105, 11500 - 29th St. SE
Calgary, Alberta
T2Z 3W9
Canada